Two men sentenced to life for planning Islamic State-inspired attack on Jewish event in northern England
Published on: 2026-02-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pair who plotted attack on Jews in northern England jailed for life
1. BLUF (Bottom Line Up Front)
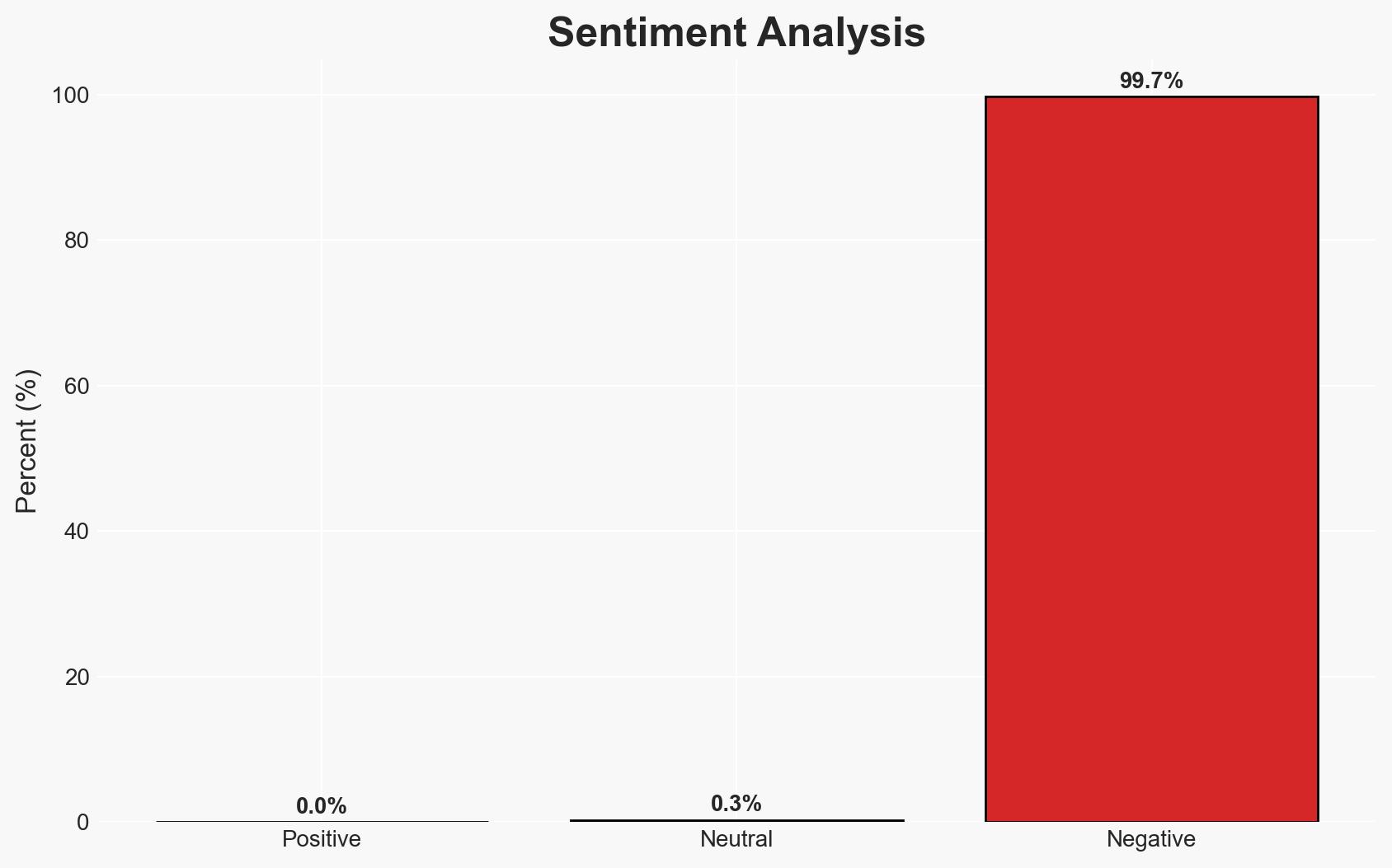
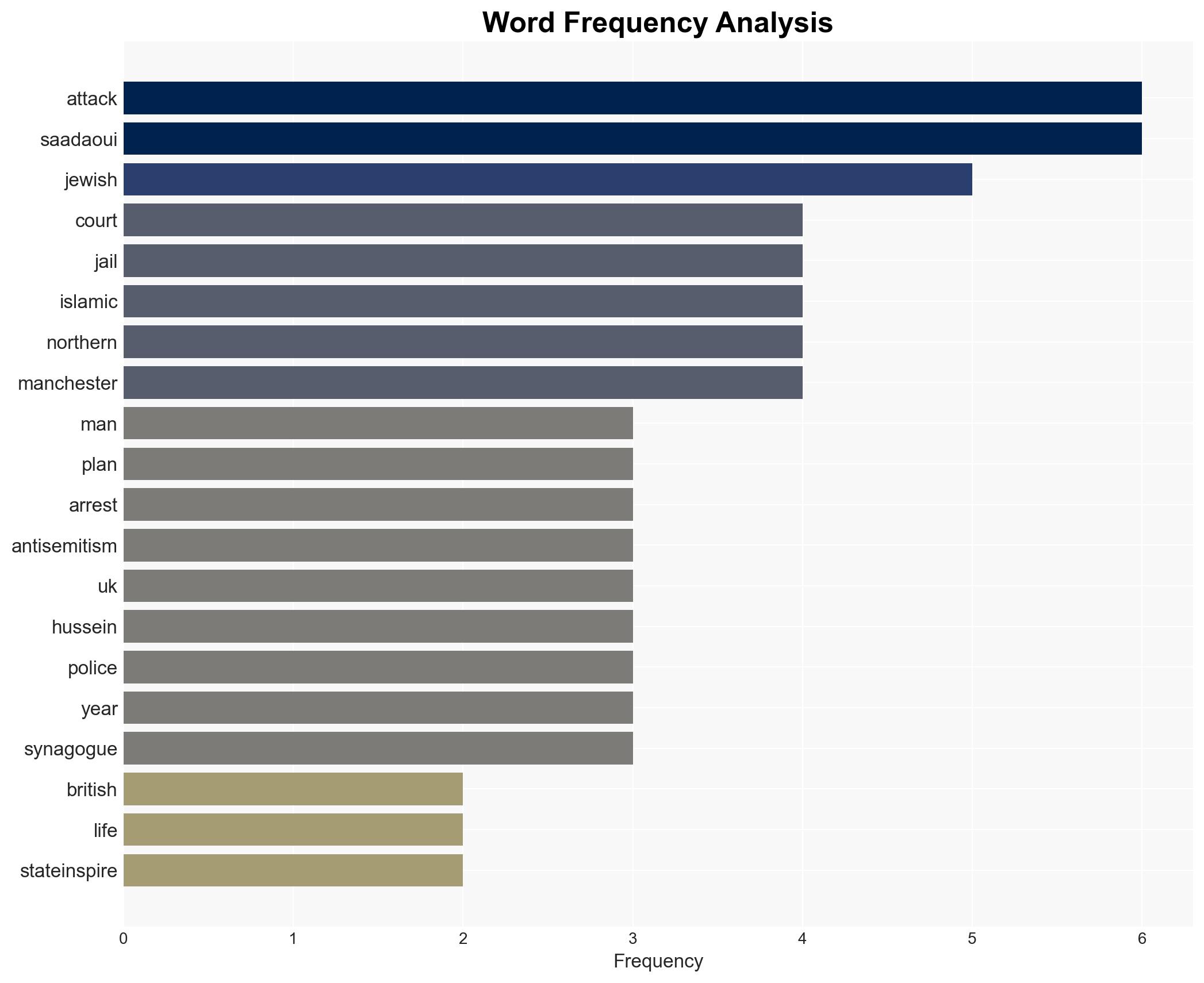
The successful conviction of Walid Saadaoui and Amar Hussein for plotting an Islamic State-inspired attack on a Jewish gathering in northern England underscores the persistent threat of extremist violence against Jewish communities. The thwarted plot highlights effective counter-terrorism operations but also raises concerns about ongoing radicalization and operational planning within the UK. Overall confidence in this assessment is moderate due to potential information gaps and deception risks.
2. Competing Hypotheses
- Hypothesis A: The plot was primarily motivated by ideological alignment with Islamic State objectives, as evidenced by Saadaoui’s admiration for Abdelhamid Abaaoud and the planned attack’s alignment with IS tactics. However, the extent of direct IS involvement remains uncertain.
- Hypothesis B: The plot was primarily driven by personal grievances or opportunistic extremism, with limited formal connection to Islamic State networks. The lack of evidence of direct IS support or coordination supports this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the ideological indicators and operational planning consistent with IS methodologies. Key indicators that could shift this judgment include evidence of direct communication or support from IS networks.
3. Key Assumptions and Red Flags
- Assumptions: The plot was primarily ideologically motivated; UK counter-terrorism capabilities are effective in intercepting such threats; Saadaoui and Hussein acted independently of larger networks.
- Information Gaps: Details on any direct communication between the plotters and IS operatives; extent of local support networks; potential other targets or plots.
- Bias & Deception Risks: Potential over-reliance on ideological indicators without corroborating operational evidence; possible deception by the plotters regarding their true intentions or affiliations.
4. Implications and Strategic Risks
This development highlights the ongoing risk of extremist plots targeting minority communities, potentially exacerbating social tensions and necessitating enhanced security measures. The thwarted attack could inspire copycat actions or retaliatory violence.
- Political / Geopolitical: Potential for increased political pressure on counter-terrorism policies and community relations initiatives.
- Security / Counter-Terrorism: Reinforces the need for vigilant monitoring of radicalization pathways and potential lone-actor threats.
- Cyber / Information Space: Possible exploitation of digital platforms for extremist recruitment and planning, requiring enhanced cyber surveillance.
- Economic / Social: Potential impact on community cohesion and public confidence in security measures, with possible economic implications for affected areas.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of extremist online activities; engage with community leaders to reassure and strengthen community resilience.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to counter online radicalization; enhance intelligence-sharing frameworks with international partners.
- Scenario Outlook: Best: Strengthened community relations and reduced extremist activities; Worst: Successful similar attacks and increased radicalization; Most-Likely: Continued low-level threats with sporadic plots intercepted.
6. Key Individuals and Entities
- Walid Saadaoui – Main instigator, Tunisian origin
- Amar Hussein – Co-conspirator, Kuwaiti origin
- Abdelhamid Abaaoud – Islamic State recruiter, ideological influence
- Jihad al-Shamie – Perpetrator of previous attack in Manchester
7. Thematic Tags
Counter-Terrorism, radicalization, Islamic State, antisemitism, UK security, community resilience, extremist networks
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us