Ukrainian Cyber Unit Deceives Russian Troops with Fake Starlink Service, Exposing Their Locations
Published on: 2026-02-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ukrainian forces say Russian troops paid them for a fake Starlink service that instead revealed battlefield locations
1. BLUF (Bottom Line Up Front)
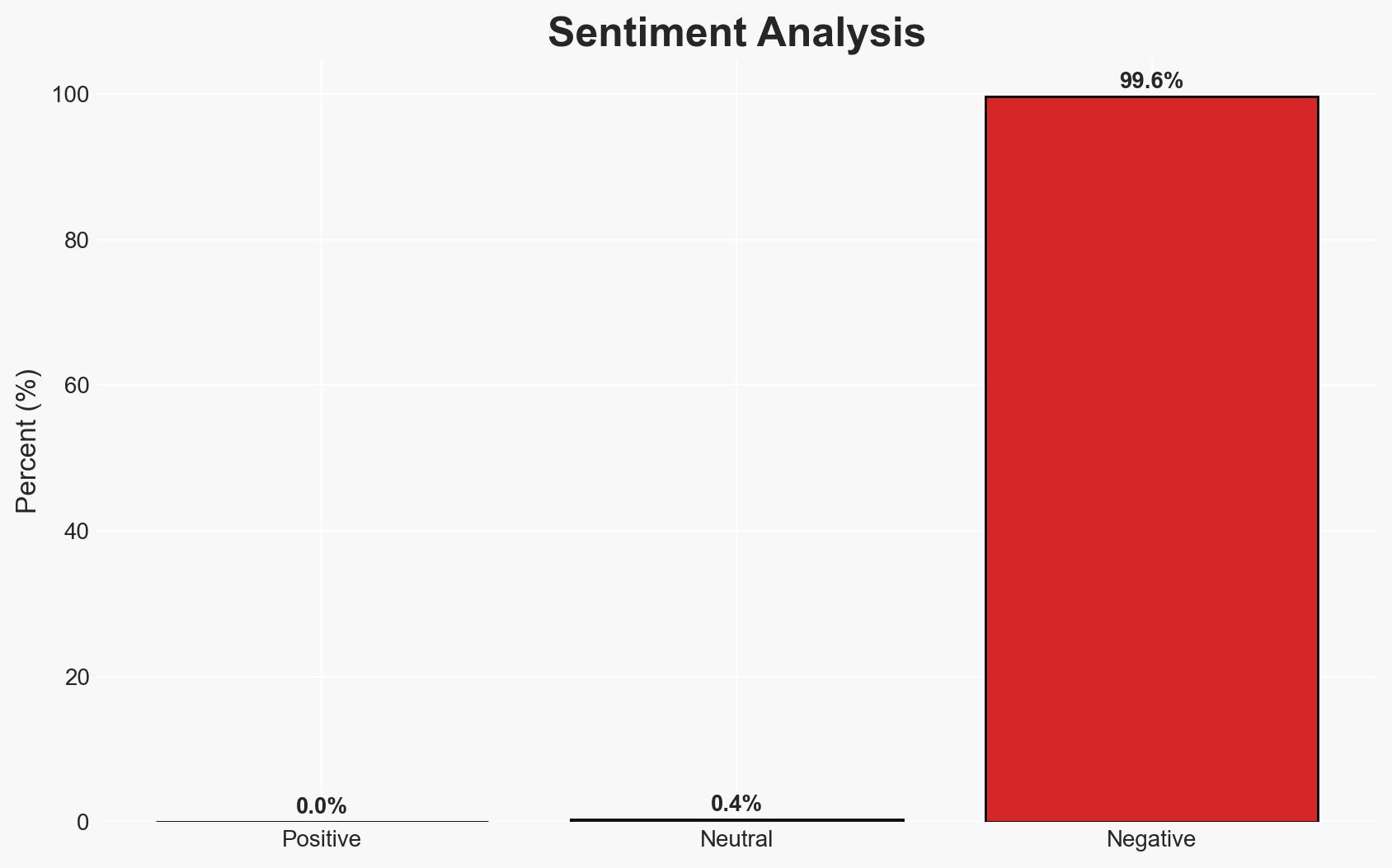
Ukrainian cyber operations have reportedly exploited Russian military reliance on Starlink services by creating a fake registration service that captured sensitive data from Russian troops. This operation highlights the vulnerabilities in Russian communications and the innovative use of cyber tactics by Ukrainian forces. The most likely hypothesis is that this operation was a deliberate Ukrainian strategy to gather intelligence, with moderate confidence in this assessment due to the lack of independent verification.
2. Competing Hypotheses
- Hypothesis A: The operation was a successful Ukrainian intelligence effort to exploit Russian reliance on Starlink for battlefield communications. Supporting evidence includes the reported data collection and financial transactions from Russian troops. Key uncertainties involve the authenticity of the screenshots and the exact scale of the operation.
- Hypothesis B: The operation is a Ukrainian disinformation campaign to undermine Russian military morale and credibility. This could be supported by the lack of independent verification and the potential for exaggeration in wartime propaganda. Contradicting evidence includes the detailed nature of the reported data collection.
- Assessment: Hypothesis A is currently better supported due to the specificity of the reported data and the involvement of known OSINT groups. Indicators that could shift this judgment include independent verification of the data or evidence of manipulation in the reported screenshots.
3. Key Assumptions and Red Flags
- Assumptions: Ukrainian forces have the capability to execute such cyber operations; Russian troops are reliant on Starlink for communications; the reported data is genuine and accurately reflects the operation’s outcomes.
- Information Gaps: Verification of the collected data’s authenticity and the operational impact on Russian forces.
- Bias & Deception Risks: Potential cognitive bias towards believing Ukrainian reports due to their strategic interest; risk of source bias from Ukrainian military statements; possible deception in the reported data to mislead Russian forces.
4. Implications and Strategic Risks
This development could lead to increased cyber operations and countermeasures between Ukraine and Russia, potentially escalating into broader cyber conflict. The operation underscores the strategic importance of communications security in modern warfare.
- Political / Geopolitical: Potential for increased tensions between Russia and Ukraine, with possible international ramifications if the operation is confirmed.
- Security / Counter-Terrorism: Heightened threat environment for Russian forces in Ukraine, potentially leading to increased operational security measures.
- Cyber / Information Space: Demonstrates the effectiveness of cyber deception tactics and could inspire similar operations in other conflicts.
- Economic / Social: Limited direct economic impact, but potential social implications if the operation affects Russian troop morale.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Verify the authenticity of the reported data; monitor Russian communications for changes in operational security measures; assess potential retaliatory cyber actions.
- Medium-Term Posture (1–12 months): Enhance cyber defense capabilities; strengthen partnerships with OSINT groups for intelligence sharing; develop counter-deception strategies.
- Scenario Outlook:
- Best: Ukrainian operations continue to disrupt Russian communications, leading to strategic advantages.
- Worst: Escalation into broader cyber conflict with significant collateral damage.
- Most-Likely: Continued cyber skirmishes with incremental impacts on the battlefield.
6. Key Individuals and Entities
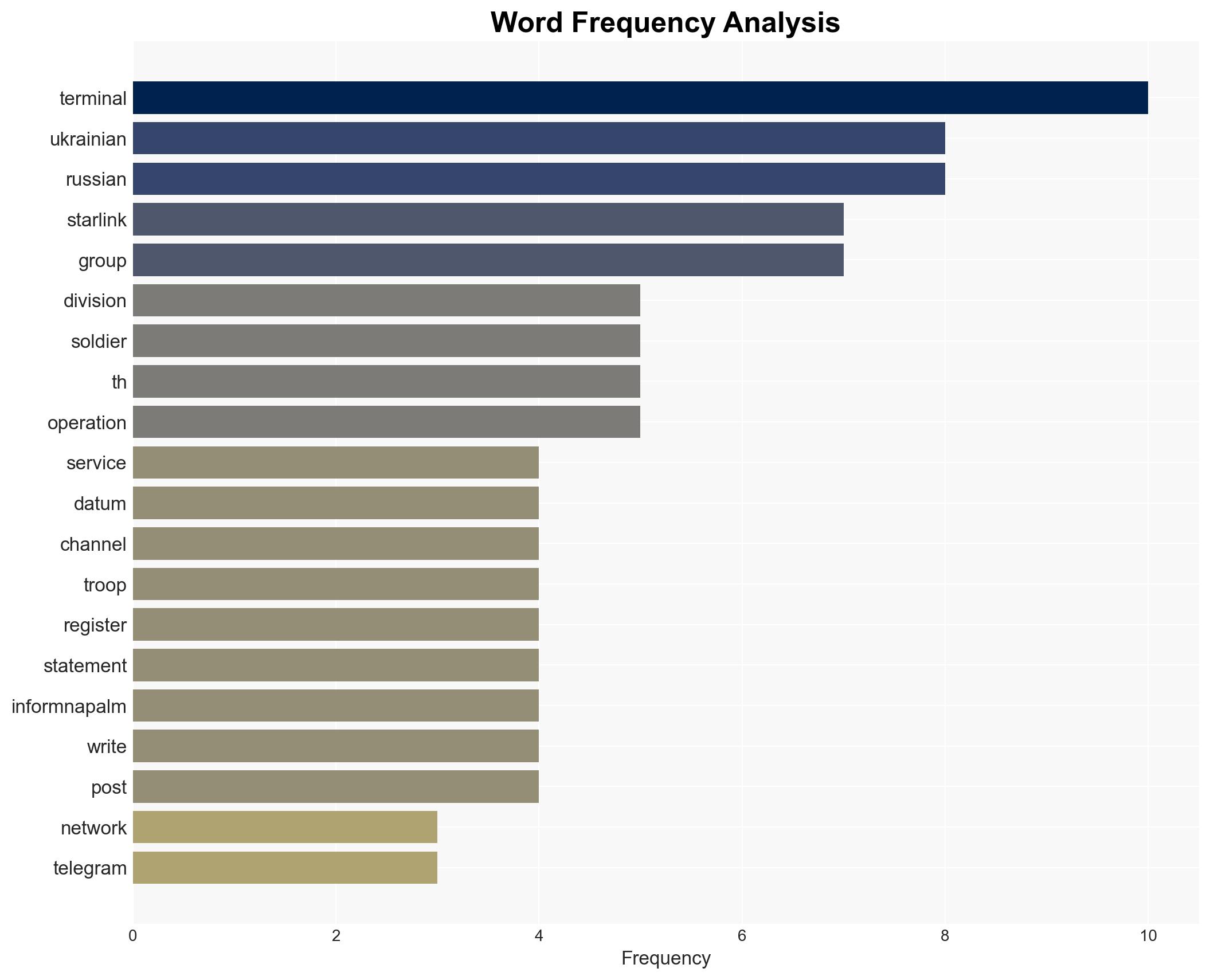
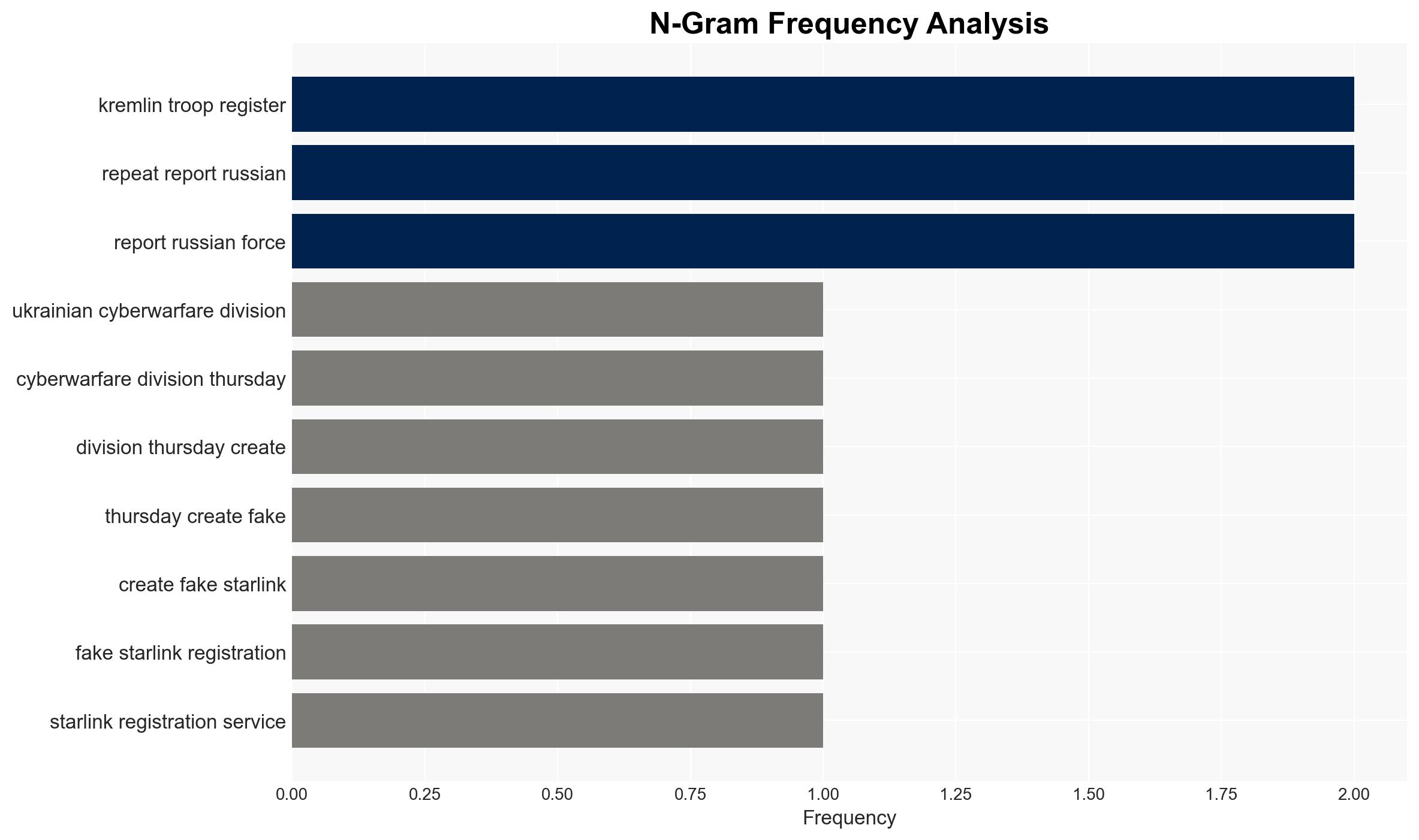
- 256th Cyber Assault Division
- InformNapalm
- MILITANT
- SpaceX
- Russian military forces
7. Thematic Tags
regional conflicts, cyber operations, military communications, OSINT, Ukraine conflict, deception tactics, Starlink, Russian military
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Regional Conflicts Briefs ·
Daily Summary ·
Support us