Top file transfer tool CrushFTP says a thousand servers are still vulnerable to cyberattack so patch now – TechRadar
Published on: 2025-07-22
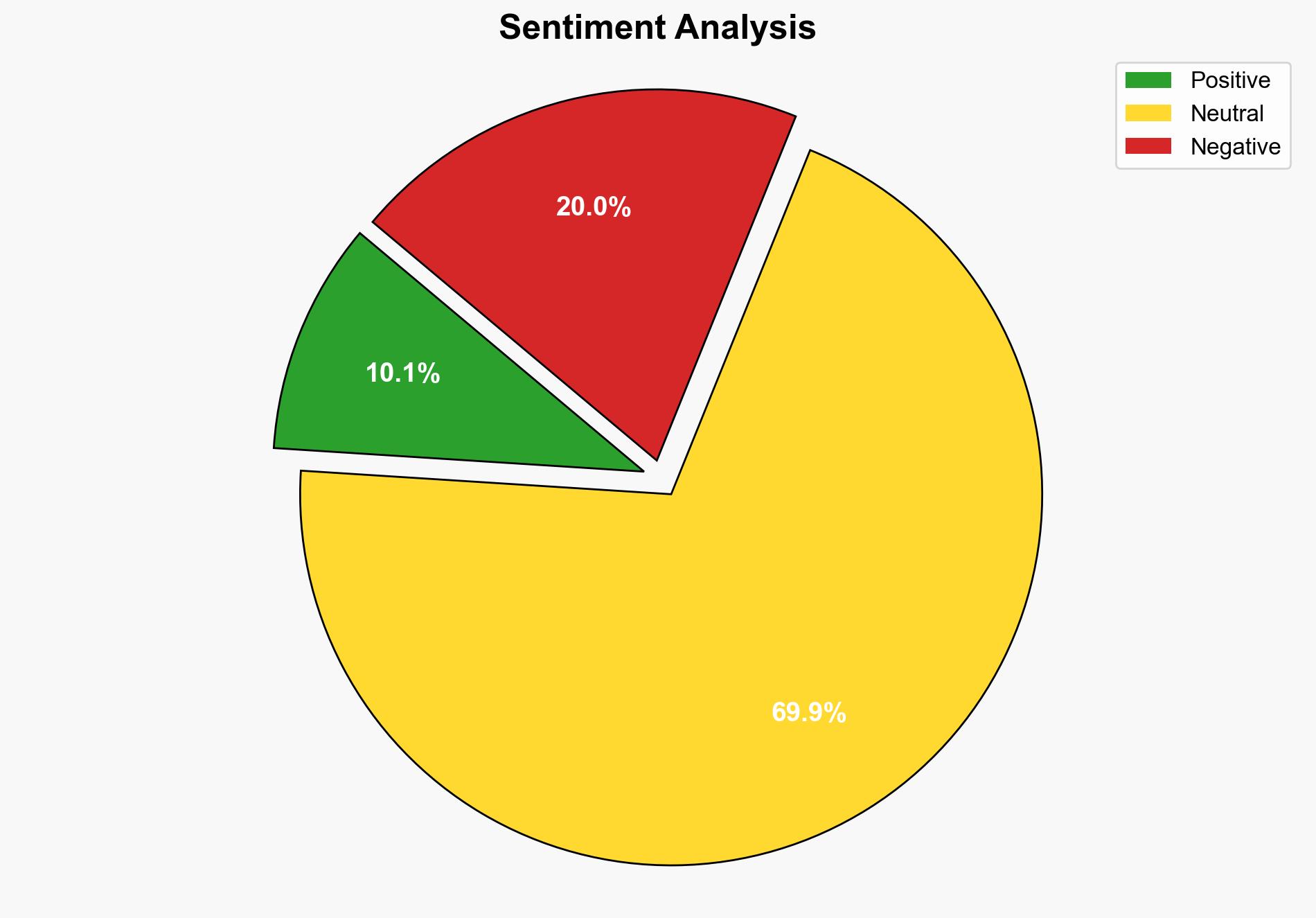
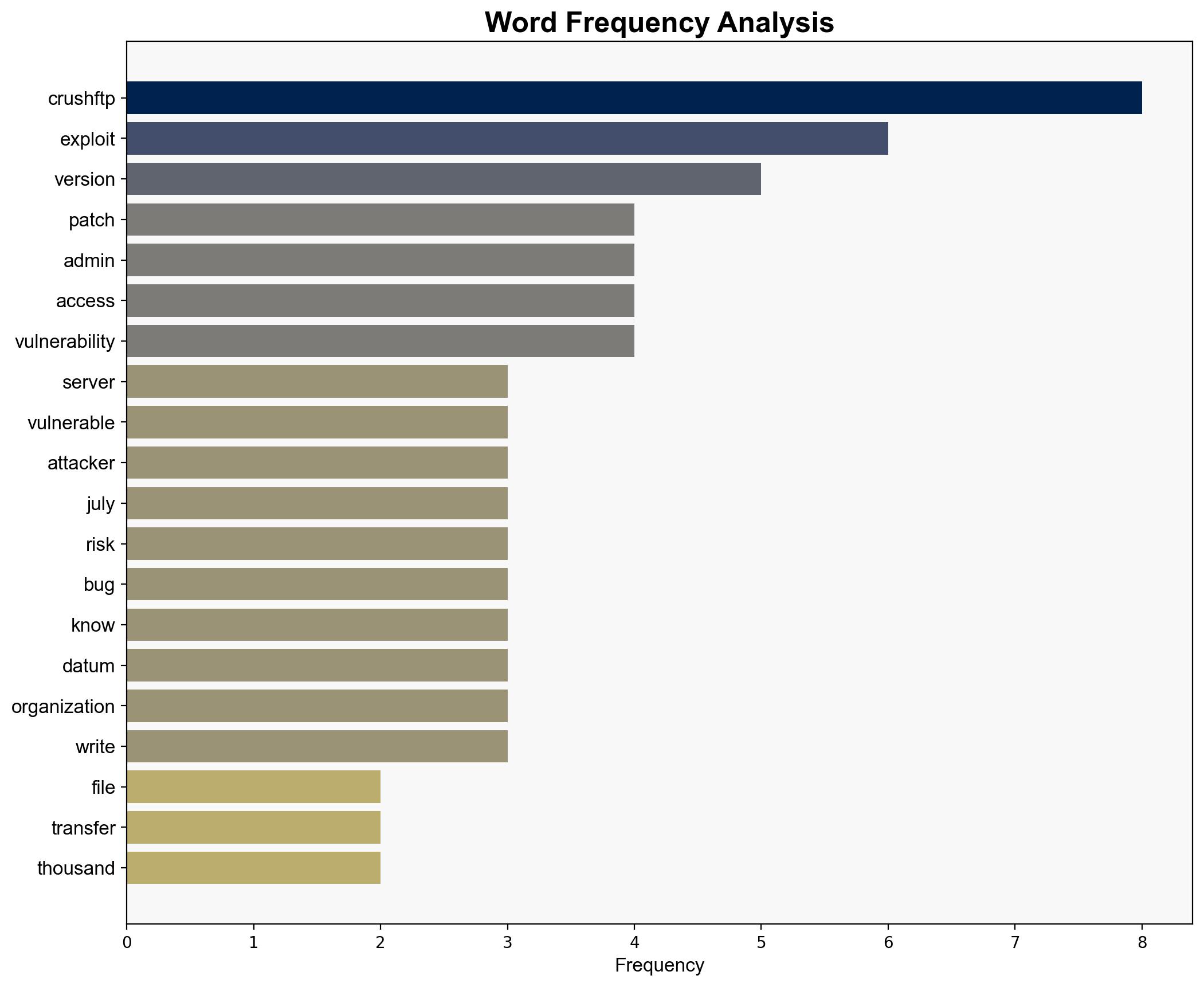
Intelligence Report: Top File Transfer Tool CrushFTP Vulnerabilities
1. BLUF (Bottom Line Up Front)
Thousands of servers running outdated versions of CrushFTP are vulnerable to cyberattacks due to a critical flaw that grants attackers administrative access. Immediate patching is essential to mitigate potential exploitation. This report employs structured analytic techniques to provide a comprehensive assessment and actionable recommendations.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated adversarial actions reveal that attackers can exploit the vulnerability to gain unauthorized access, potentially leading to data breaches and malware deployment.
Indicators Development
Monitoring for unusual access patterns and unauthorized administrative actions can serve as early indicators of exploitation attempts.
Bayesian Scenario Modeling
Probabilistic modeling suggests a high likelihood of continued exploitation if patches are not applied, with potential pathways leading to significant data compromise.
3. Implications and Strategic Risks
The vulnerability poses a significant risk to organizations relying on CrushFTP for secure file transfers. Exploitation could lead to data breaches, financial losses, and reputational damage. The widespread nature of the vulnerability increases the risk of systemic impact across sectors.
4. Recommendations and Outlook
- Immediate patching of all CrushFTP instances to the latest version is critical to prevent exploitation.
- Implement continuous monitoring for signs of unauthorized access.
- Develop a response plan for potential breaches, including data recovery and communication strategies.
- Scenario-based projections:
- Best Case: All systems patched promptly, minimizing exploitation risk.
- Worst Case: Delayed patching leads to widespread data breaches and financial losses.
- Most Likely: Mixed response with some organizations patching promptly while others remain vulnerable.
5. Key Individuals and Entities
Sead (journalist), Shadowserver Organization (notified potential risks).
6. Thematic Tags
cybersecurity, data breach, vulnerability management, risk mitigation