Trojanized SonicWall NetExtender app exfiltrates VPN credentials – Help Net Security
Published on: 2025-06-24
Intelligence Report: Trojanized SonicWall NetExtender app exfiltrates VPN credentials – Help Net Security
1. BLUF (Bottom Line Up Front)
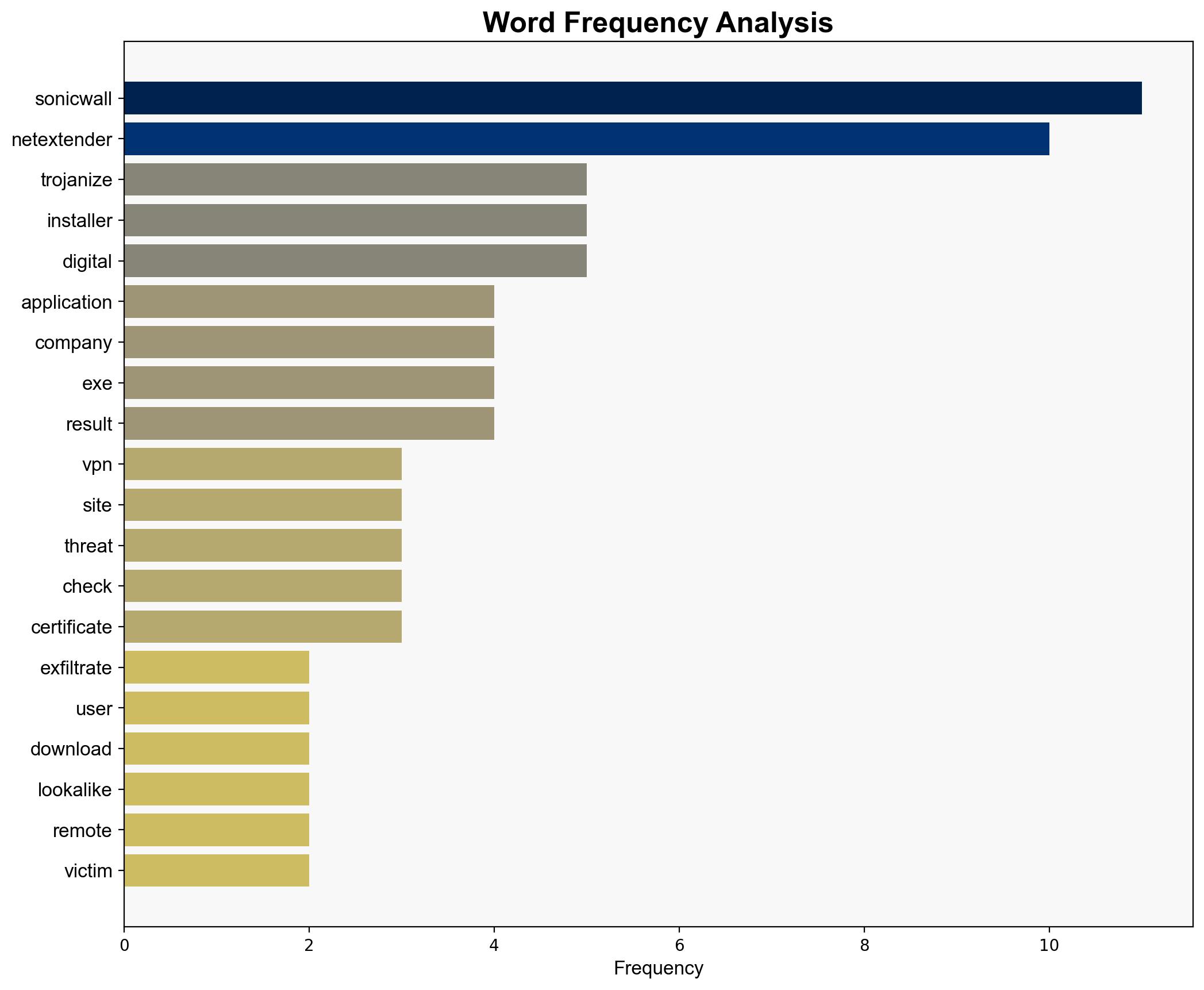
An unknown threat actor has compromised the SonicWall NetExtender application, exfiltrating VPN credentials by tricking users into downloading a trojanized version from a lookalike website. The malicious installer is digitally signed by Citylight Medium Private Limited, bypassing security checks. Immediate action is required to mitigate the threat by ensuring downloads are only from verified sources and enhancing user awareness.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated the actions of the cyber adversary to identify potential vulnerabilities within the SonicWall NetExtender application and improve defensive measures.
Indicators Development
Developed indicators to detect anomalies in digital signatures and download sources, enabling early threat detection.
Bayesian Scenario Modeling
Utilized probabilistic models to predict potential pathways for similar cyberattacks, assessing the likelihood and impact of future threats.
Network Influence Mapping
Mapped the influence of digital certificate authorities and their role in the propagation of the trojanized application.
3. Implications and Strategic Risks
The compromise of VPN credentials poses significant risks to organizational networks, potentially leading to unauthorized access and data breaches. The use of a legitimate digital signature increases the threat’s credibility, complicating detection efforts. This incident highlights systemic vulnerabilities in digital certificate management and user awareness.
4. Recommendations and Outlook
- Ensure all SonicWall applications are downloaded directly from the official SonicWall website or verified sources.
- Enhance user training to recognize phishing attempts and the importance of verifying digital signatures.
- Implement additional security layers, such as multi-factor authentication, to protect VPN access.
- Scenario Projections:
- Best Case: Rapid mitigation and user education minimize impact and prevent further breaches.
- Worst Case: Continued exploitation leads to widespread data breaches and significant reputational damage.
- Most Likely: Partial mitigation with ongoing attempts by threat actors to exploit similar vulnerabilities.
5. Key Individuals and Entities
Citylight Medium Private Limited (digital signature issuer)
6. Thematic Tags
national security threats, cybersecurity, digital certificate management, phishing, VPN security