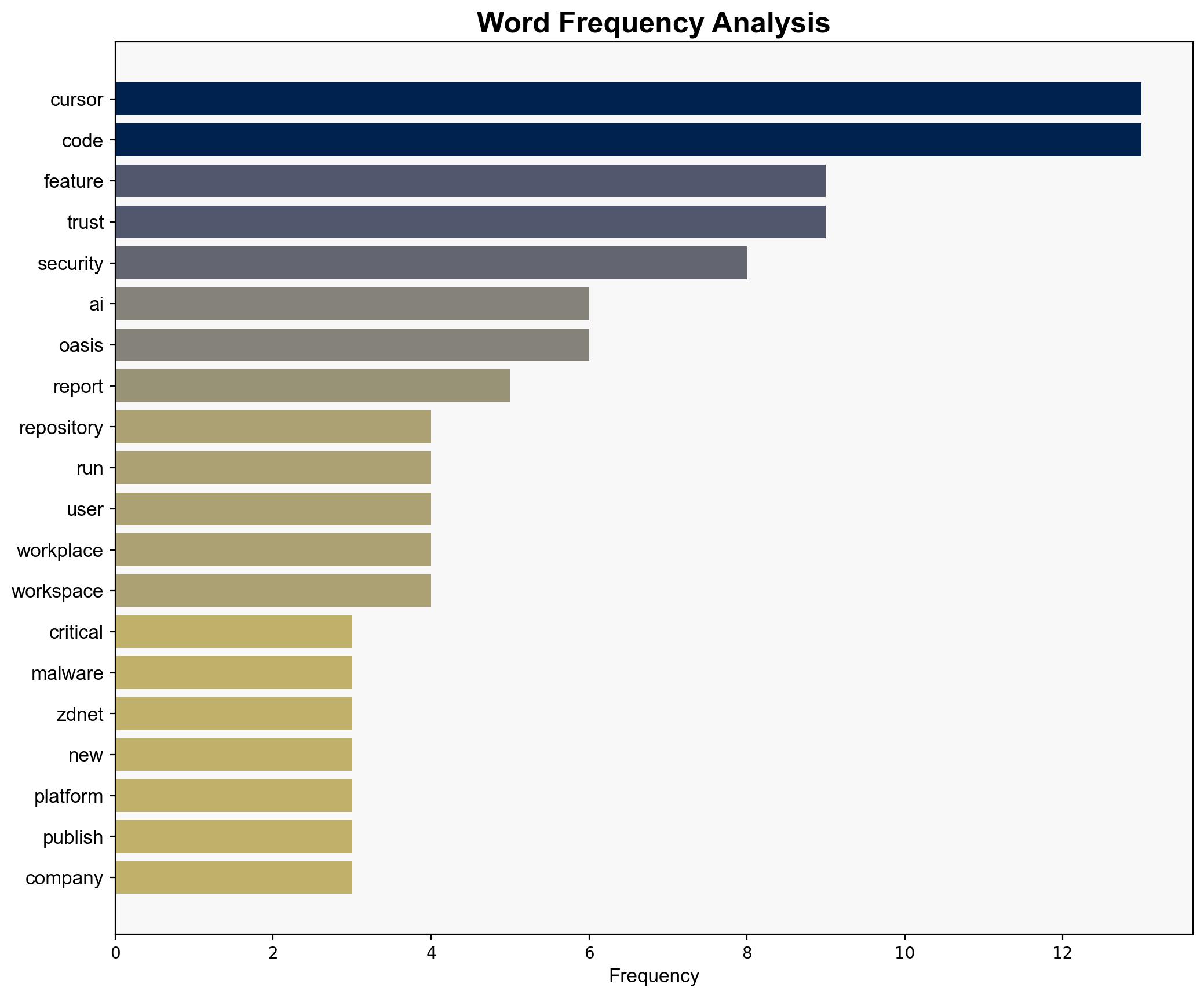
This ‘critical’ Cursor security flaw could expose your code to malware – how to fix it – ZDNet
Published on: 2025-09-12
Intelligence Report: This ‘critical’ Cursor security flaw could expose your code to malware – how to fix it – ZDNet
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the security flaw in the Cursor platform, specifically its autorun feature, poses a significant risk of malware exposure and supply chain attacks. The recommended action is to immediately enable the workspace trust feature and follow updated security guidelines. Confidence level: Moderate, due to potential undisclosed vulnerabilities and reliance on user compliance.
2. Competing Hypotheses
1. **Hypothesis A**: The autorun feature in Cursor is a critical vulnerability that hackers can exploit to embed malware, posing a significant risk to users and potentially leading to widespread supply chain attacks.
2. **Hypothesis B**: The reported vulnerability is overstated, with the risk being minimal due to existing security protocols and the ability to mitigate through user-enabled features like workspace trust.
Using ACH 2.0, Hypothesis A is better supported by the evidence of the autorun feature’s potential to automatically execute malicious code without user verification, as reported by Oasis Security. Hypothesis B lacks support due to the reliance on user action to enable security features, which may not be uniformly applied.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that users will follow security guidelines and enable the workspace trust feature. It is also assumed that the vulnerability is not already being exploited on a large scale.
– **Red Flags**: The lack of immediate comment from Cursor and potential undisclosed vulnerabilities in the platform. The reliance on user compliance for security measures is a significant blind spot.
4. Implications and Strategic Risks
The vulnerability could lead to a cascade of cyber threats, including unauthorized access to sensitive data and system compromise. The economic impact could be significant if exploited in a supply chain attack, affecting multiple organizations. Geopolitically, such vulnerabilities could be leveraged by state-sponsored actors to disrupt critical infrastructure.
5. Recommendations and Outlook
- Immediate action: Enable the workspace trust feature and adhere to updated security guidelines.
- Long-term: Develop automated security protocols that do not rely on user compliance.
- Scenario Projections:
- Best Case: Users promptly enable security features, and no significant exploitation occurs.
- Worst Case: Widespread exploitation leading to major supply chain disruptions.
- Most Likely: Some exploitation occurs, prompting further security updates and user education.
6. Key Individuals and Entities
– Oasis Security (reporting entity)
– Cursor (platform with the vulnerability)
– ZDNet (reporting source)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus