U.S. Forces Intensify Operations in Syria to Counter ISIS Threats to National Security
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US Forces Protect the Homeland with Aggressive Pursuit of ISIS in Syria
1. BLUF (Bottom Line Up Front)
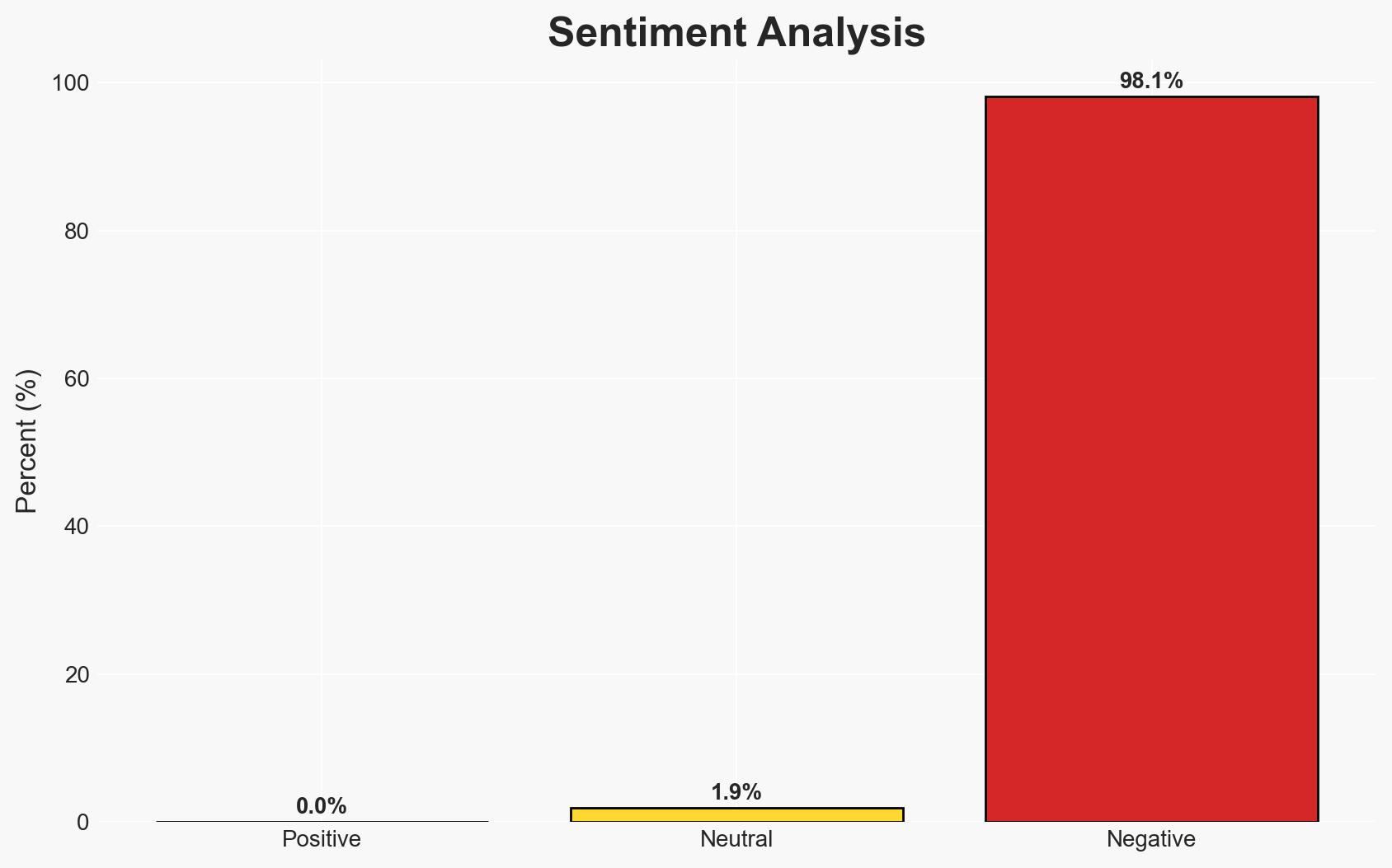
U.S. and partner operations in Syria have significantly disrupted ISIS activities, capturing or killing key operatives and dismantling weapons caches. This effort is crucial in preventing ISIS from posing a direct threat to the U.S. and its interests. The most likely hypothesis is that continued operations will further degrade ISIS’s capabilities, though the potential for ISIS to adapt remains. Overall confidence in this assessment is moderate due to existing information gaps and the dynamic nature of terrorist operations.
2. Competing Hypotheses
- Hypothesis A: U.S. operations in Syria are effectively degrading ISIS’s ability to conduct attacks against the U.S. and its allies. This is supported by the reported capture or killing of key ISIS operatives and the destruction of weapons caches. However, uncertainties remain about the full extent of ISIS’s operational capabilities and networks.
- Hypothesis B: Despite U.S. operations, ISIS retains the ability to inspire and coordinate attacks, potentially adapting its tactics to circumvent current counter-terrorism measures. Evidence for this includes the persistence of ISIS-inspired plots and the group’s historical resilience.
- Assessment: Hypothesis A is currently better supported due to tangible operational successes reported by CENTCOM. However, indicators such as new attack plots or evidence of operational adaptation by ISIS could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: U.S. and partner forces have accurate intelligence on ISIS networks; Syrian government cooperation will continue; ISIS lacks significant external support.
- Information Gaps: Detailed intelligence on remaining ISIS leadership and their operational plans; the extent of ISIS’s recruitment and radicalization efforts globally.
- Bias & Deception Risks: Potential over-reliance on U.S. military sources; risk of underestimating ISIS’s adaptability and resilience.
4. Implications and Strategic Risks
The ongoing operations in Syria could lead to a significant reduction in ISIS’s operational capabilities, but may also drive the group to adapt or decentralize further. The situation could evolve with broader regional dynamics, including Syrian government stability and international relations.
- Political / Geopolitical: Continued U.S. operations may strain relations with regional actors opposed to U.S. presence in Syria.
- Security / Counter-Terrorism: Successful operations may reduce immediate threats but could lead to ISIS adopting more clandestine or cyber-based tactics.
- Cyber / Information Space: Potential increase in ISIS’s use of online platforms for propaganda and recruitment as physical operations are disrupted.
- Economic / Social: Prolonged instability in Syria could impact regional economies and exacerbate humanitarian issues.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing with regional partners; increase monitoring of online extremist content.
- Medium-Term Posture (1–12 months): Strengthen partnerships with local Syrian forces; develop capabilities to counter potential ISIS cyber operations.
- Scenario Outlook: Best: ISIS capabilities are significantly degraded with minimal resurgence. Worst: ISIS adapts, increasing attacks in the region or globally. Most-Likely: Continued degradation with sporadic ISIS attempts to regroup.
6. Key Individuals and Entities
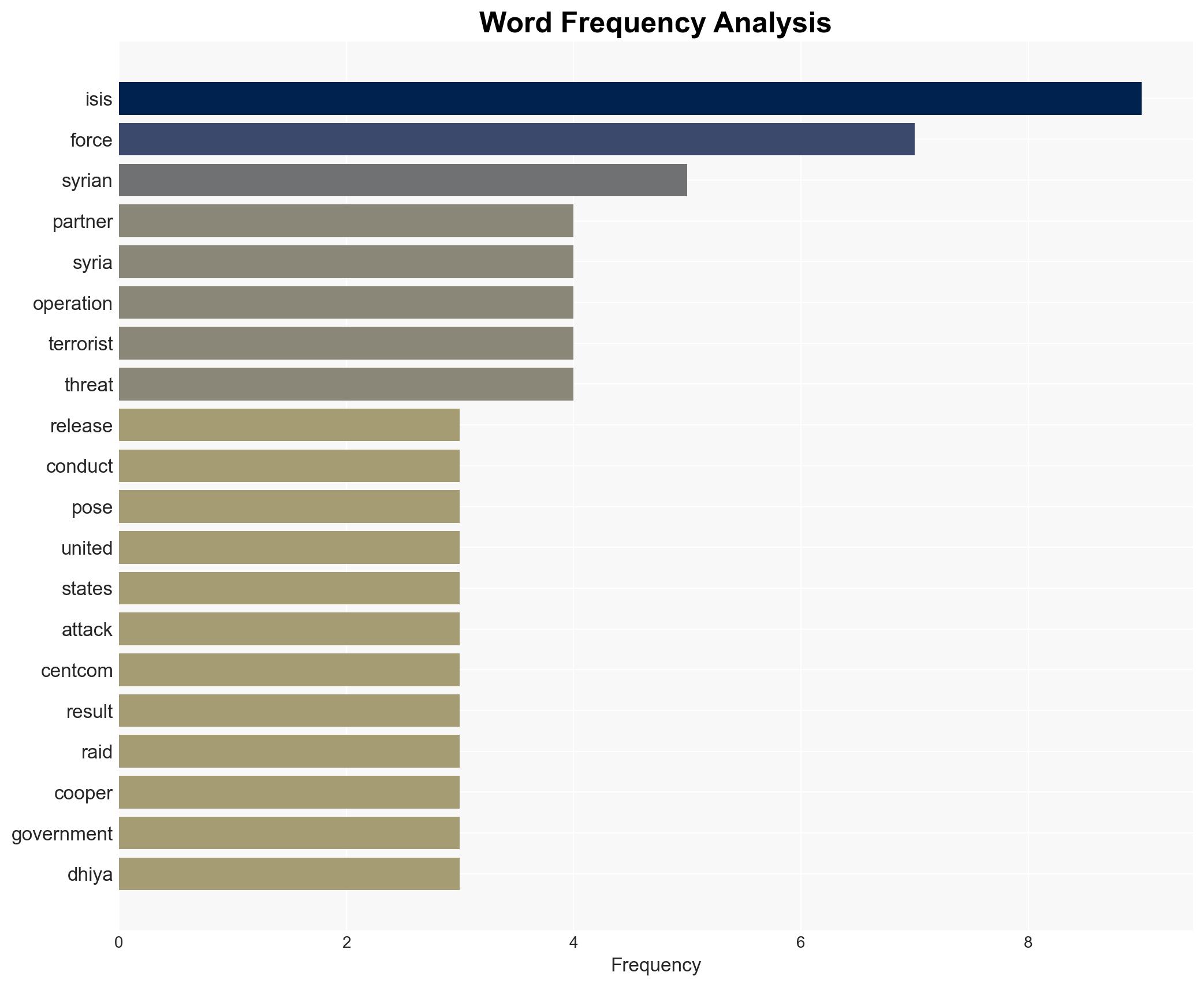
- Omar Abdul Qader, Senior ISIS operative
- Dhiya’ Zawba Muslih al-Hardani, Senior ISIS leader
- Adm. Brad Cooper, CENTCOM commander
- Not clearly identifiable from open sources in this snippet
7. Thematic Tags
Counter-Terrorism, ISIS, military operations, Syria, U.S. Central Command, regional security, intelligence sharing
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us