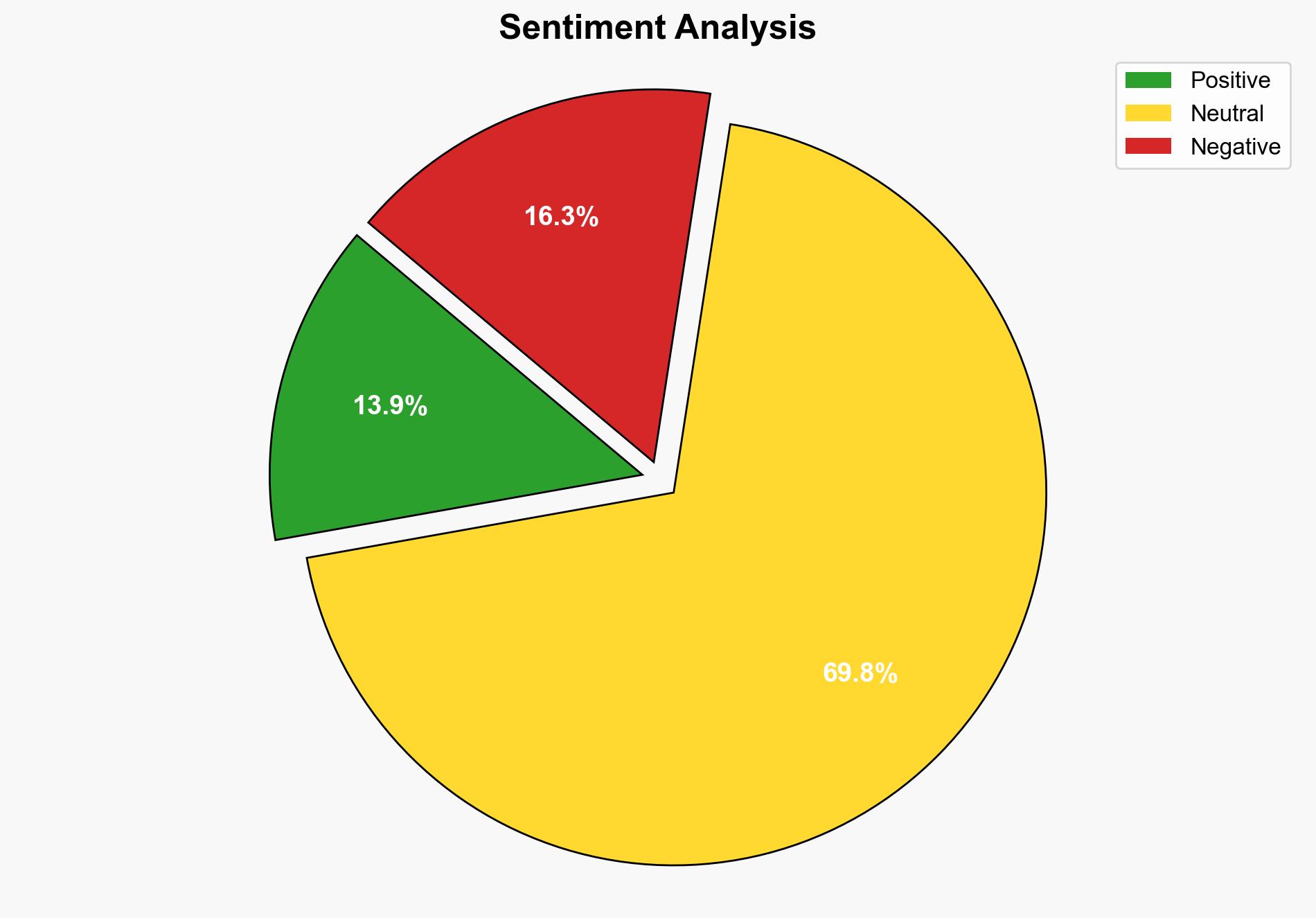
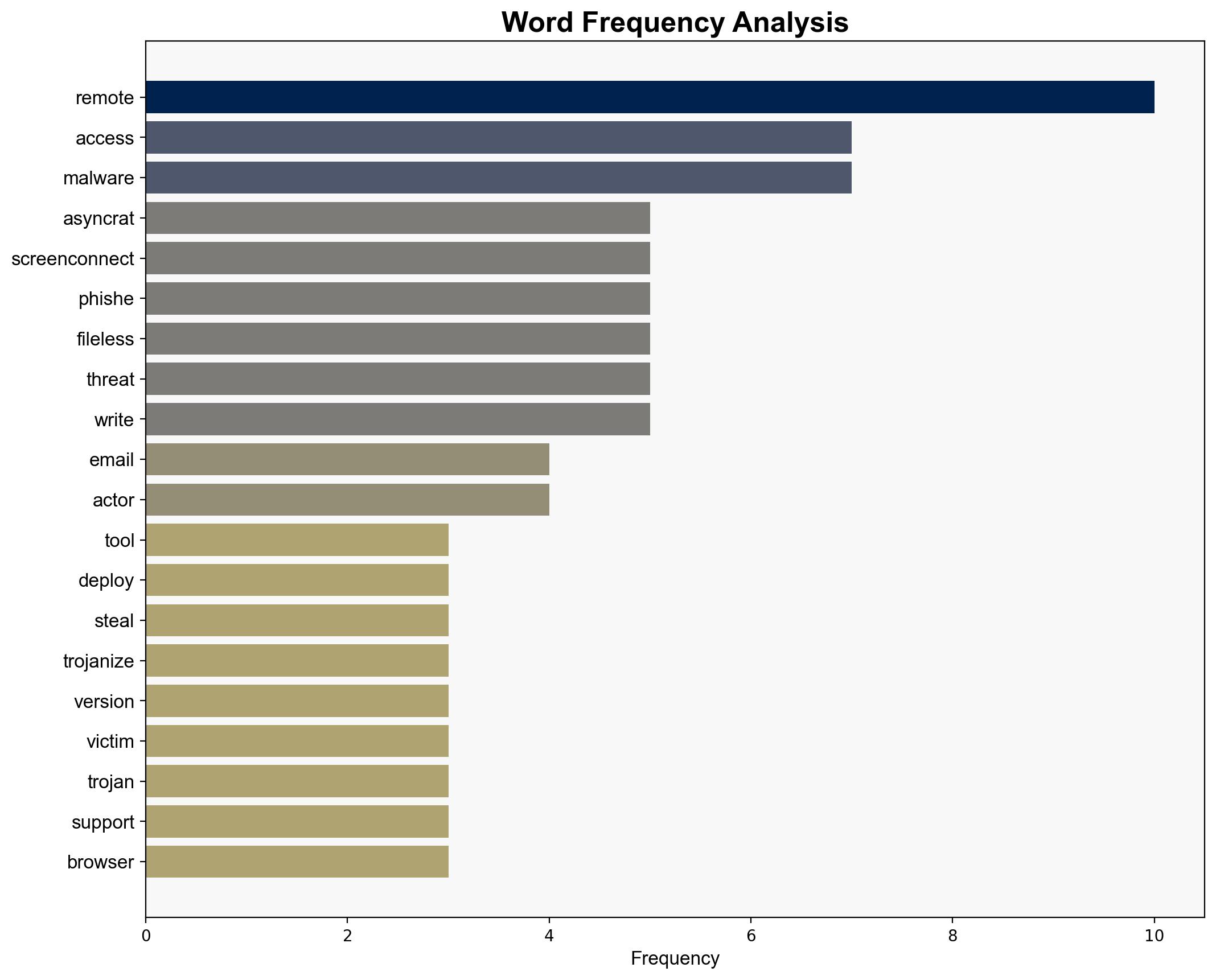
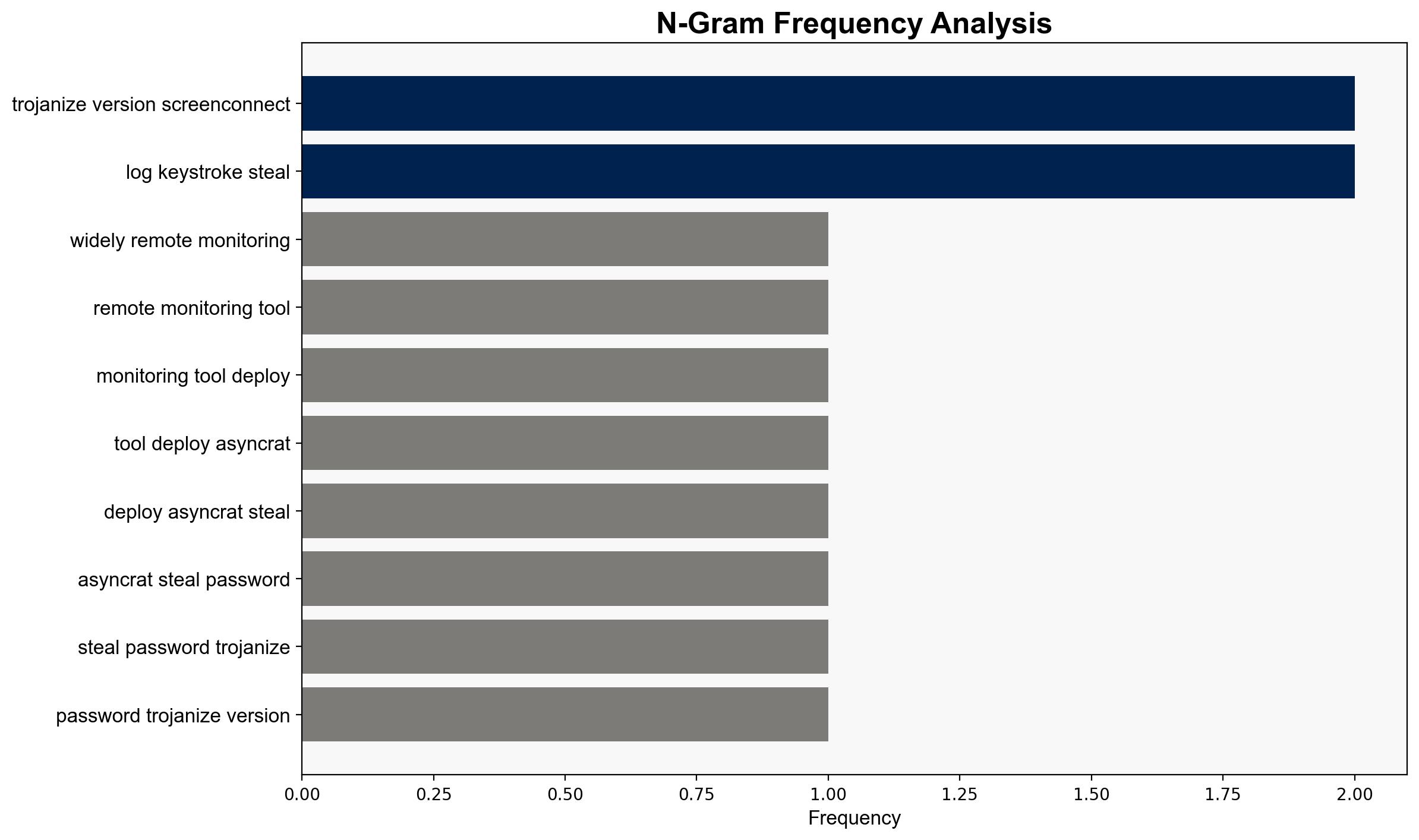
This widely used Remote Monitoring tool is being used to deploy AsyncRAT to steal passwords – TechRadar
Published on: 2025-09-11
Intelligence Report: This widely used Remote Monitoring tool is being used to deploy AsyncRAT to steal passwords – TechRadar
1. BLUF (Bottom Line Up Front)
The strategic judgment indicates a moderate confidence level that cybercriminals are exploiting legitimate remote monitoring tools to deploy AsyncRAT for credential theft. The most supported hypothesis suggests that the open-source nature of AsyncRAT and its integration with legitimate software increases its appeal and utility for diverse threat actors. Recommended action includes enhancing detection mechanisms for fileless malware and increasing awareness of phishing tactics among potential targets.
2. Competing Hypotheses
1. **Hypothesis A**: Cybercriminals are primarily leveraging the open-source nature of AsyncRAT and its integration with legitimate remote monitoring tools to conduct widespread credential theft operations.
2. **Hypothesis B**: The primary driver of these attacks is the increased sophistication and availability of phishing techniques, which are used to trick users into installing trojanized versions of legitimate software.
Using ACH 2.0, Hypothesis A is better supported due to the explicit mention of AsyncRAT’s open-source nature and its appeal to a wide range of threat actors. Hypothesis B is plausible but less supported by the direct evidence provided.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Threat actors prefer open-source tools for their flexibility and adaptability.
– Users are generally unaware of the risks associated with phishing and trojanized software.
– **Red Flags**:
– Lack of specific attribution to a particular group or actor, suggesting potential gaps in intelligence.
– The assumption that all users of the legitimate software are equally vulnerable without considering varying levels of cybersecurity awareness.
– **Blind Spots**:
– The potential for insider threats or compromised supply chains is not addressed.
4. Implications and Strategic Risks
The integration of AsyncRAT with legitimate tools poses significant cybersecurity risks, particularly in sectors reliant on remote access solutions. This could lead to increased incidents of identity theft, financial fraud, and unauthorized data access. The continued evolution of phishing techniques may exacerbate these risks, leading to broader economic and reputational damage for affected organizations. The potential for geopolitical exploitation exists if state actors leverage these tools for espionage.
5. Recommendations and Outlook
- Enhance cybersecurity training focused on phishing awareness and detection.
- Implement advanced monitoring solutions to detect fileless malware activity.
- Encourage collaboration between cybersecurity firms and software developers to identify and mitigate vulnerabilities in legitimate tools.
- Scenario Projections:
- Best Case: Increased awareness and improved detection reduce successful attacks.
- Worst Case: Widespread adoption of these techniques leads to significant data breaches and financial losses.
- Most Likely: Continued sporadic attacks with moderate impact, prompting gradual improvements in cybersecurity measures.
6. Key Individuals and Entities
– AsyncRAT developers (open-source contributors)
– ConnectWise (developer of ScreenConnect)
– LevelBlue (security researchers)
– Sead Fadilpašić (journalist reporting on the issue)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus