Trust Wallet advises immediate Chrome extension update following $7 million security breach
Published on: 2025-12-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
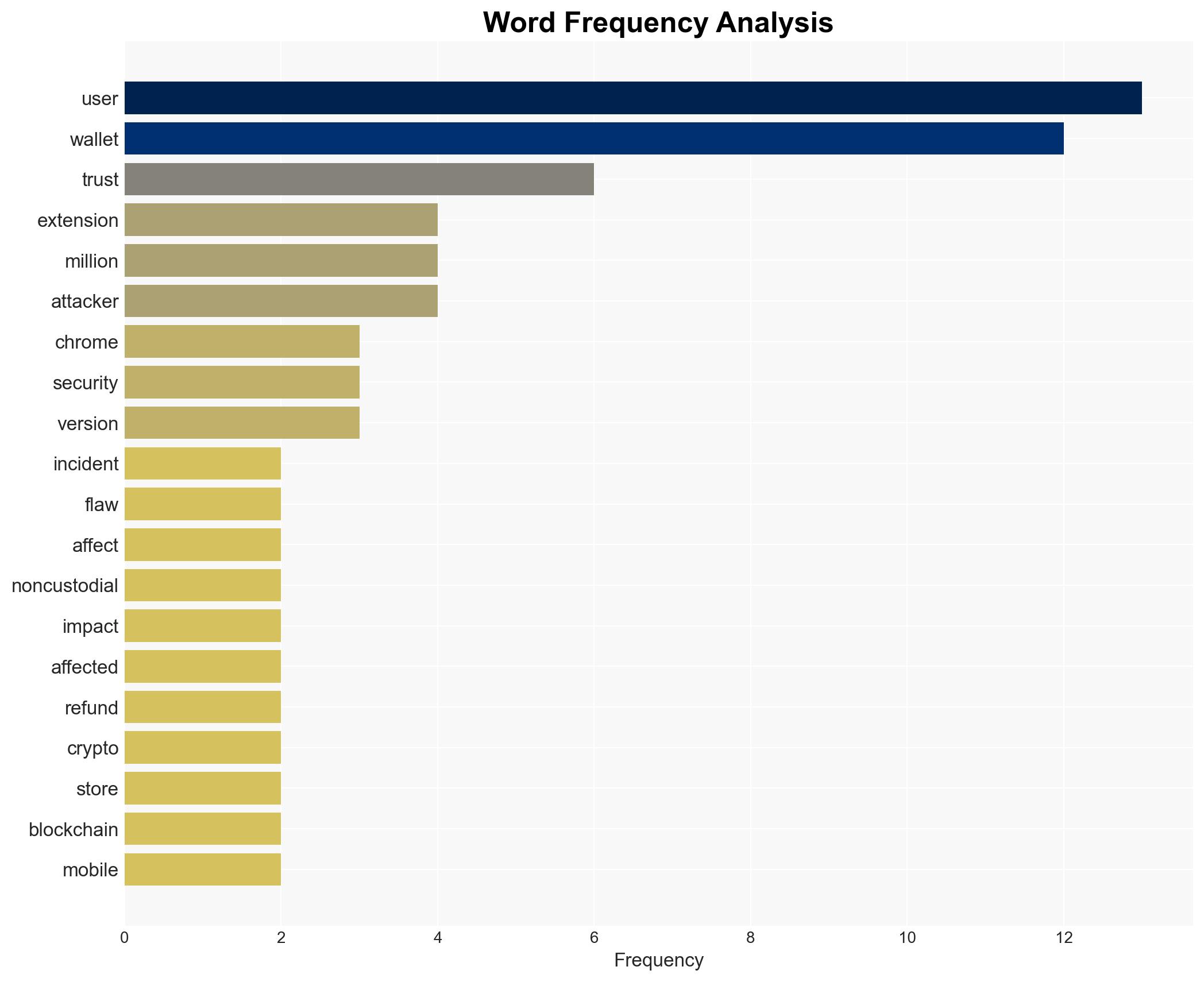
Intelligence Report: Trust Wallet warns users to update Chrome extension after 7M security loss
1. BLUF (Bottom Line Up Front)
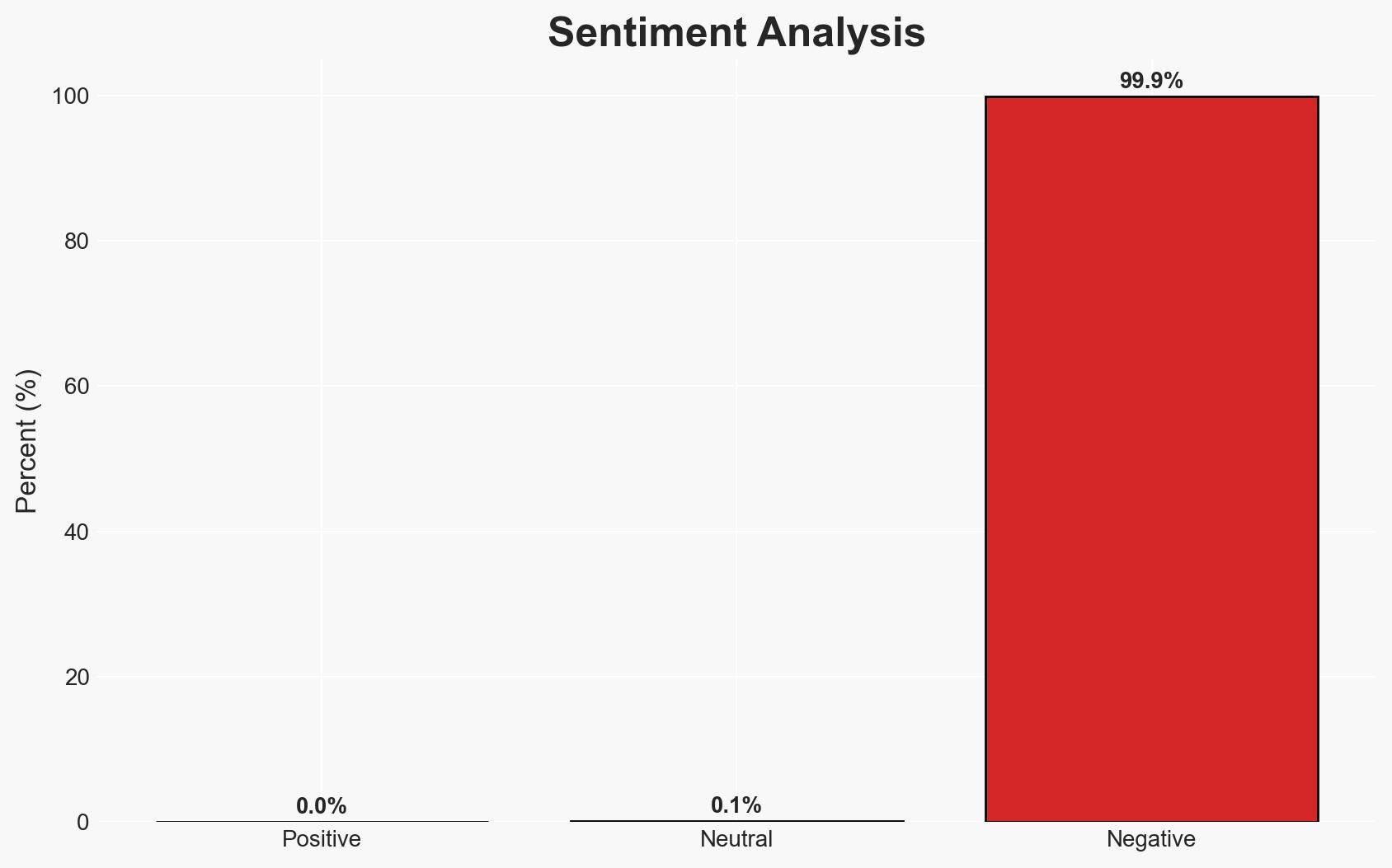
The security breach of Trust Wallet’s Chrome extension, resulting in a $7 million loss, was likely orchestrated by a sophisticated threat actor, potentially an APT group. The breach exploited a vulnerability in version 2.68, affecting approximately one million users. This incident highlights significant cybersecurity vulnerabilities in crypto wallet extensions. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was conducted by an APT group exploiting the Trust Wallet Chrome extension vulnerability. Supporting evidence includes the use of sophisticated techniques such as malicious code insertion and the use of a fake domain. However, the exact identity of the group remains unconfirmed.
- Hypothesis B: The breach was carried out by independent cybercriminals leveraging publicly available tools and tactics. While the use of open-source analytics tools supports this hypothesis, the coordination and complexity of the attack suggest a more organized group.
- Assessment: Hypothesis A is currently better supported due to the complexity and scale of the attack, which aligns with APT group capabilities. Indicators such as further attribution to specific groups or discovery of similar tactics in other incidents could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Trust Wallet’s statement on the breach is accurate; the malicious code was inserted intentionally; the attackers have advanced capabilities.
- Information Gaps: The precise identity and motivations of the attackers; the full extent of user impact beyond reported financial losses.
- Bias & Deception Risks: Potential bias in attributing the attack to an APT group without concrete evidence; risk of misinformation from unofficial channels.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny of crypto wallet security and regulatory pressures on digital asset management platforms. The breach may embolden similar attacks if not adequately addressed.
- Political / Geopolitical: Potential for increased regulatory action on crypto platforms, impacting international crypto markets.
- Security / Counter-Terrorism: Heightened threat environment for digital financial assets, requiring enhanced security measures.
- Cyber / Information Space: Increased risk of phishing and social engineering attacks exploiting user panic and misinformation.
- Economic / Social: Potential loss of trust in digital asset platforms, affecting user adoption and market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for further attacks, ensure users update to secure versions, and disseminate clear communication to prevent phishing.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing, enhance user education on security best practices.
- Scenario Outlook: Best: Quick resolution and restoration of user trust; Worst: Continued breaches and regulatory crackdowns; Most-Likely: Gradual recovery with increased security measures.
6. Key Individuals and Entities
- Trust Wallet
- SlowMist (Blockchain cybersecurity firm)
- PeckShield (Cybersecurity research firm)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, crypto wallets, APT groups, phishing, digital assets, regulatory impact, user security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us