UK watchdog warns app developers using end-to-end encryption may be classified as hostile actors under new la…
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
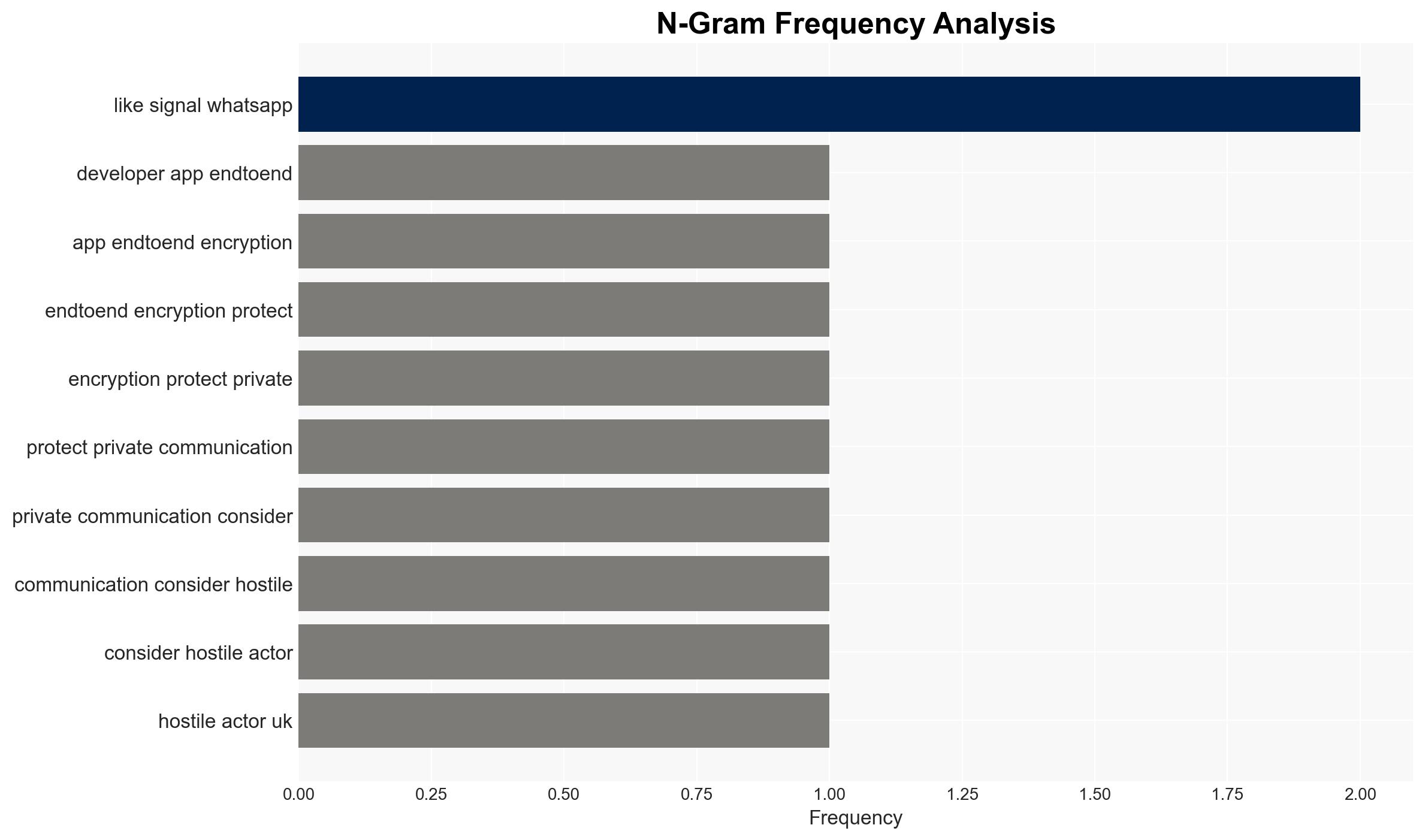
Intelligence Report: Creating apps like Signal or WhatsApp could be ‘hostile activity’ claims UK watchdog
1. BLUF (Bottom Line Up Front)
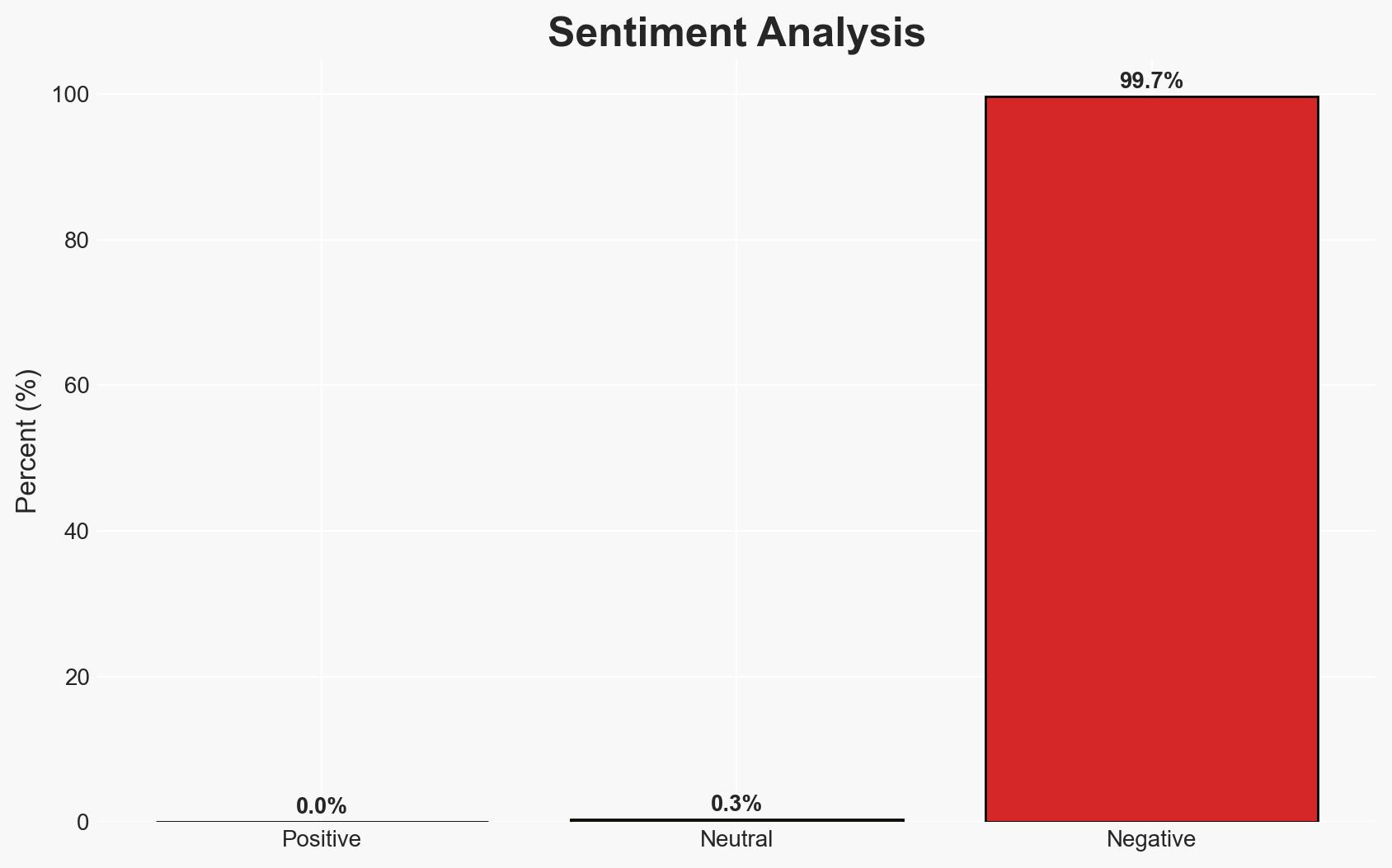
The UK government’s consideration of developers of end-to-end encrypted apps as potential “hostile actors” represents a significant shift in national security policy, with implications for privacy and technology regulation. This stance is primarily driven by concerns over monitoring capabilities. The most likely hypothesis is that this is a strategic move to increase surveillance capabilities, affecting tech companies and privacy advocates. Overall confidence in this assessment is moderate, given the current legislative context and ongoing debates.
2. Competing Hypotheses
- Hypothesis A: The UK government is using the classification of encrypted app developers as “hostile actors” to enhance its surveillance capabilities. This is supported by the broad powers granted under recent legislation and the pressure on tech companies to weaken encryption. However, it is uncertain how this will be enforced and its impact on international relations.
- Hypothesis B: The classification is primarily a deterrent against foreign influence and not intended for domestic application. This is contradicted by the focus on domestic tech companies and the legislative push against encryption, suggesting a broader application.
- Assessment: Hypothesis A is currently better supported due to the legislative context and ongoing pressure on tech companies to comply with surveillance demands. Indicators such as increased legislative actions against encryption and public statements by government officials could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The UK government prioritizes national security over privacy; legislative changes will be enforced; tech companies will resist weakening encryption.
- Information Gaps: Specific enforcement mechanisms for the classification of “hostile actors”; the extent of international cooperation on encryption policies.
- Bias & Deception Risks: Potential bias in government reports favoring increased surveillance; risk of tech companies overstating the impact to rally public support.
4. Implications and Strategic Risks
This development could lead to increased tensions between the UK government and tech companies, impacting privacy rights and international tech policy. Over time, this may influence global encryption standards and privacy norms.
- Political / Geopolitical: Potential strain on UK-US tech relations; influence on EU data protection policies.
- Security / Counter-Terrorism: Enhanced surveillance capabilities may improve threat monitoring but could also drive malicious actors to more secure platforms.
- Cyber / Information Space: Risk of increased cyber vulnerabilities if encryption is weakened; potential for misinformation campaigns exploiting privacy concerns.
- Economic / Social: Possible impact on the tech sector’s growth and innovation; public backlash over privacy rights could affect social trust in government.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor legislative developments; engage with tech companies to assess potential compliance strategies; evaluate public sentiment on privacy issues.
- Medium-Term Posture (1–12 months): Develop resilience measures for potential cyber vulnerabilities; strengthen partnerships with international allies on encryption standards.
- Scenario Outlook: Best: Harmonization of privacy and security policies; Worst: Increased surveillance leading to public unrest; Most-Likely: Ongoing legislative adjustments with tech sector pushback.
6. Key Individuals and Entities
- Jonathan Hall KC, Independent Reviewer of State Threats Legislation
- UK government and lawmakers
- Tech companies (e.g., Apple, Signal, WhatsApp)
- Olivier Crépin-Leblond, Internet Society
7. Thematic Tags
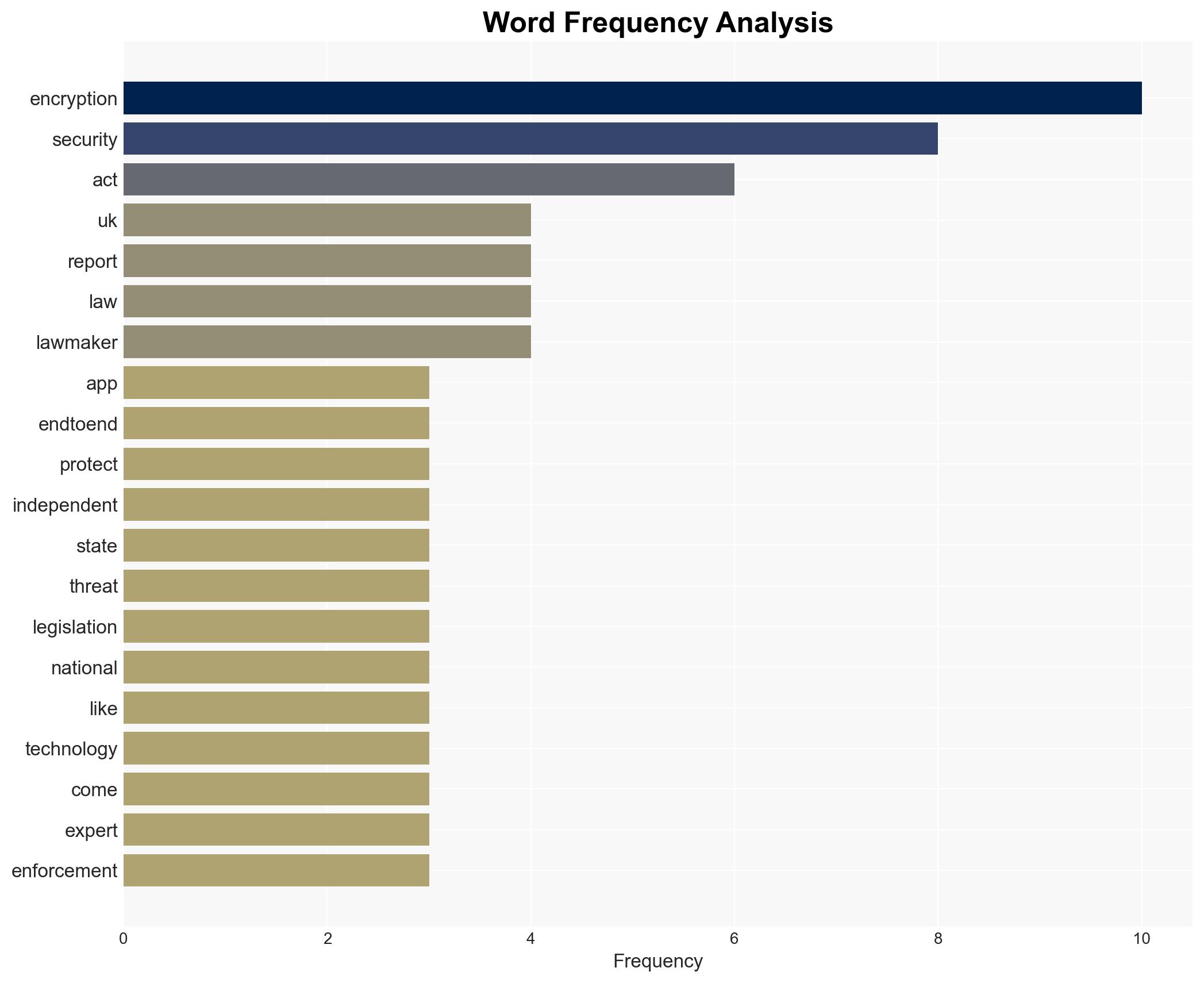
cybersecurity, national security, encryption, surveillance, privacy rights, tech regulation, UK legislation, cyber policy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us