This popular WordPress security plugin has a worrying flaw which exposed user data – TechRadar
Published on: 2025-10-30
Intelligence Report: This popular WordPress security plugin has a worrying flaw which exposed user data – TechRadar
1. BLUF (Bottom Line Up Front)
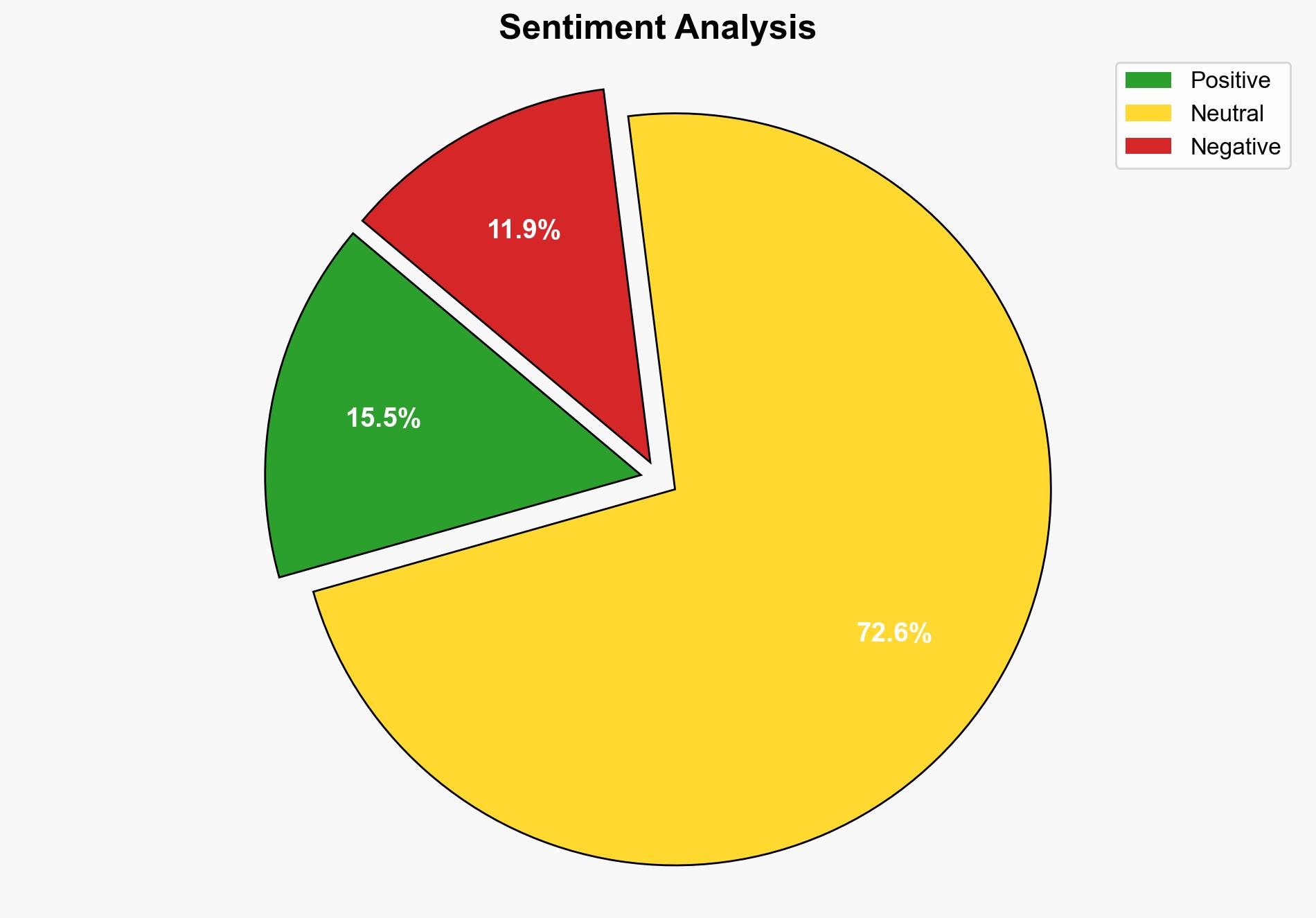
The WordPress security plugin vulnerability poses a moderate risk to user data integrity and privacy. The most supported hypothesis is that the vulnerability is primarily due to inadequate capability checks in the plugin’s code, which has been partially mitigated by a recent patch. Confidence Level: Moderate. Recommended action is to prioritize patching of affected systems and enhance monitoring for potential exploitation attempts.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is a result of a coding oversight that failed to implement proper capability checks, allowing low-privileged users to access sensitive files.
Hypothesis 2: The vulnerability may have been intentionally introduced or exploited by malicious actors to gain unauthorized access to sensitive data, leveraging the plugin’s widespread use.
Using ACH 2.0, Hypothesis 1 is better supported due to the immediate response by the vendor with a patch and the absence of evidence indicating intentional exploitation at the time of discovery.
3. Key Assumptions and Red Flags
Assumptions:
– The vendor’s patch effectively mitigates the vulnerability.
– Users will promptly update their installations.
Red Flags:
– Delay in user adoption of the patch.
– Lack of detailed information on the exploitation method.
4. Implications and Strategic Risks
The vulnerability could lead to unauthorized data access, impacting user trust and potentially leading to broader cyber threats if exploited at scale. Economic implications include potential costs for breach mitigation and reputational damage. Geopolitically, widespread exploitation could be leveraged by state actors for intelligence gathering.
5. Recommendations and Outlook
- Immediate patching of affected systems is critical.
- Enhance monitoring for signs of exploitation and unauthorized access attempts.
- Conduct a thorough code review of similar plugins to preemptively identify vulnerabilities.
- Scenario Projections:
- Best Case: Rapid patch adoption mitigates risk with no significant exploitation.
- Worst Case: Delayed patching leads to widespread data breaches and loss of user trust.
- Most Likely: Moderate exploitation occurs, but is contained through timely patching and monitoring.
6. Key Individuals and Entities
– Wordfence (Security Researcher)
– TechRadar (Reporting Source)
7. Thematic Tags
cybersecurity, data privacy, software vulnerabilities, risk management