Think passwordless is too complicated Let’s clear that up – Talosintelligence.com
Published on: 2025-10-24
Intelligence Report: Think passwordless is too complicated Let’s clear that up – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
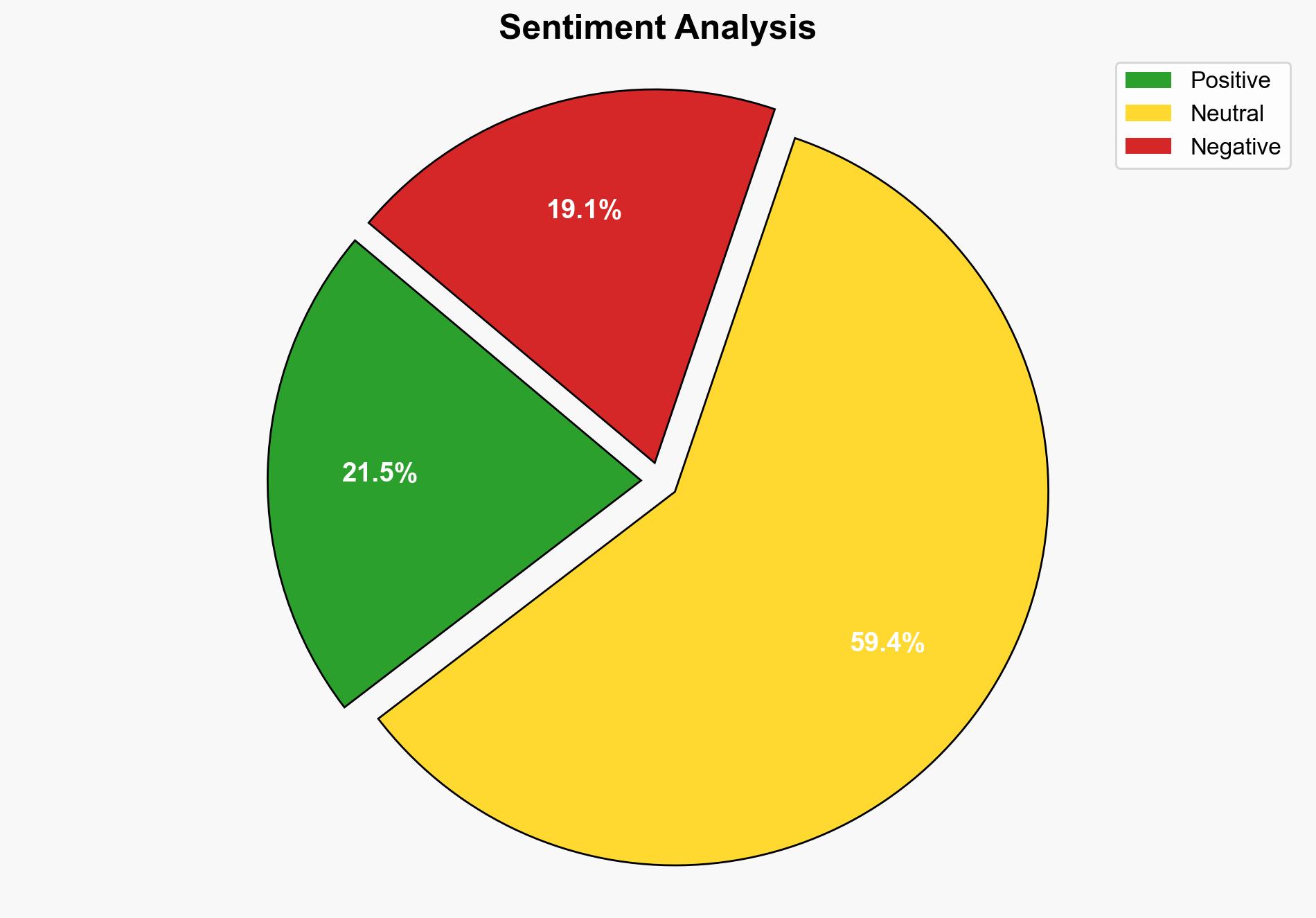
The analysis suggests a moderate confidence level in the hypothesis that the blocking issue on Talosintelligence.com is primarily due to automated security measures misidentifying legitimate access attempts as threats. The recommended action is to enhance communication with users and refine security protocols to reduce false positives while maintaining robust protection against genuine threats.
2. Competing Hypotheses
1. **Hypothesis A**: The blocking of access to Talosintelligence.com is a result of overly aggressive security protocols that misinterpret legitimate user actions as potential threats.
2. **Hypothesis B**: The blocking is intentional and part of a broader strategy to restrict access to sensitive information, possibly due to heightened security concerns or ongoing cyber threats.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported by the repetitive nature of the blocking messages and the emphasis on automated triggers, suggesting a systemic issue rather than a deliberate restriction.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the security measures in place are primarily automated and not manually configured for specific users.
– **Red Flags**: The lack of detailed information on the specific triggers for blocking raises questions about transparency and potential miscommunication.
– **Blind Spots**: The possibility that external factors, such as a coordinated cyber attack, are influencing the security protocols is not fully explored.
4. Implications and Strategic Risks
If Hypothesis A is correct, the main risk is alienating legitimate users, which could lead to reputational damage and decreased trust in the platform. Conversely, if Hypothesis B holds, there is a risk of escalating cyber threats necessitating further restrictions, impacting information dissemination and access.
5. Recommendations and Outlook
- **Mitigation**: Implement a review and refinement of security protocols to reduce false positives and improve user experience.
- **Communication**: Enhance transparency with users regarding security measures and provide clear instructions for resolving access issues.
- **Scenario Projections**:
– **Best Case**: Improved security measures lead to fewer false positives and increased user trust.
– **Worst Case**: Continued access issues result in significant user attrition and reputational harm.
– **Most Likely**: Incremental improvements in security protocols stabilize user access while maintaining protection against threats.
6. Key Individuals and Entities
No specific individuals are mentioned in the source material. The primary entity involved is Talosintelligence.com, with Cloudflare providing security services.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus