Transparent Tribe Initiates New Cyber Espionage Campaign Targeting Indian Government and Academia
Published on: 2026-01-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Transparent Tribe Launches New RAT Attacks Against Indian Government and Academia
1. BLUF (Bottom Line Up Front)
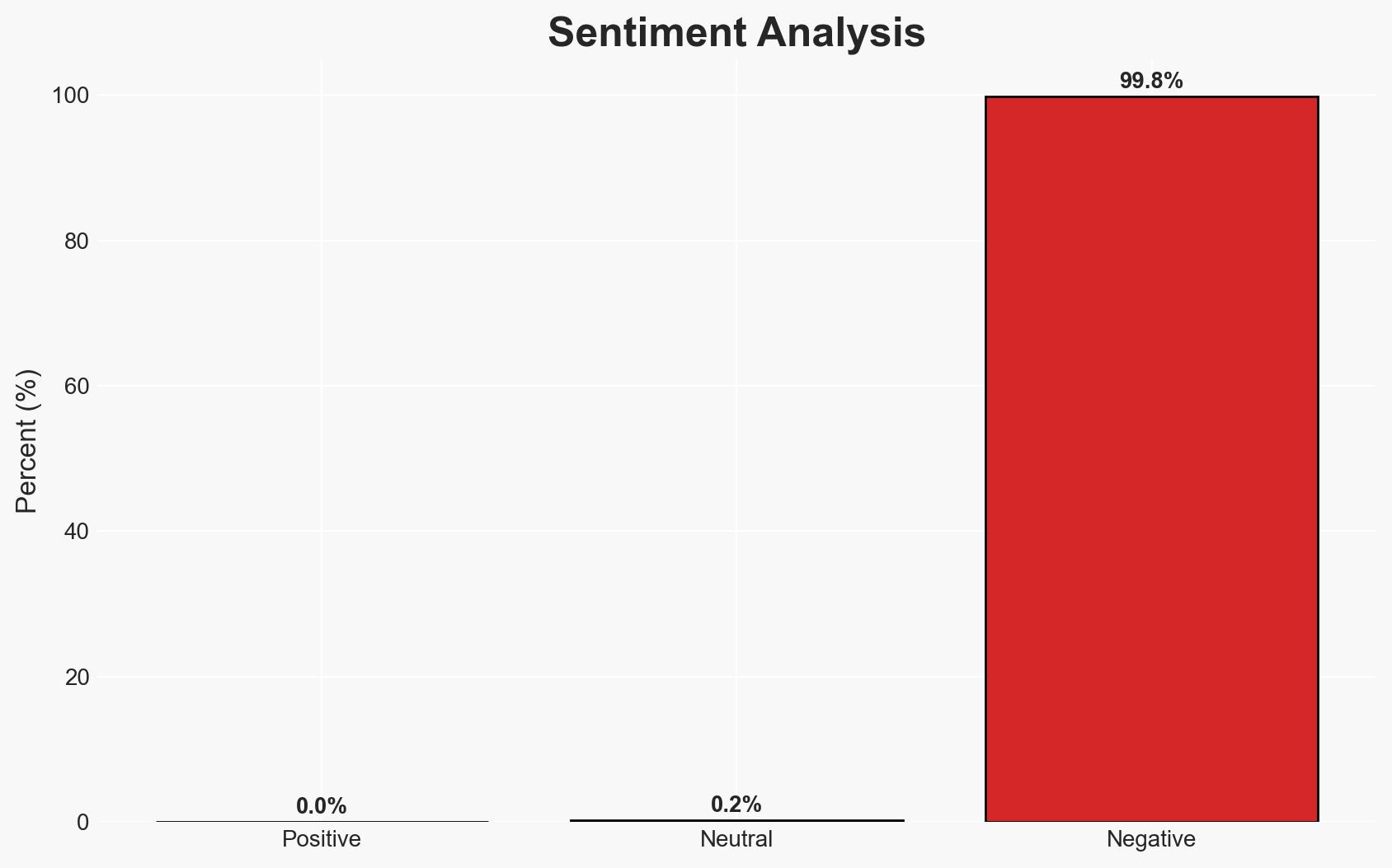
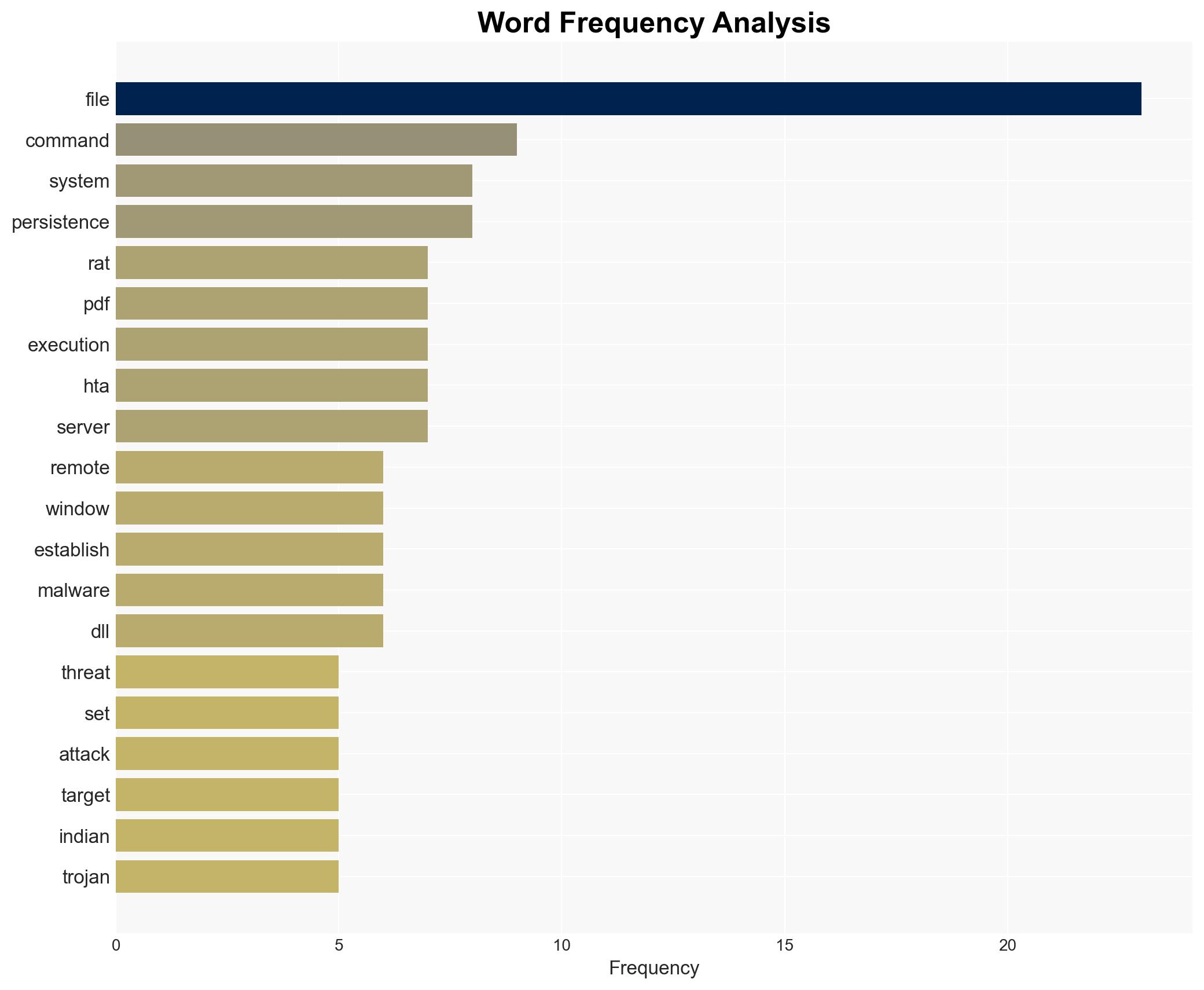
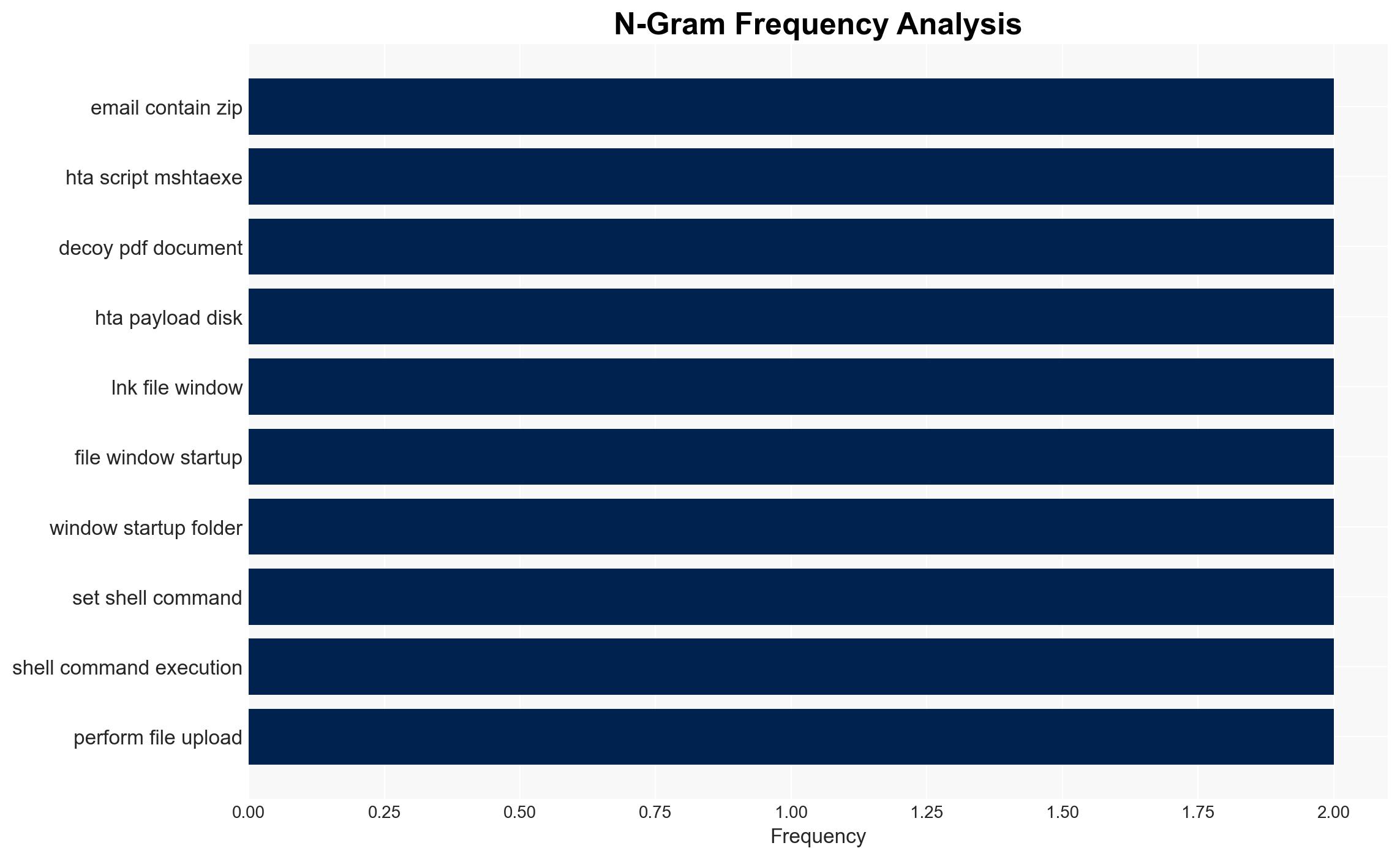
Transparent Tribe, also known as APT36, has initiated a new cyber espionage campaign targeting Indian government and academic sectors using a sophisticated remote access trojan (RAT). This campaign employs advanced evasion techniques and persistence mechanisms tailored to specific antivirus systems. The primary objective appears to be intelligence collection. Overall confidence in this assessment is moderate due to limited visibility into the full scope of the campaign and potential attribution complexities.
2. Competing Hypotheses
- Hypothesis A: Transparent Tribe is conducting state-sponsored cyber espionage to gather intelligence on Indian governmental and academic activities. This is supported by the group’s historical targeting patterns and the sophistication of the malware used. Key uncertainties include the full extent of state sponsorship and specific intelligence objectives.
- Hypothesis B: The attacks could be a false flag operation designed to misattribute the campaign to Transparent Tribe, potentially by another actor with an interest in destabilizing India or obscuring their own activities. This is less supported due to the consistent use of techniques and tools historically associated with Transparent Tribe.
- Assessment: Hypothesis A is currently better supported due to the alignment with Transparent Tribe’s known capabilities and historical targeting. Indicators that could shift this judgment include evidence of different operational patterns or attribution to another actor.
3. Key Assumptions and Red Flags
- Assumptions: Transparent Tribe continues to operate with state sponsorship; the primary goal is intelligence collection; the group has the capability to adapt malware to evade detection.
- Information Gaps: Detailed attribution evidence linking the campaign directly to state sponsorship; comprehensive understanding of the campaign’s full scope and targets.
- Bias & Deception Risks: Attribution bias due to historical patterns; potential for deceptive tactics by other actors to mislead attribution efforts.
4. Implications and Strategic Risks
This development could exacerbate tensions between India and potential state sponsors of Transparent Tribe, impacting diplomatic relations and regional stability.
- Political / Geopolitical: Potential escalation in cyber operations between India and perceived adversaries; increased diplomatic friction.
- Security / Counter-Terrorism: Heightened threat environment for Indian governmental and academic institutions; potential for retaliatory cyber measures.
- Cyber / Information Space: Increased sophistication in cyber threats; potential spread of techniques to other actors.
- Economic / Social: Possible impacts on India’s economic stability if sensitive information is compromised; public trust in digital security may be undermined.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of network traffic for indicators of compromise; implement advanced threat detection and response measures; increase awareness and training for targeted sectors.
- Medium-Term Posture (1–12 months): Strengthen cyber defense partnerships with allied nations; invest in cybersecurity infrastructure and workforce development; conduct joint exercises to improve resilience.
- Scenario Outlook: Best: Improved cyber defenses deter future attacks. Worst: Escalation leads to broader geopolitical conflict. Most-Likely: Continued low-level cyber engagements with periodic escalations.
6. Key Individuals and Entities
- Transparent Tribe (APT36), CYFIRMA (reporting entity)
7. Thematic Tags
cybersecurity, cyber-espionage, state-sponsored hacking, India, cyber defense, malware, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us