UK allocates £210 million to enhance cybersecurity across government services and align with critical infrast…
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: UK splashes 210M on cyber plan to stop Whitehall getting pwnd
1. BLUF (Bottom Line Up Front)
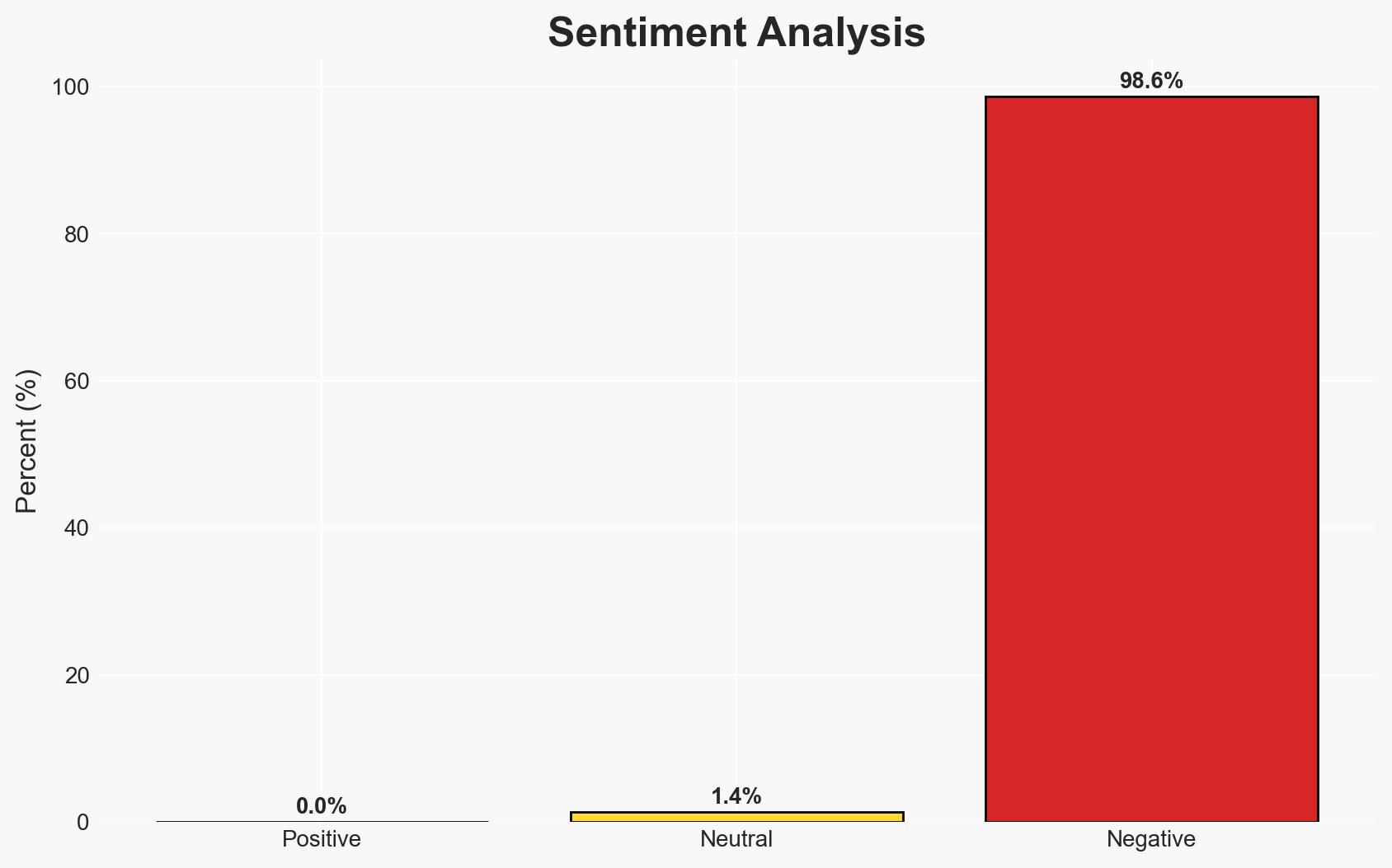
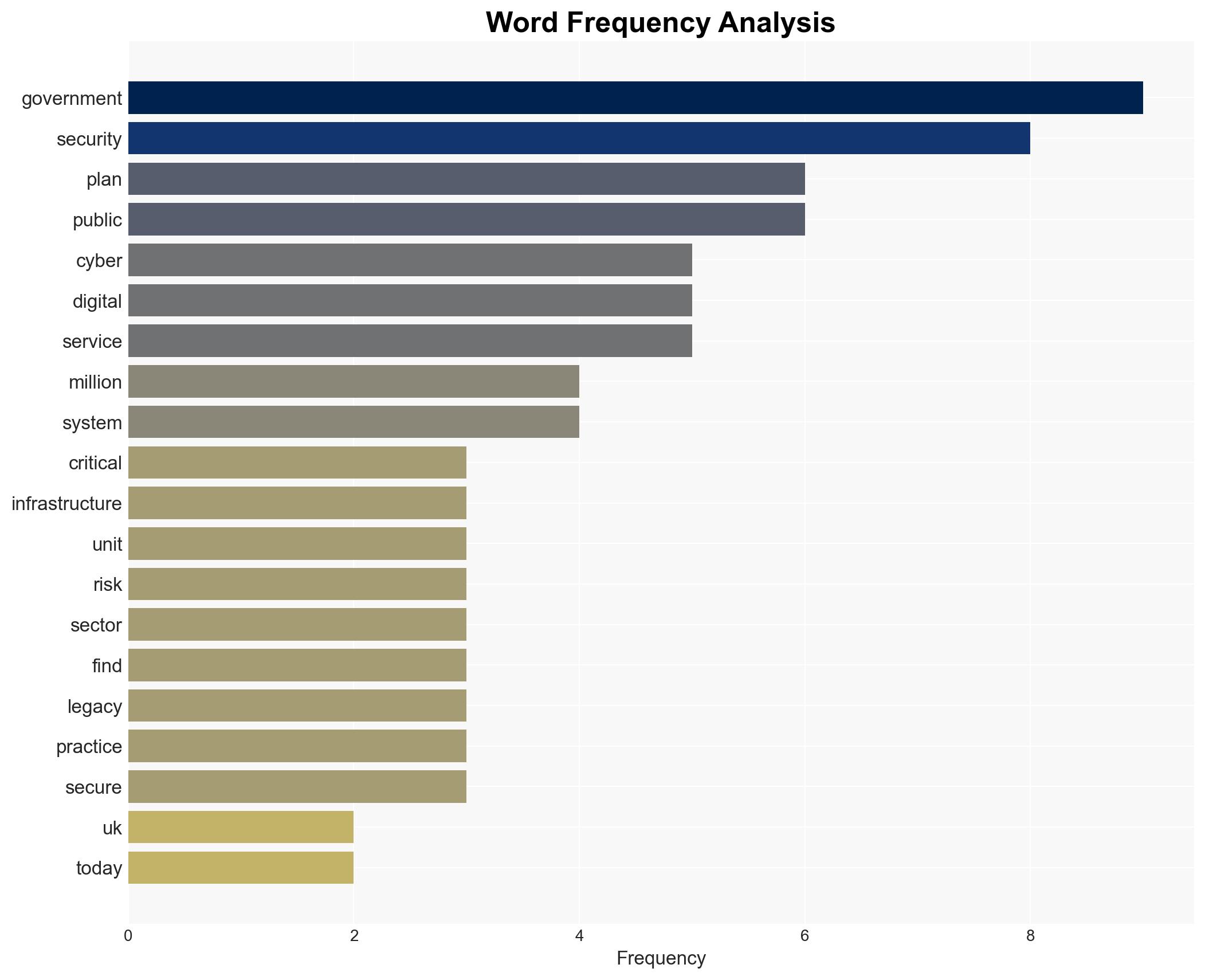
The UK government has launched a £210 million cyber action plan to enhance cybersecurity across public services, aiming to mitigate risks and improve resilience against cyber threats. The initiative is likely to bolster defenses but may face challenges in implementation and effectiveness due to existing systemic vulnerabilities. This assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The cyber action plan will significantly improve the UK’s public sector cybersecurity posture, reducing vulnerabilities and preventing future breaches. This is supported by the establishment of a dedicated Government Cyber Unit and increased funding. However, uncertainties include the actual implementation effectiveness and the sufficiency of the allocated budget.
- Hypothesis B: The cyber action plan will have limited impact due to entrenched systemic issues, such as legacy systems and low maturity of existing controls. The recent history of breaches and the NAO’s critical findings support this view, suggesting that the plan may not address deeper structural problems.
- Assessment: Hypothesis B is currently better supported due to the persistent nature of the identified vulnerabilities and the historical challenges in addressing them. Key indicators that could shift this judgment include measurable improvements in system maturity and successful mitigation of identified risks.
3. Key Assumptions and Red Flags
- Assumptions: The new funding will be efficiently allocated; the Government Cyber Unit will effectively coordinate cybersecurity efforts; existing vulnerabilities can be mitigated with current technology and practices.
- Information Gaps: Detailed implementation plans and timelines; specific metrics for measuring success; clarity on how legacy systems will be addressed.
- Bias & Deception Risks: Potential overestimation of the plan’s impact by government officials; underreporting of ongoing vulnerabilities; possible manipulation of success metrics.
4. Implications and Strategic Risks
The development could lead to improved cybersecurity practices across the UK public sector, but may also expose gaps if not effectively implemented. The plan’s success or failure will influence broader national security dynamics.
- Political / Geopolitical: Strengthened cybersecurity could enhance the UK’s international standing and deterrence posture, but failure might lead to reputational damage.
- Security / Counter-Terrorism: Improved defenses could reduce the risk of cyber-attacks disrupting critical services, though persistent vulnerabilities may still be exploited.
- Cyber / Information Space: The initiative may set a precedent for other nations, influencing global cybersecurity standards and practices.
- Economic / Social: Successful implementation could protect economic interests and public trust, while failure might lead to financial losses and public dissatisfaction.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of current cybersecurity capabilities; establish clear metrics for success; initiate stakeholder engagement for feedback and collaboration.
- Medium-Term Posture (1–12 months): Develop partnerships with private sector cybersecurity experts; invest in training and capacity building for public sector employees; continuously monitor and adapt strategies based on emerging threats.
- Scenario Outlook:
- Best: Significant reduction in cyber incidents with enhanced public trust and international reputation.
- Worst: Continued breaches and systemic failures leading to economic and reputational damage.
- Most-Likely: Incremental improvements with ongoing challenges in addressing legacy systems and resource allocation.
6. Key Individuals and Entities
- UK Chief Information Security Officer (CISO)
- Department for Science, Innovation and Technology (DSIT)
- National Audit Office (NAO)
- Digital Minister Ian Murray
- Cisco, NCC Group, Palo Alto Networks, Sage, Santander
7. Thematic Tags
cybersecurity, public sector, UK government, cyber resilience, digital infrastructure, national security, legacy systems
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us