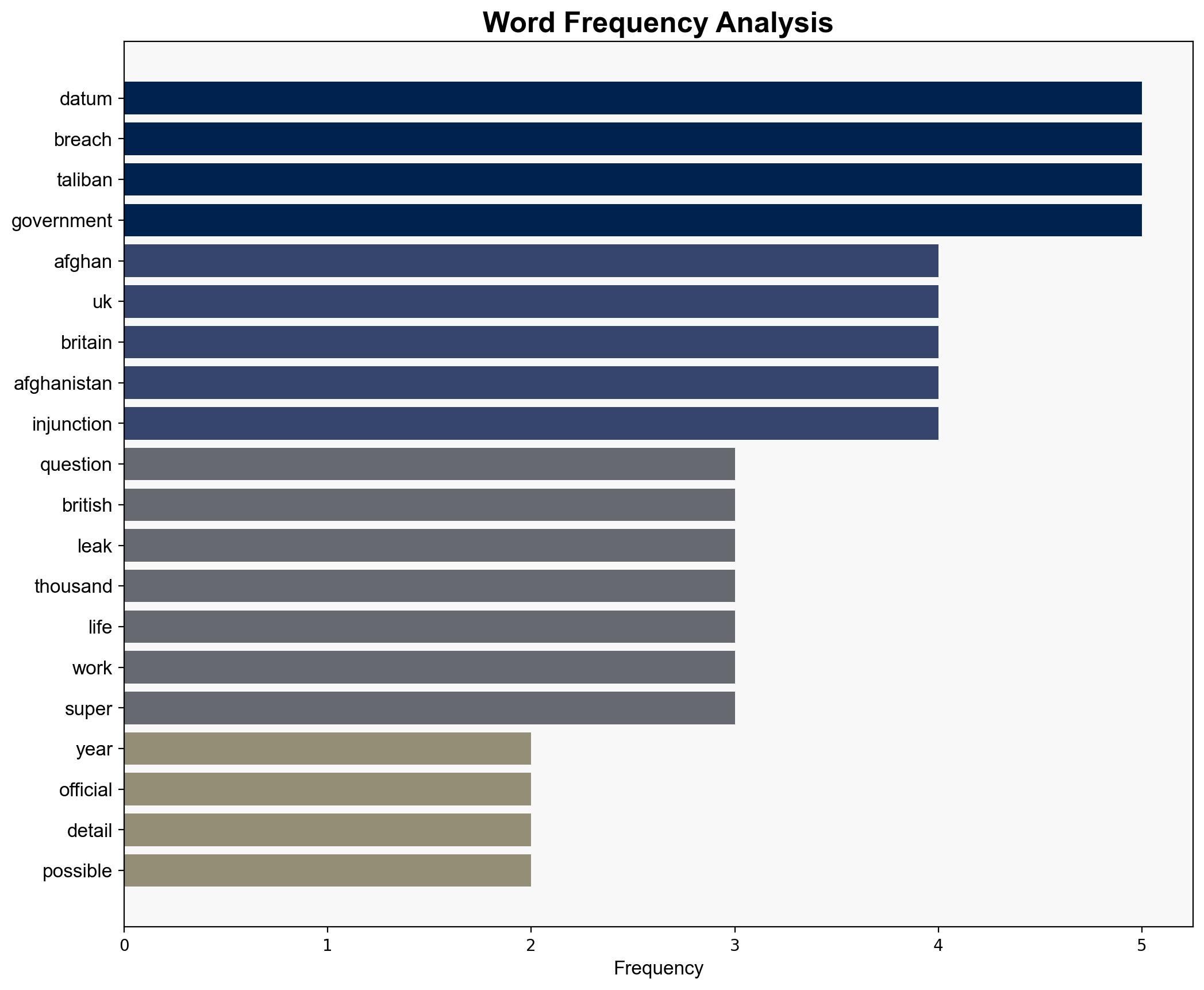
Three key questions after Afghan data leak sparked unprecedented secret evacuation – BBC News
Published on: 2025-07-15
Intelligence Report: Three Key Questions After Afghan Data Leak Sparked Unprecedented Secret Evacuation
1. BLUF (Bottom Line Up Front)
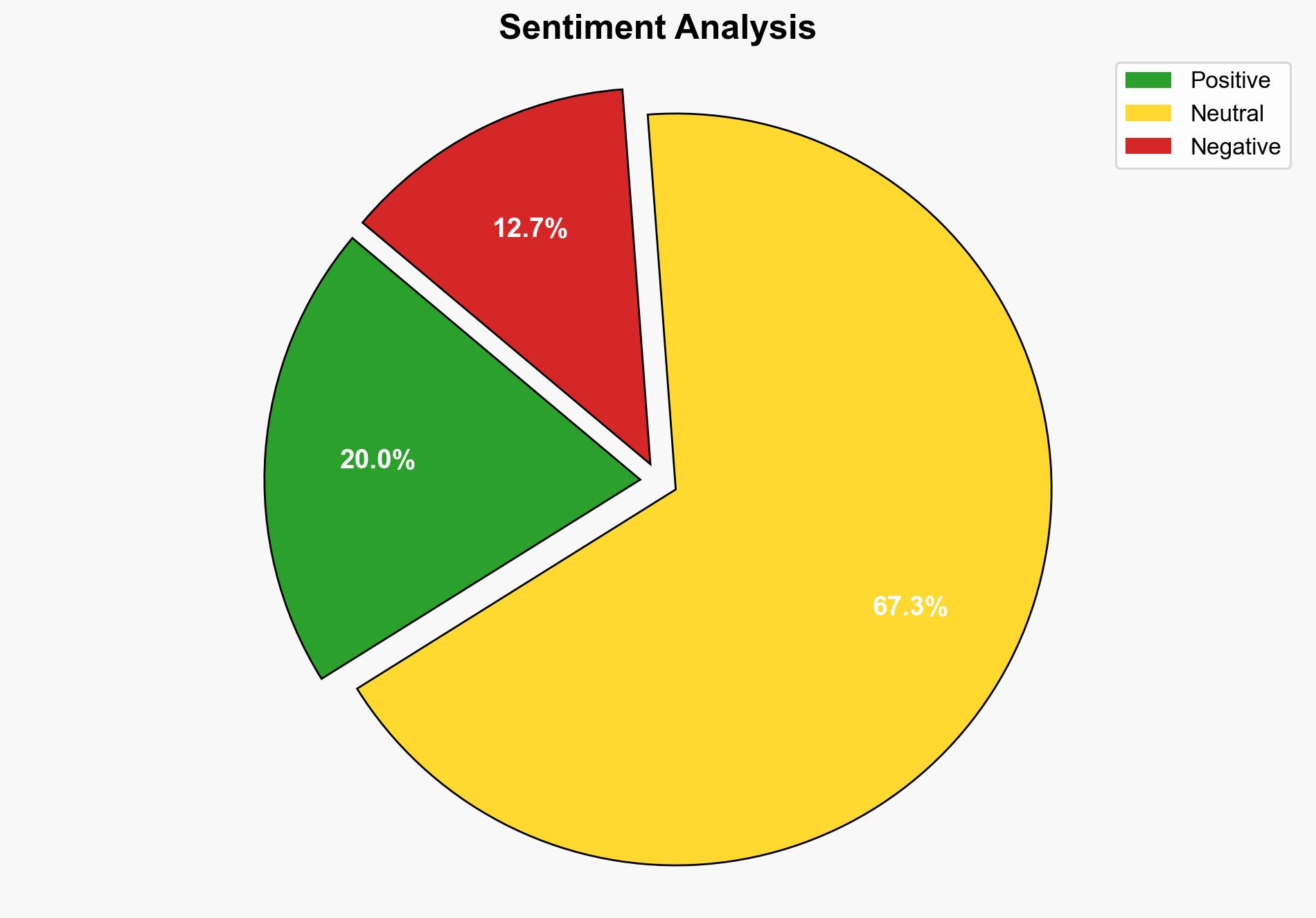
The inadvertent leak of sensitive Afghan data by British officials has led to a secret evacuation operation, highlighting critical vulnerabilities in data security protocols. This incident underscores the importance of robust cybersecurity measures and the potential geopolitical ramifications of data breaches. Immediate actions are required to address these vulnerabilities and ensure the safety of affected individuals.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Analyzed the intentions behind potential threat actors, emphasizing the need for enhanced data protection to prevent similar breaches. The analysis suggests a combination of human error and inadequate security protocols as contributing factors.
Indicators Development
Monitored potential retaliatory actions by the Taliban, including digital radicalization and propaganda efforts, which could exploit the breach to incite further violence or recruitment.
Narrative Pattern Analysis
Evaluated the dissemination of ideological narratives that could leverage the breach to undermine trust in Western allies, potentially affecting future cooperation with local forces in conflict zones.
3. Implications and Strategic Risks
The data leak presents significant risks, including heightened threats to individuals named in the dataset and potential diplomatic strains between the UK and Afghanistan. The breach may embolden cyber actors to exploit similar vulnerabilities, increasing the likelihood of future attacks. Additionally, the incident could undermine trust in international partnerships, affecting ongoing and future operations.
4. Recommendations and Outlook
- Enhance cybersecurity protocols and conduct regular audits to prevent unauthorized data access.
- Implement comprehensive training programs for personnel handling sensitive information to reduce human error.
- Develop contingency plans for rapid response to data breaches, including secure communication channels for affected individuals.
- Scenario-based projections:
- Best case: Strengthened cybersecurity measures prevent future breaches, restoring trust and cooperation.
- Worst case: Continued vulnerabilities lead to further breaches, escalating threats to individuals and diplomatic relations.
- Most likely: Incremental improvements in security reduce breach frequency, but challenges persist due to evolving cyber threats.
5. Key Individuals and Entities
The report does not specify individuals by name due to the sensitive nature of the information and ongoing security concerns.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus