Troops neutralize terrorist and dismantle medical facility in coordinated North West operations
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Soldiers destroy terrorists medical facility kill one in North West raids
1. BLUF (Bottom Line Up Front)
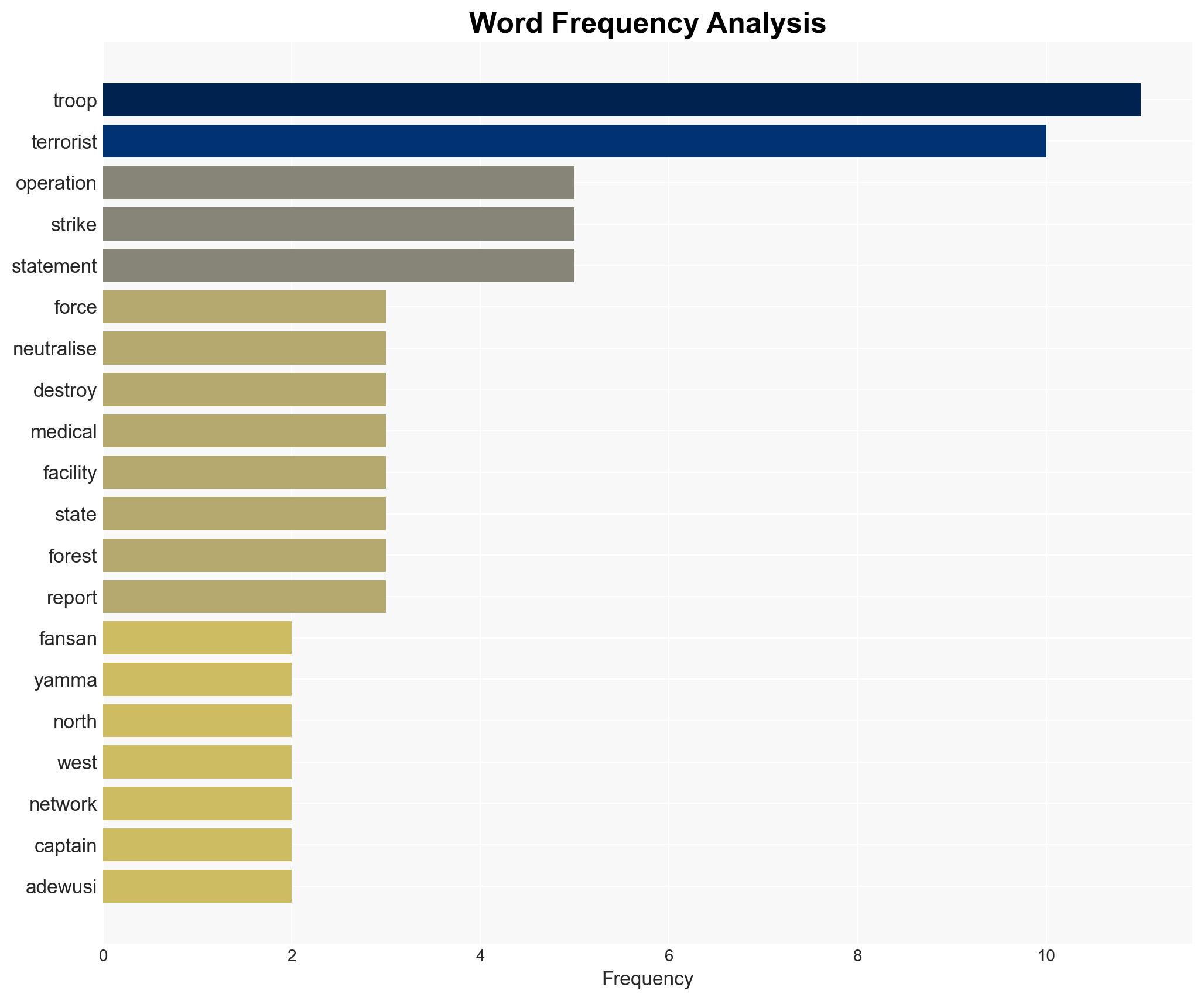
The Nigerian military’s Operation FANSAN YAMMA has successfully disrupted terrorist operations in the North West by neutralizing a terrorist and destroying a clandestine medical facility. This action likely degrades the operational capabilities of terrorist networks in the region. The operation reflects a proactive stance in counter-terrorism efforts, with moderate confidence in its immediate impact on regional security dynamics.
2. Competing Hypotheses
- Hypothesis A: The destruction of the medical facility and neutralization of a terrorist significantly disrupts the operational capabilities of the terrorist network in the North West. Supporting evidence includes the reported destruction of a key support structure and the recovery of weapons. However, the extent of the disruption is uncertain due to potential undisclosed resources and support networks.
- Hypothesis B: The operation is a tactical success but may not significantly impact the overall capabilities of the terrorist network, which could adapt quickly. This is supported by the limited number of terrorists neutralized and the possibility of other undiscovered facilities. Contradicting evidence includes the immediate operational success and intelligence-driven actions.
- Assessment: Hypothesis A is currently better supported due to the immediate tactical success and the intelligence-driven nature of the operations. Key indicators that could shift this judgment include evidence of continued or increased terrorist activity in the region or discovery of additional support facilities.
3. Key Assumptions and Red Flags
- Assumptions: The intelligence leading to the operations was accurate and comprehensive; the destroyed facility was a significant component of the terrorist network’s support system; the fleeing terrorists are unable to regroup quickly.
- Information Gaps: Details on the size and structure of the broader terrorist network in the region; potential undiscovered support facilities; the full extent of external support to the terrorists.
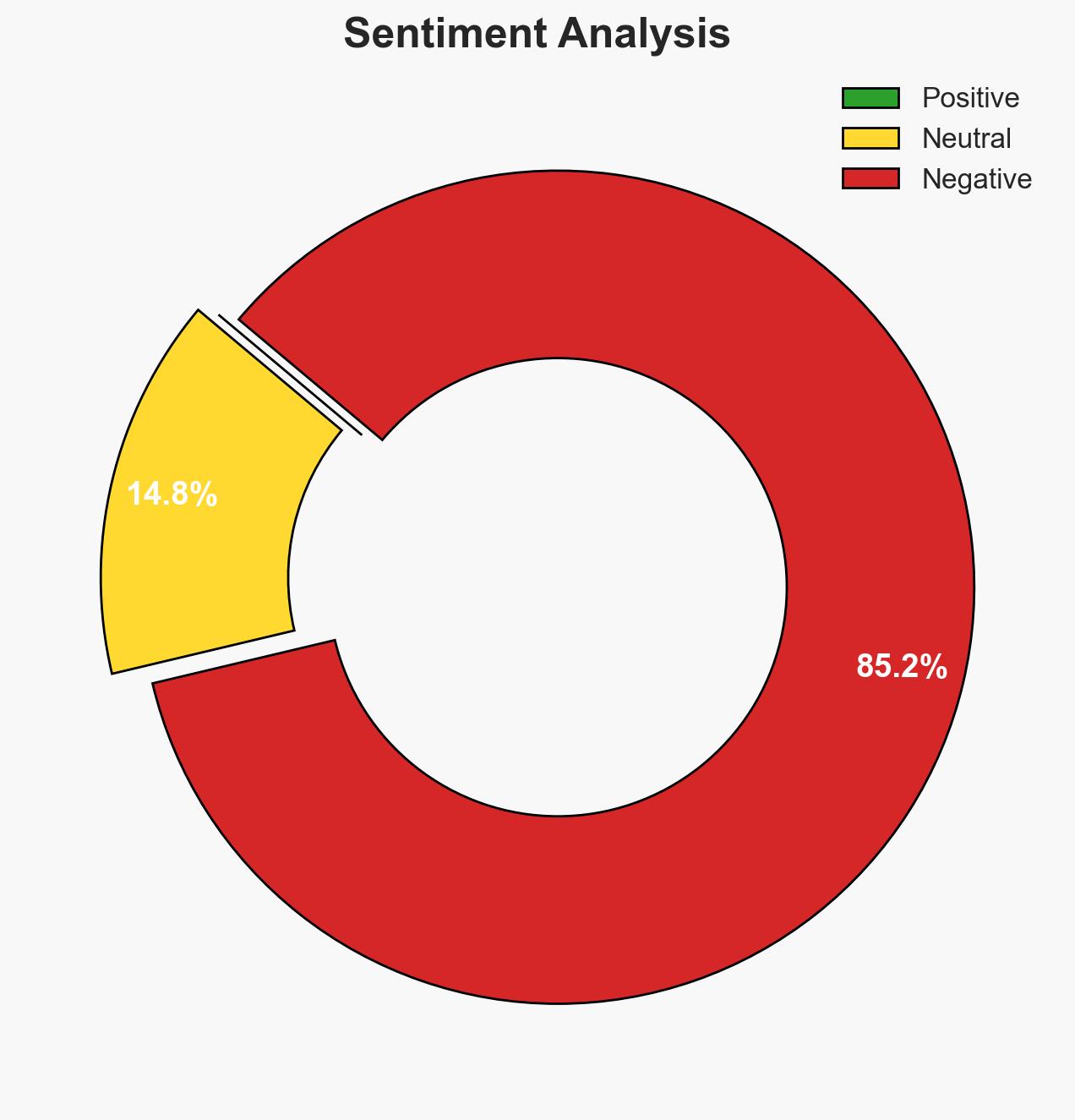
- Bias & Deception Risks: Potential bias in reporting successes to bolster public perception of military effectiveness; possibility of misinformation from terrorist networks to obscure true capabilities.
4. Implications and Strategic Risks
This development could lead to a temporary reduction in terrorist activities in the North West, but may also prompt retaliatory actions or shifts in tactics by the terrorists.
- Political / Geopolitical: Strengthened government credibility in counter-terrorism efforts; potential for increased international support or scrutiny.
- Security / Counter-Terrorism: Short-term reduction in terrorist operations; potential for increased intelligence operations in the region.
- Cyber / Information Space: Possible increase in terrorist propaganda or cyber operations to counteract perceived losses.
- Economic / Social: Improved local security could foster economic activities; however, fear of reprisals may persist among local populations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase intelligence gathering to identify remaining network components; enhance local security measures to prevent retaliatory attacks.
- Medium-Term Posture (1–12 months): Strengthen regional partnerships and intelligence-sharing frameworks; invest in community engagement to build local resilience against terrorist influence.
- Scenario Outlook:
- Best: Sustained military pressure leads to significant degradation of terrorist networks.
- Worst: Terrorists regroup and launch retaliatory attacks, destabilizing the region.
- Most-Likely: Continued military operations maintain pressure, but terrorist networks adapt, requiring ongoing vigilance.
6. Key Individuals and Entities
- Captain David Adewusi (Operation’s Media Information Officer)
- Operation FANSAN YAMMA
- 8 Division Garrison Strike Force
- Department of State Services (DSS)
- 1 Brigade and Headquarters JTF OPFY Mobile Strike Team
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, military operations, intelligence, regional security, terrorist networks, Nigeria, operational success
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us