Trust Wallet’s Chrome extension breach results in $7 million cryptocurrency theft
Published on: 2025-12-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Trust Wallet Chrome extension hack tied to millions in losses
1. BLUF (Bottom Line Up Front)
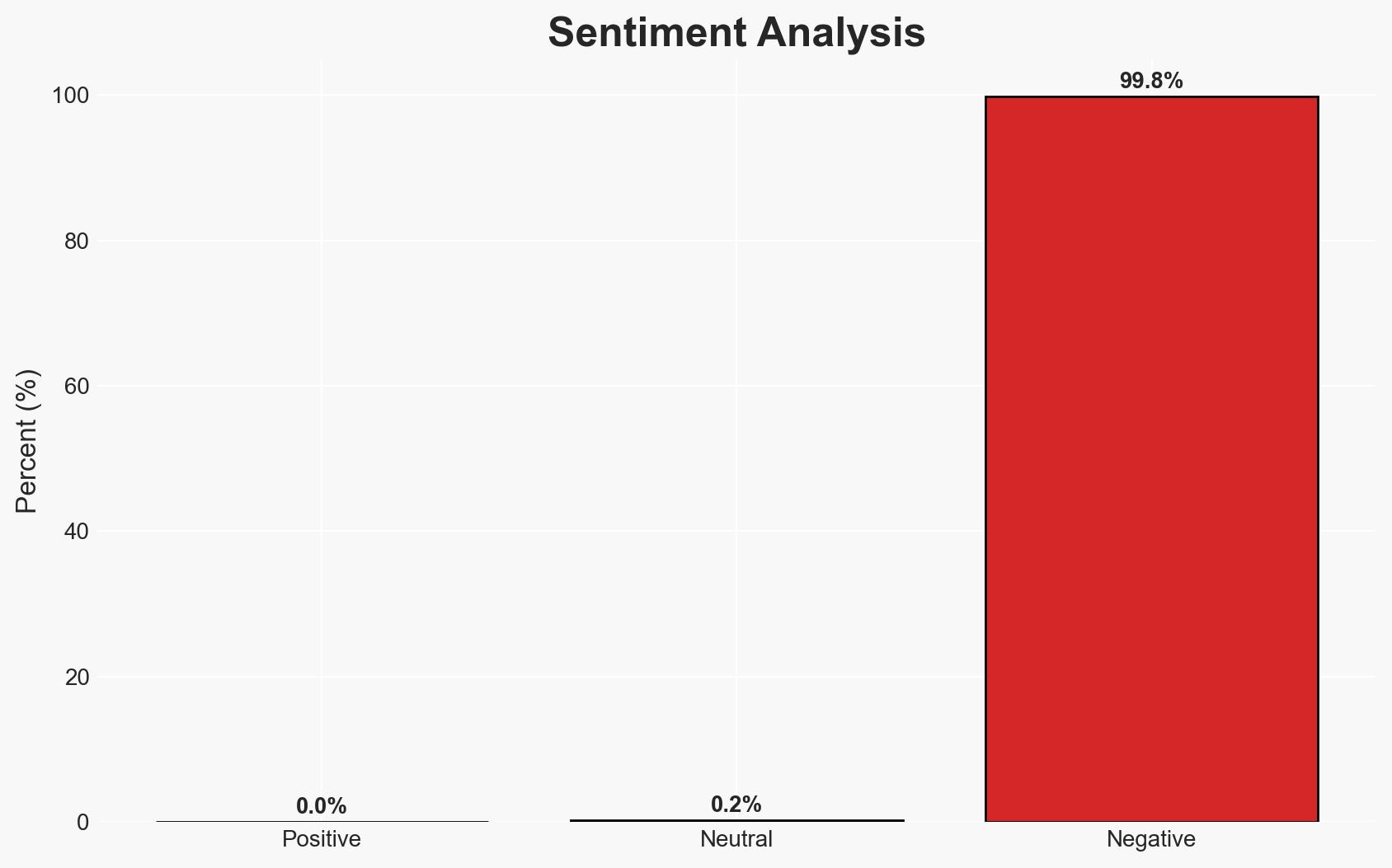
The Trust Wallet Chrome extension was compromised, resulting in at least $7 million in cryptocurrency theft. The incident appears to be a supply chain attack involving malicious code in a recent update. The primary affected parties are Trust Wallet users. Current assessment supports the hypothesis of a targeted cyber attack with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The hack was a targeted supply chain attack exploiting vulnerabilities in the Trust Wallet Chrome extension update. Evidence includes the timing of the update, the presence of suspicious code, and the registration of a malicious domain. Key uncertainties involve the identity and motives of the attackers.
- Hypothesis B: The incident was a result of internal negligence or insider threat within Trust Wallet, leading to the accidental inclusion of malicious code. Contradicting evidence includes the external registration of a malicious domain and the phishing campaigns, which suggest external orchestration.
- Assessment: Hypothesis A is currently better supported due to the external indicators of malicious intent, such as phishing domains and the registration of a new domain. Indicators that could shift this judgment include credible insider information or evidence of internal security lapses.
3. Key Assumptions and Red Flags
- Assumptions: Trust Wallet’s security protocols were breached externally; the malicious domain was registered by the attackers; the phishing campaigns are related to the primary attack.
- Information Gaps: The identity of the attackers; the full extent of the vulnerability exploited; potential insider involvement.
- Bias & Deception Risks: Confirmation bias due to reliance on external indicators; potential deception by attackers to mislead attribution efforts.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on cryptocurrency security practices and regulatory responses. It may also embolden similar cyber threats targeting supply chains.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and cryptocurrency regulation.
- Security / Counter-Terrorism: Heightened risk of similar attacks on other financial platforms, necessitating improved security measures.
- Cyber / Information Space: Increased focus on securing software supply chains and monitoring for phishing campaigns.
- Economic / Social: Loss of trust in cryptocurrency platforms could impact market stability and user adoption.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for further phishing campaigns, conduct a thorough security audit of Trust Wallet, and engage with affected users for remediation.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on cyber threats, enhance supply chain security protocols, and invest in user education on phishing risks.
- Scenario Outlook:
- Best: Rapid containment and resolution with minimal further losses.
- Worst: Continued exploitation leading to significant financial and reputational damage.
- Most-Likely: Gradual recovery with increased regulatory and security measures.
6. Key Individuals and Entities
- Changpeng “CZ” Zhao, Binance founder
- Trust Wallet
- BleepingComputer
- Security analyst Akinator
- Not clearly identifiable from open sources in this snippet for attackers
7. Thematic Tags
cybersecurity, cryptocurrency, supply chain attack, phishing, digital assets, financial security, cyber threat
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us