Transitioning from RC4 to AES-SHA1: Enhancing Security in Windows Authentication by 2026
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Beyond RC4 for Windows Authentication
1. BLUF (Bottom Line Up Front)
The transition from RC4 to AES-SHA1 encryption in Windows authentication is a critical security enhancement to mitigate credential theft risks. Organizations must identify and address legacy RC4 dependencies before mid-2026 to avoid service disruptions. This shift will primarily affect IT departments managing Windows Server environments. Overall confidence in this assessment is moderate due to potential unknowns in legacy system dependencies.
2. Competing Hypotheses
- Hypothesis A: The deprecation of RC4 will lead to a seamless transition to AES-SHA1, enhancing security without significant disruptions. This is supported by the availability of tools to identify RC4 usage and the default inclusion of AES-SHA1 in supported Windows versions. However, uncertainties remain regarding the readiness of all organizations to implement these changes.
- Hypothesis B: The transition will cause significant disruptions due to widespread legacy dependencies on RC4, particularly in environments with non-Windows devices or outdated applications. This is supported by the continued need for RC4 in certain interoperability scenarios, but lacks comprehensive data on the extent of these dependencies.
- Assessment: Hypothesis A is currently better supported due to proactive measures and tools provided by Microsoft to facilitate the transition. Key indicators that could shift this judgment include reports of widespread service disruptions or new vulnerabilities in AES-SHA1.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the technical capability to implement the transition; AES-SHA1 is sufficiently secure against current threat vectors; Microsoft will continue to support transition efforts.
- Information Gaps: The extent of RC4 dependency across different sectors; the readiness of organizations to transition; potential vulnerabilities in AES-SHA1.
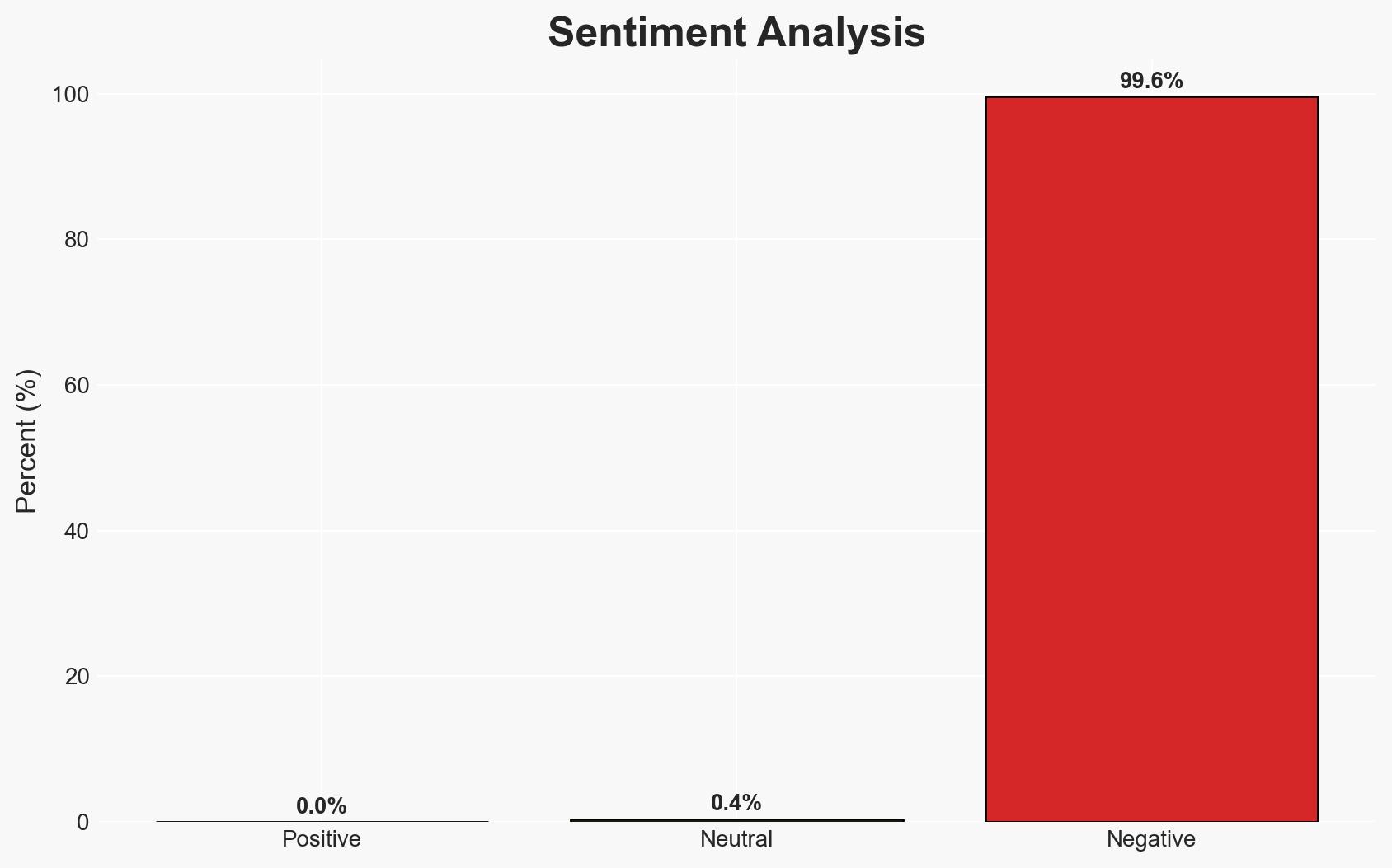
- Bias & Deception Risks: Confirmation bias in assuming all organizations will transition smoothly; potential underreporting of transition challenges by organizations.
4. Implications and Strategic Risks
The transition from RC4 to AES-SHA1 could have significant implications across various domains, particularly if not managed effectively.
- Political / Geopolitical: Limited direct implications, but potential for increased scrutiny on cybersecurity practices in critical infrastructure sectors.
- Security / Counter-Terrorism: Enhanced security posture against credential theft, reducing vulnerabilities to cyber-attacks.
- Cyber / Information Space: Potential for increased cyber incidents if transition is mishandled, leading to temporary vulnerabilities.
- Economic / Social: Disruptions in services could impact economic activities, particularly in sectors heavily reliant on legacy systems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of current encryption usage; prioritize remediation of RC4 dependencies; utilize Microsoft tools for transition support.
- Medium-Term Posture (1–12 months): Develop resilience strategies for potential disruptions; engage in partnerships for shared best practices; invest in cybersecurity training for IT staff.
- Scenario Outlook:
- Best: Seamless transition with enhanced security and minimal disruptions.
- Worst: Significant service disruptions and vulnerabilities due to unaddressed RC4 dependencies.
- Most-Likely: Gradual transition with manageable disruptions and improved security posture.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
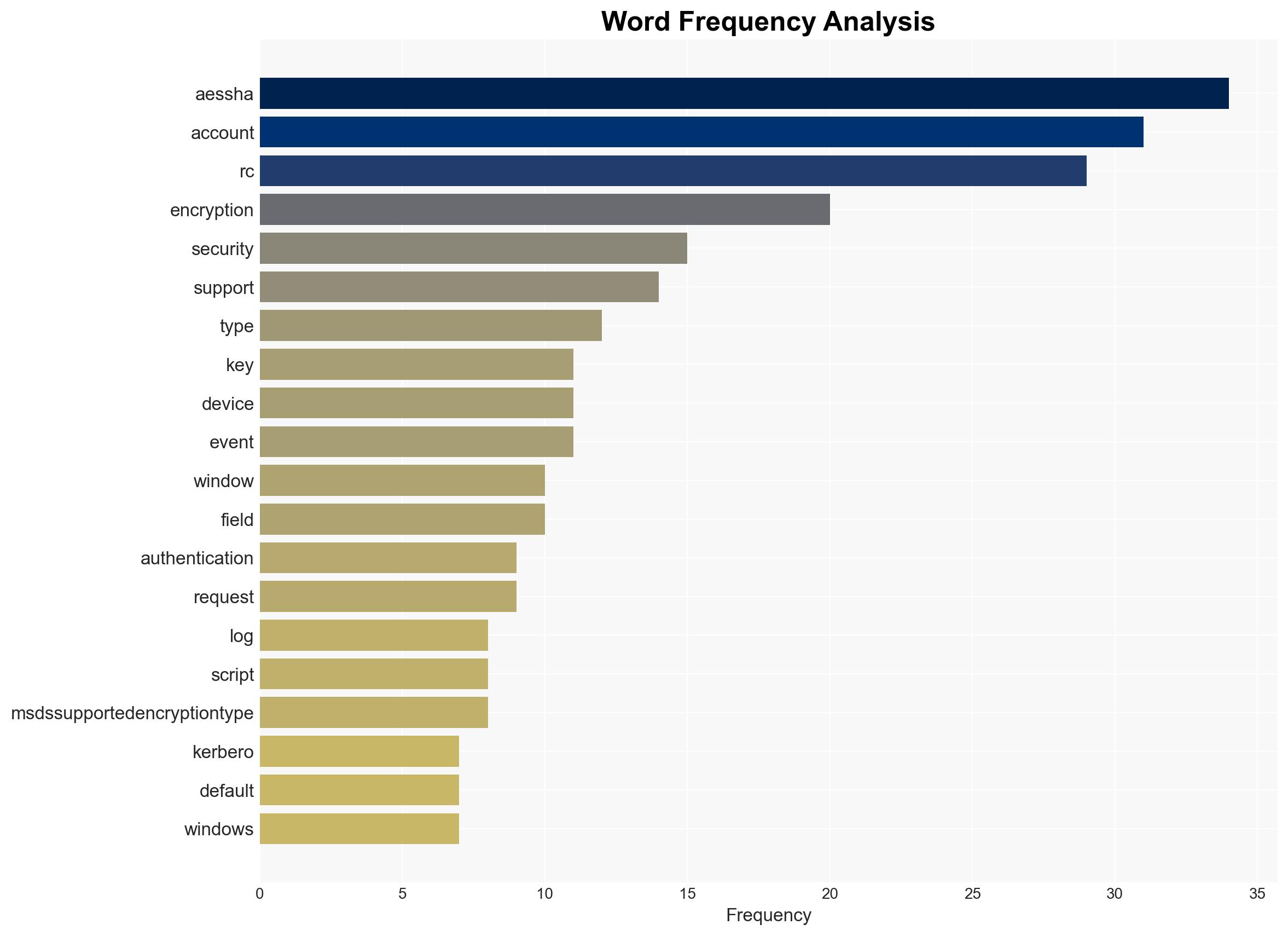
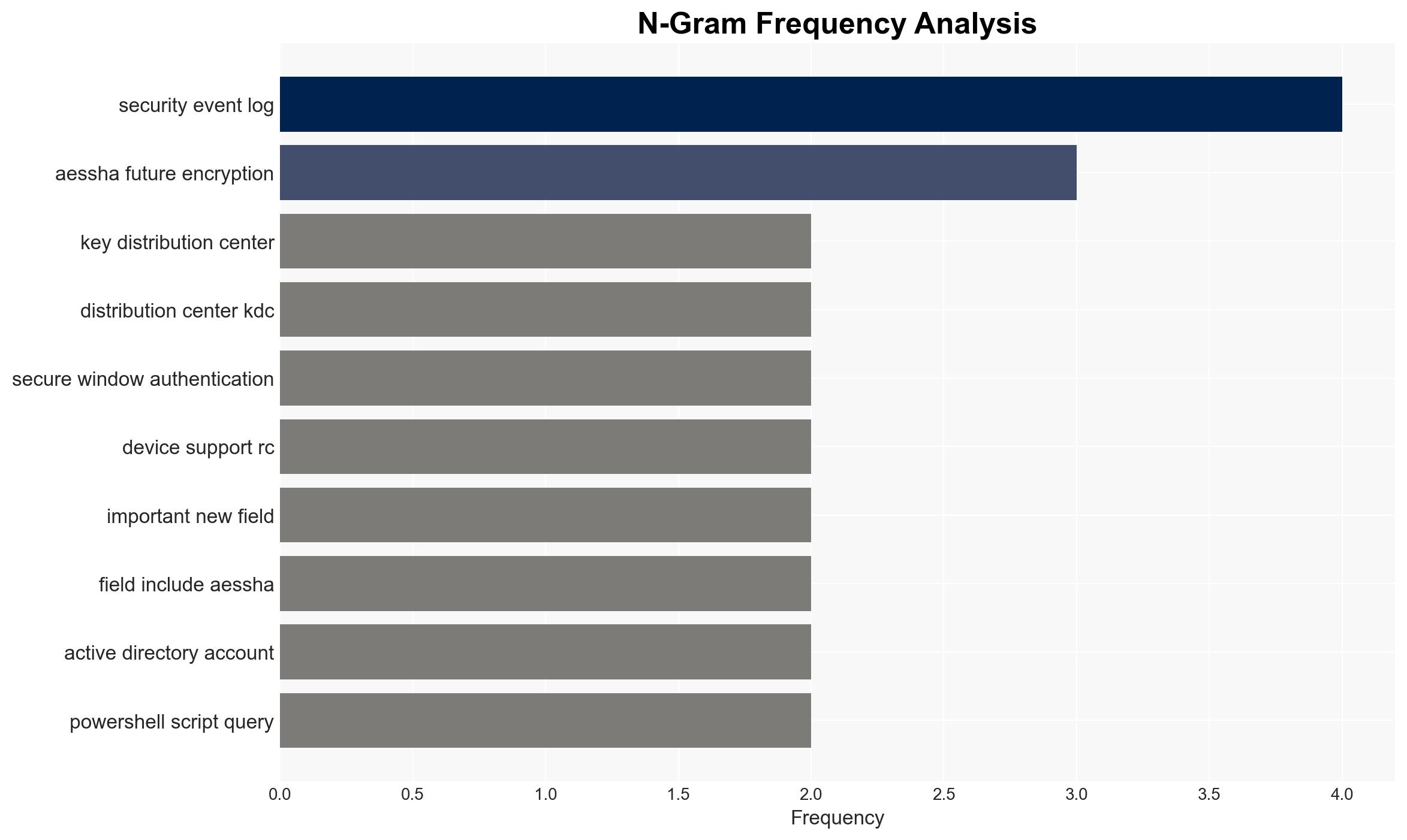
cybersecurity, encryption, Windows authentication, RC4 deprecation, AES-SHA1 transition, IT infrastructure, legacy systems
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us