Three Ukrainians Detained in Poland for Possessing Hacking Tools Linked to Potential Cyberattacks
Published on: 2025-12-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 3 Ukrainian saboteurs ARRESTED in Poland over hacking equipment
1. BLUF (Bottom Line Up Front)
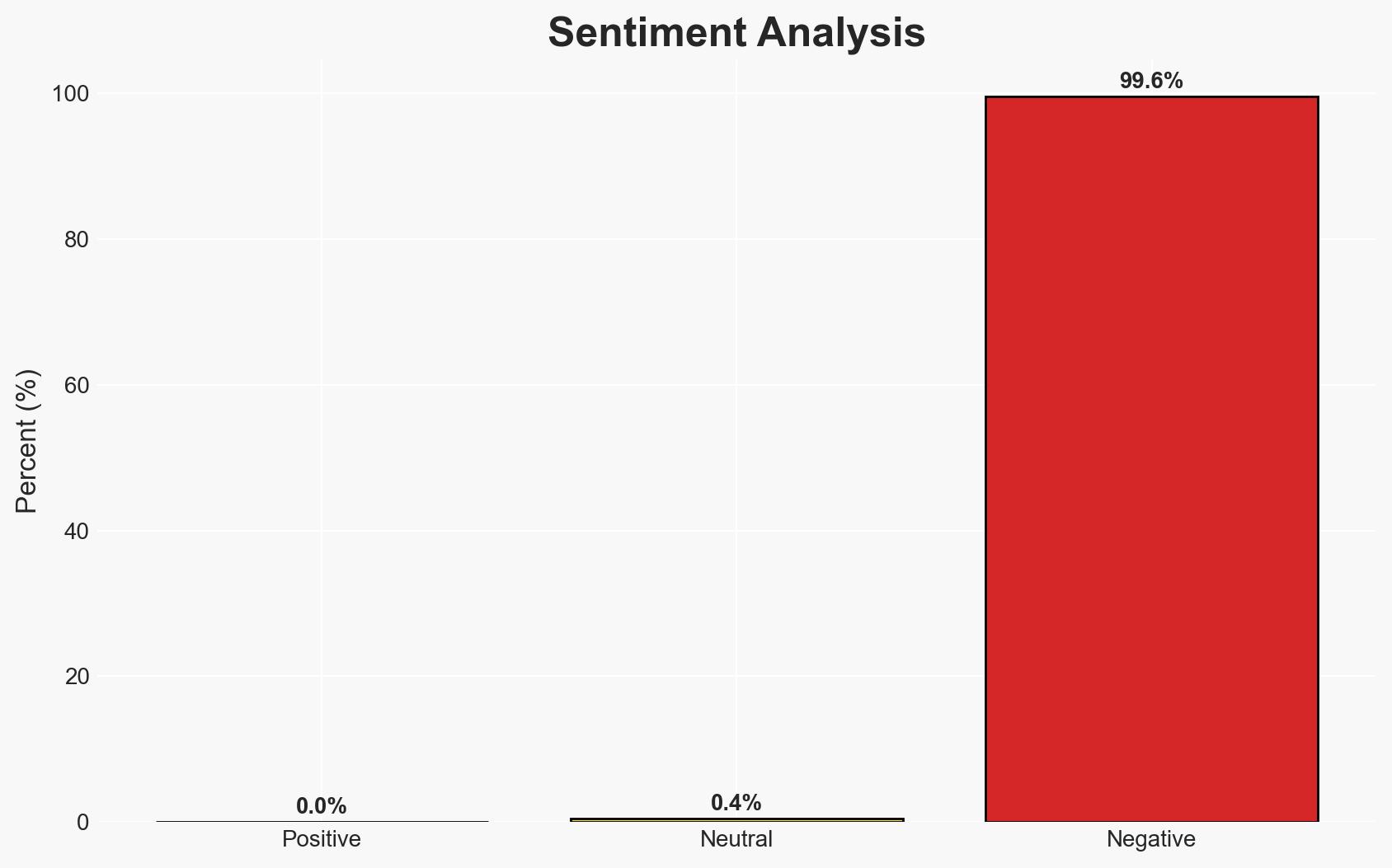
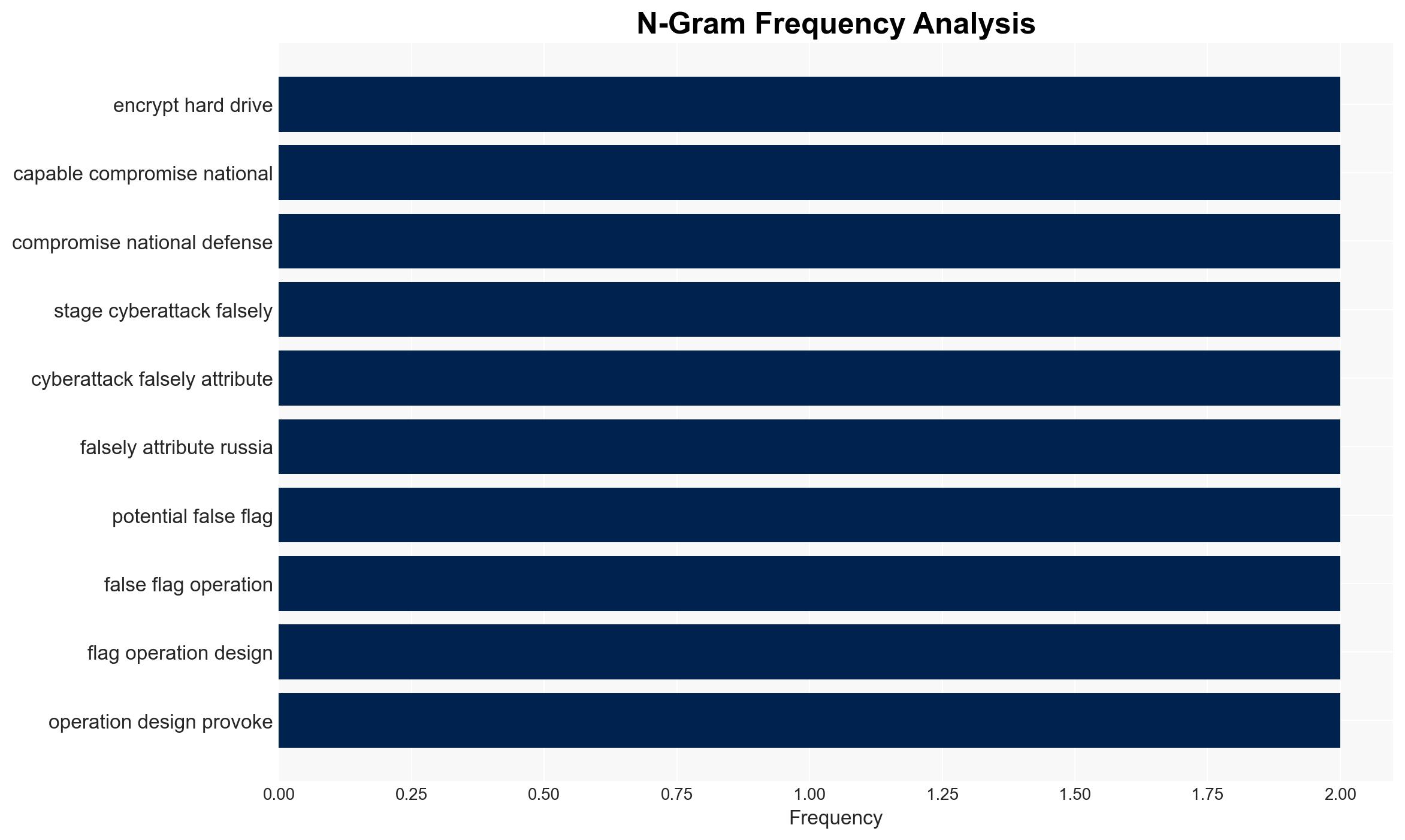
The arrest of three Ukrainian nationals in Poland with advanced hacking equipment suggests a potential false flag operation aimed at implicating Russia and provoking NATO under Article Five. This incident highlights the risk of escalating hybrid warfare tactics in Eastern Europe. The most likely hypothesis is that these individuals were part of a Russian-backed operation exploiting Ukrainian nationals for deniable actions. Overall confidence in this assessment is moderate due to existing information gaps and potential deception risks.
2. Competing Hypotheses
- Hypothesis A: The arrested individuals are part of a Russian-backed operation using Ukrainian nationals to conduct false flag cyberattacks to destabilize NATO and provoke a military response. Supporting evidence includes the possession of sophisticated hacking tools and a pattern of similar sabotage activities linked to Russian interests. Key uncertainties involve the direct connection to Russian intelligence and the operational scope.
- Hypothesis B: The individuals acted independently or as part of a non-state criminal network exploiting geopolitical tensions for financial gain. This hypothesis is supported by the lack of direct evidence tying them to Russian state actors and their claim of being IT specialists. Contradicting evidence includes the strategic nature of their tools and the broader pattern of sabotage.
- Assessment: Hypothesis A is currently better supported due to the strategic implications of the tools found and the historical context of Russian hybrid warfare tactics. Indicators that could shift this judgment include credible intelligence linking the suspects to non-state actors or financial motivations.
3. Key Assumptions and Red Flags
- Assumptions: The suspects were knowingly participating in a state-backed operation; the equipment was intended for use in false flag operations; Russia has a strategic interest in destabilizing NATO’s eastern flank.
- Information Gaps: Direct evidence of communication between the suspects and Russian intelligence; the full extent of the operational network in the Baltic region; motivations of the suspects.
- Bias & Deception Risks: Confirmation bias towards attributing actions to state actors; potential for disinformation campaigns to mislead investigations; reliance on sources with vested interests in framing Russia.
4. Implications and Strategic Risks
This development could exacerbate tensions between NATO and Russia, potentially leading to increased military readiness and diplomatic strain. It may also embolden further hybrid warfare tactics in the region.
- Political / Geopolitical: Potential escalation of NATO-Russia tensions; increased pressure on NATO to respond to perceived threats.
- Security / Counter-Terrorism: Heightened alert for similar sabotage activities; increased security measures in Poland and neighboring countries.
- Cyber / Information Space: Potential for increased cyberattacks on critical infrastructure; misinformation campaigns to obscure true perpetrators.
- Economic / Social: Possible economic impact from disrupted infrastructure; increased public anxiety and distrust in government capabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cyber activities in the region; increase intelligence sharing among NATO allies; conduct a thorough forensic analysis of seized equipment.
- Medium-Term Posture (1–12 months): Strengthen regional cybersecurity infrastructure; develop resilience measures against hybrid threats; foster partnerships with Baltic states for coordinated defense strategies.
- Scenario Outlook:
- Best: Successful disruption of the operational network, leading to reduced hybrid threats.
- Worst: Escalation into direct military confrontation due to misattributed cyberattacks.
- Most-Likely: Continued low-intensity hybrid warfare with periodic provocations and cyber incidents.
6. Key Individuals and Entities
- Yevhenii Ivanov
- Oleksandr Kononov
- Polish Prime Minister Donald Tusk
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, counter-terrorism, hybrid warfare, cyber-espionage, NATO, false flag operations, Eastern Europe security, Russian intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us