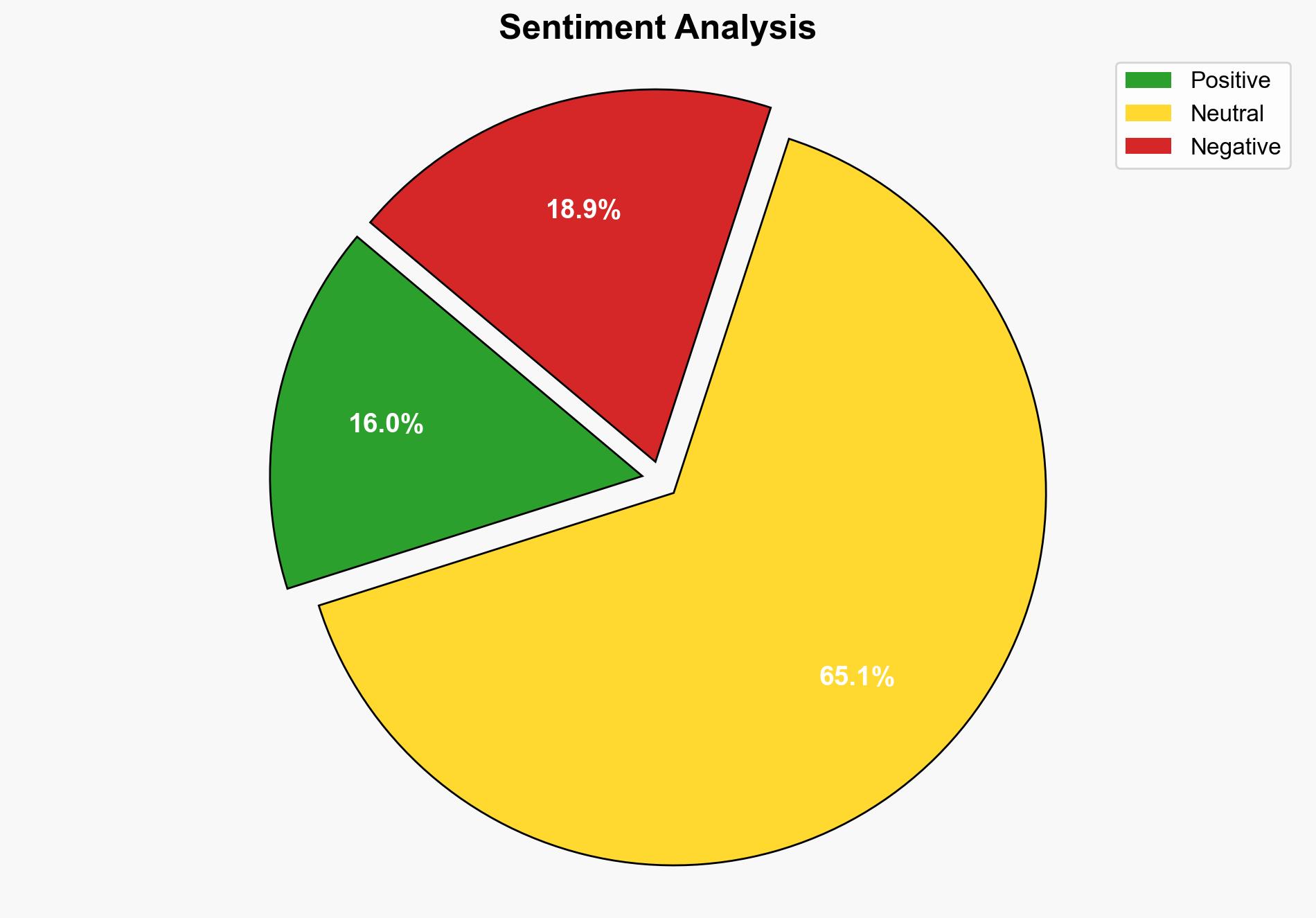
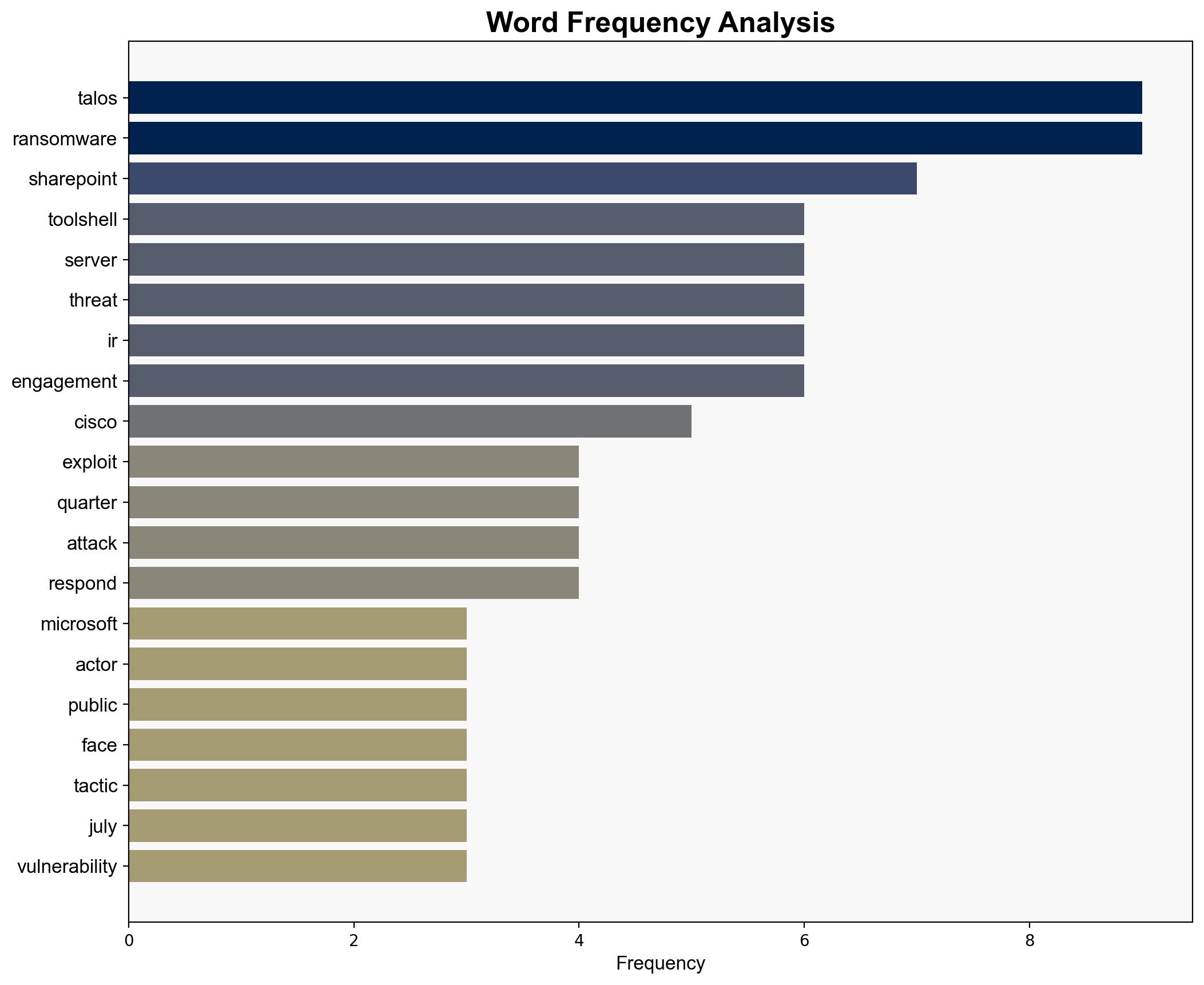
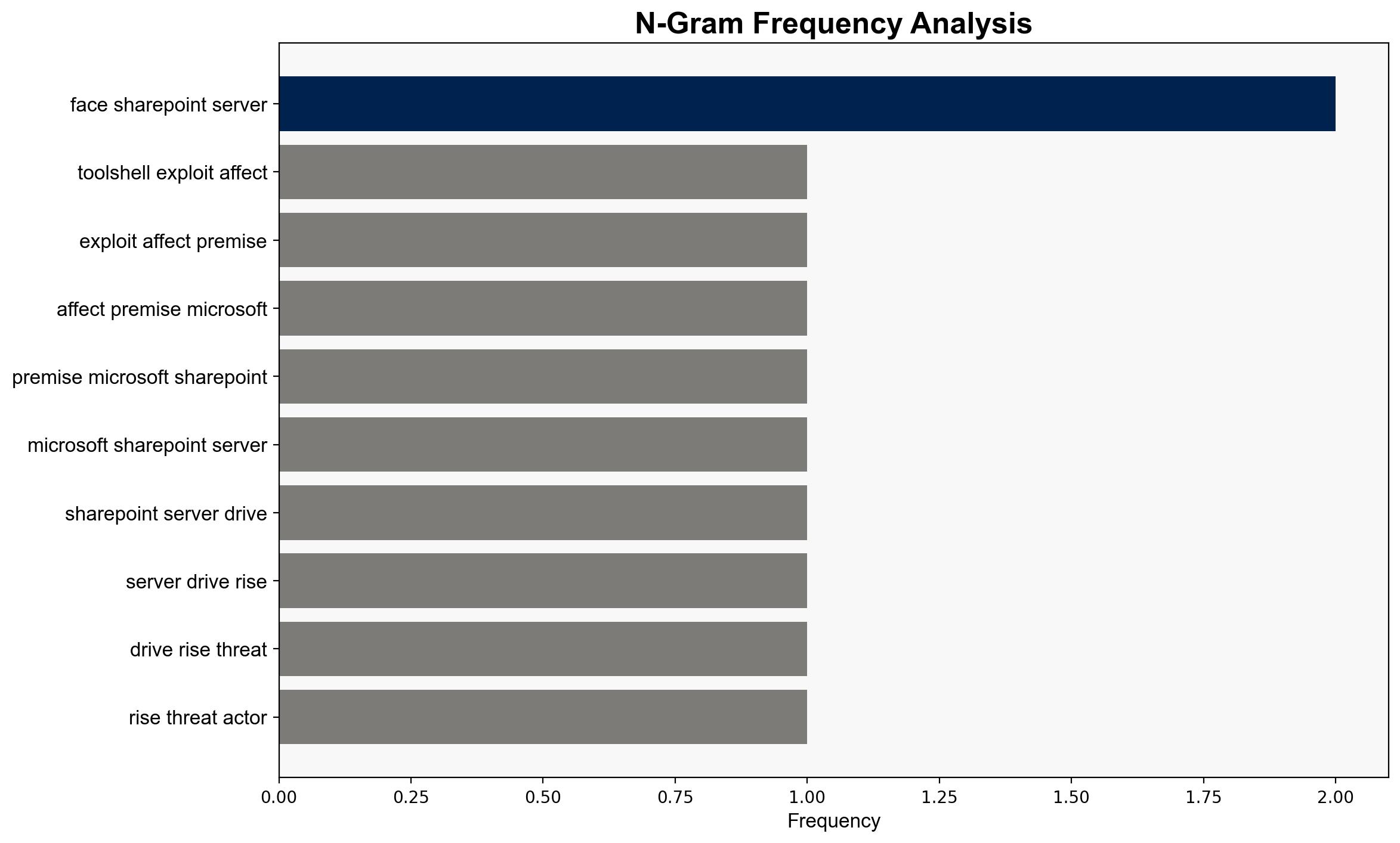
Threat Actors Ramp Up Public App Exploits as ToolShell Gains Traction – Infosecurity Magazine
Published on: 2025-10-24
Intelligence Report: Threat Actors Ramp Up Public App Exploits as ToolShell Gains Traction – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that Chinese-based threat groups are strategically exploiting vulnerabilities in Microsoft SharePoint servers to gain initial access to sensitive networks, with a moderate confidence level. Immediate action is recommended to enhance network segmentation and patch management to mitigate these threats.
2. Competing Hypotheses
Hypothesis 1: Chinese-based threat groups, such as Linen Typhoon and Violet Typhoon, are conducting a coordinated campaign to exploit SharePoint vulnerabilities for strategic access to government, defense, and academic networks. This is supported by the timing of the attacks and the specific targeting of high-value sectors.
Hypothesis 2: The rise in ToolShell exploits is primarily opportunistic, driven by various independent threat actors capitalizing on publicly disclosed vulnerabilities, rather than a coordinated campaign by specific groups. This is suggested by the broad range of affected sectors and the general increase in ransomware incidents.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the alignment of observed tactics, techniques, and procedures (TTPs) with known Chinese threat actor patterns and the strategic nature of the targeted sectors.
3. Key Assumptions and Red Flags
– Assumption: The attribution to Chinese-based groups is accurate based on TTPs and previous patterns.
– Red Flag: The possibility of false flag operations by other actors to mislead attribution efforts.
– Blind Spot: Limited visibility into non-public sector targets and potential underreporting of incidents.
4. Implications and Strategic Risks
The exploitation of SharePoint vulnerabilities poses significant risks to national security and critical infrastructure. Successful breaches could lead to data exfiltration, intellectual property theft, and potential disruption of critical services. The persistent threat of ransomware further exacerbates these risks, potentially leading to financial and reputational damage.
5. Recommendations and Outlook
- Enhance network segmentation and implement robust patch management protocols to mitigate vulnerability exploitation.
- Conduct regular threat intelligence sharing among affected sectors to improve collective defense mechanisms.
- Scenario Projections:
- Best Case: Rapid patch deployment and improved defenses reduce successful exploitations.
- Worst Case: Continued exploitation leads to significant breaches and operational disruptions.
- Most Likely: Incremental improvements in defenses lead to a gradual decline in successful attacks.
6. Key Individuals and Entities
– Linen Typhoon
– Violet Typhoon
– Cisco Talos
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus