UK Construction Company Compromised by Prometei Botnet Exploiting Weak RDP Credentials on Windows Server
Published on: 2026-02-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: UK Construction Firm Hit by Prometei Botnet Hiding in Windows Server
1. BLUF (Bottom Line Up Front)
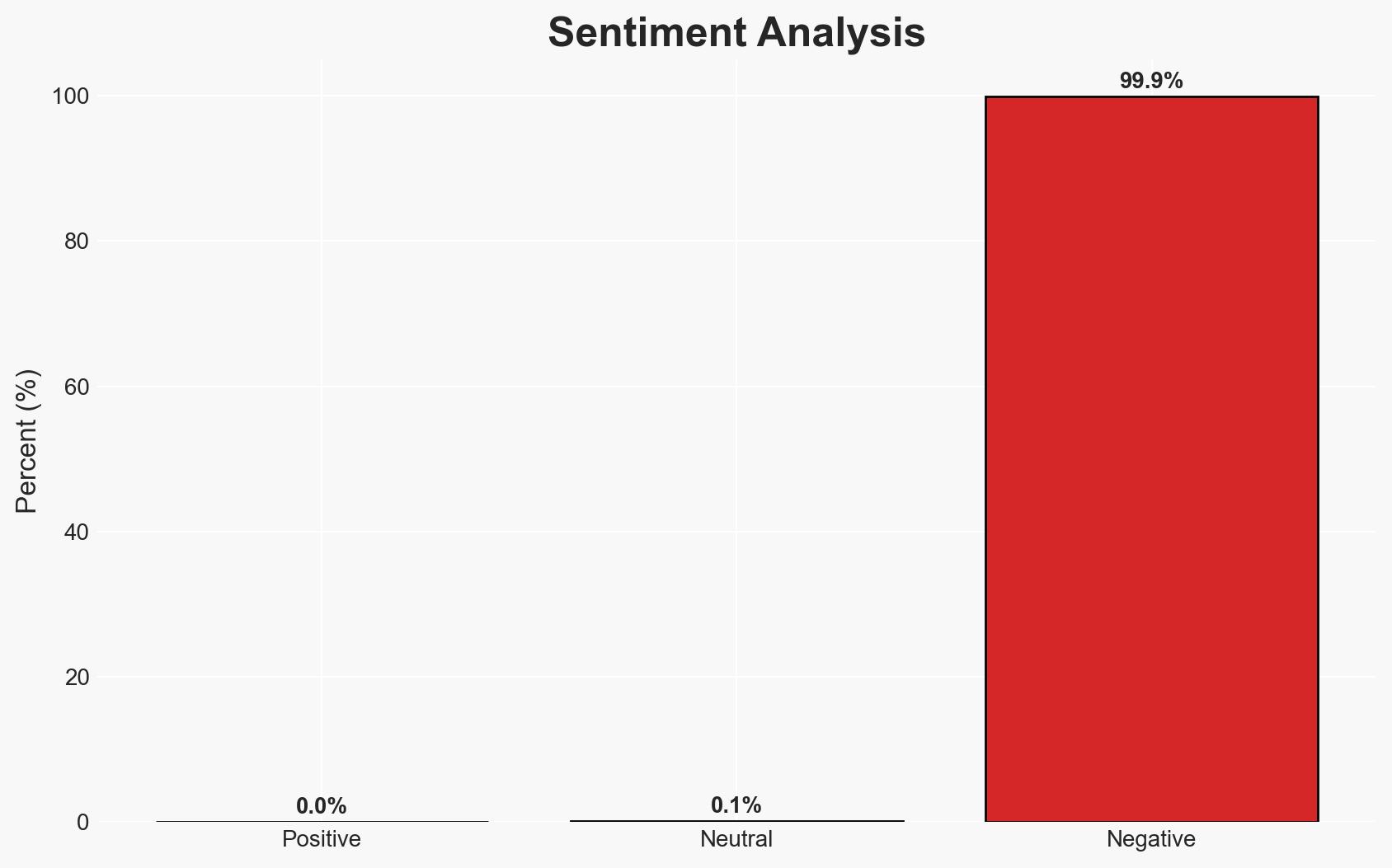
The Prometei botnet, linked to Russian actors, compromised a UK construction firm’s Windows Server, primarily for cryptocurrency mining and credential theft. The breach highlights vulnerabilities in systems using weak passwords and underscores the botnet’s sophisticated evasion techniques. This incident poses moderate confidence in the need for enhanced cybersecurity measures across similar sectors.
2. Competing Hypotheses
- Hypothesis A: The Prometei botnet targeted the UK construction firm primarily for financial gain through Monero mining. This is supported by the botnet’s known capabilities and past behavior. However, the use of sophisticated evasion techniques suggests a possible secondary motive of maintaining long-term access for broader cyber operations.
- Hypothesis B: The attack was part of a broader reconnaissance effort by Russian-linked actors to map vulnerabilities in critical infrastructure sectors. While plausible, this lacks direct evidence from the current incident, which primarily indicates financial motives.
- Assessment: Hypothesis A is currently better supported due to the botnet’s established pattern of financial exploitation. Indicators such as the use of weak passwords and the primary focus on Monero mining reinforce this assessment. However, any future evidence of data exfiltration or targeting of other critical sectors could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The botnet’s primary motive is financial gain; the attack vector was weak RDP credentials; Prometei’s operators are Russian-linked; the botnet’s presence is limited to the construction firm.
- Information Gaps: Specific details on the extent of data access or exfiltration, confirmation of the operators’ identity and broader targeting patterns.
- Bias & Deception Risks: Potential over-reliance on the financial motive could obscure other strategic objectives; source bias from security firms may emphasize certain threat aspects over others.
4. Implications and Strategic Risks
The incident could lead to increased scrutiny of cybersecurity practices in the construction sector and similar industries. If the botnet’s operators are indeed Russian-linked, this may exacerbate geopolitical tensions and lead to retaliatory cyber measures.
- Political / Geopolitical: Potential for increased diplomatic friction between the UK and Russia if state involvement is confirmed.
- Security / Counter-Terrorism: Heightened awareness and defensive postures in critical infrastructure sectors against similar threats.
- Cyber / Information Space: Increased focus on securing RDP and similar protocols; potential for further exploitation of weak credentials in other sectors.
- Economic / Social: Possible financial losses for affected firms; increased costs for cybersecurity enhancements across the industry.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement strong password policies and multi-factor authentication; conduct a thorough forensic analysis to assess the breach’s scope.
- Medium-Term Posture (1–12 months): Develop sector-wide cybersecurity standards; enhance collaboration with cybersecurity firms for threat intelligence sharing.
- Scenario Outlook:
- Best: Rapid containment and improved sector resilience prevent further incidents.
- Worst: Broader targeting of critical infrastructure leads to significant disruptions.
- Most-Likely: Incremental improvements in cybersecurity practices reduce similar incidents over time.
6. Key Individuals and Entities
- eSentire Threat Response Unit (TRU)
- Primesoftex Ltd (associated server)
- Not clearly identifiable from open sources in this snippet for specific individuals.
7. Thematic Tags
cybersecurity, botnet, critical infrastructure, Russian cyber activity, financial cybercrime, password security, RDP vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us