This is a political deception New Chat Control convinces lawmakers but not privacy experts yet – TechRadar
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: This is a political deception New Chat Control convinces lawmakers but not privacy experts yet – TechRadar
1. BLUF (Bottom Line Up Front)
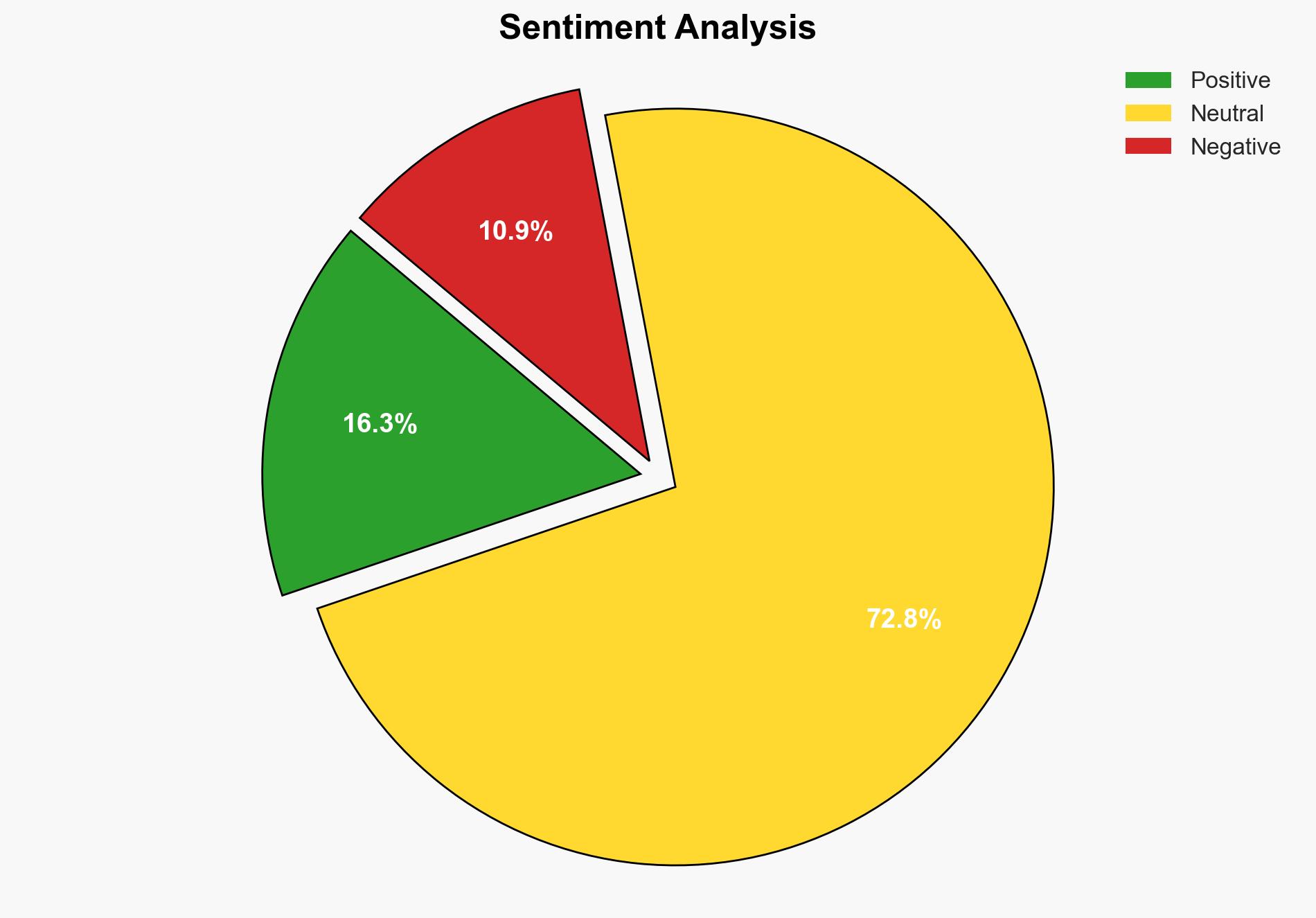
The New Chat Control proposal has garnered support from EU lawmakers but faces significant opposition from privacy experts, who view it as a potential threat to digital privacy and secure communications. The most supported hypothesis is that the proposal represents a strategic compromise to balance security and privacy, but it risks undermining encryption and privacy rights. Confidence Level: Moderate. Recommended action is to closely monitor further legislative developments and engage in advocacy for privacy-preserving amendments.
2. Competing Hypotheses
Hypothesis 1: The New Chat Control proposal is a genuine attempt to enhance security by allowing voluntary CSAM scanning, reflecting a compromise between privacy and security needs.
Hypothesis 2: The proposal is a political maneuver designed to placate privacy concerns while ultimately paving the way for more intrusive surveillance measures, potentially undermining encryption.
Hypothesis 2 is more likely given the strong opposition from privacy experts and the historical context of similar legislative efforts that have incrementally increased surveillance capabilities.
3. Key Assumptions and Red Flags
Assumptions: Lawmakers are fully informed about the technical implications of the proposal. Privacy experts’ concerns are based on a comprehensive understanding of the proposal’s potential impacts.
Red Flags: The proposal’s voluntary nature may be a facade, with future amendments potentially introducing mandatory scanning. The lack of clear definitions and safeguards for privacy rights is concerning.
Deception Indicators: The proposal’s framing as a compromise may mask intentions to erode encryption standards gradually.
4. Implications and Strategic Risks
The proposal could lead to increased surveillance capabilities, potentially setting a precedent for further erosion of digital privacy rights. This may result in public backlash, particularly in countries with strong privacy advocacy. Economically, companies providing secure communication services may face increased regulatory burdens, impacting innovation and competitiveness. Politically, the proposal could strain relationships within the EU, as member states with strong privacy laws may resist implementation.
5. Recommendations and Outlook
- Engage with policymakers to advocate for clear privacy safeguards and transparency in the implementation of the proposal.
- Monitor legislative developments and prepare for potential legal challenges to protect encryption standards.
- Best-case scenario: The proposal is amended to include robust privacy protections, maintaining encryption integrity.
- Worst-case scenario: Mandatory scanning is introduced, leading to widespread erosion of digital privacy and secure communications.
- Most-likely scenario: Incremental changes are made, with ongoing debates and adjustments to balance security and privacy concerns.
6. Key Individuals and Entities
Patrick Breyer – Digital rights jurist and critic of the proposal.
EU Council – Key legislative body involved in the proposal’s discussion and approval.
Denmark Presidency – Leading the compromise efforts within the EU Council.
7. Thematic Tags
Cybersecurity, Digital Privacy, EU Legislation, Encryption, Surveillance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology