Ukrainian sentenced to 5 years for aiding North Korean infiltration of U.S. companies through identity theft
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ukrainian gets 5 years for helping North Koreans infiltrate US firms
1. BLUF (Bottom Line Up Front)
A Ukrainian national, Oleksandr Didenko, was sentenced for aiding North Korean IT workers to infiltrate U.S. companies using stolen identities. This operation highlights a significant cyber and economic threat posed by North Korean actors exploiting U.S. employment systems. The most likely hypothesis is that this is part of a broader, state-sponsored effort by North Korea to generate revenue and access sensitive information. Overall confidence in this assessment is moderate due to limited visibility into North Korean internal operations.
2. Competing Hypotheses
- Hypothesis A: The infiltration of U.S. firms by North Korean IT workers is a coordinated state-sponsored effort to generate revenue and potentially gather intelligence. This is supported by the involvement of North Korean operatives and the scale of the operation. However, the exact level of state control or direction remains uncertain.
- Hypothesis B: The operation is primarily financially motivated by individual actors, with limited direct state involvement. While North Korea benefits from the revenue, the decentralized nature of the operation and the involvement of non-state actors like Didenko suggest a possible lack of direct state orchestration.
- Assessment: Hypothesis A is currently better supported due to the structured nature of the operation and historical patterns of North Korean cyber activities. Indicators such as increased sophistication in identity theft or a shift in targeting could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: North Korean state actors are involved in directing or benefiting from the operation; U.S. companies lack sufficient defenses against such infiltration; the operation’s primary goal is revenue generation.
- Information Gaps: The extent of North Korean government involvement; the full scope of compromised U.S. companies; detailed operational methods used by North Korean IT workers.
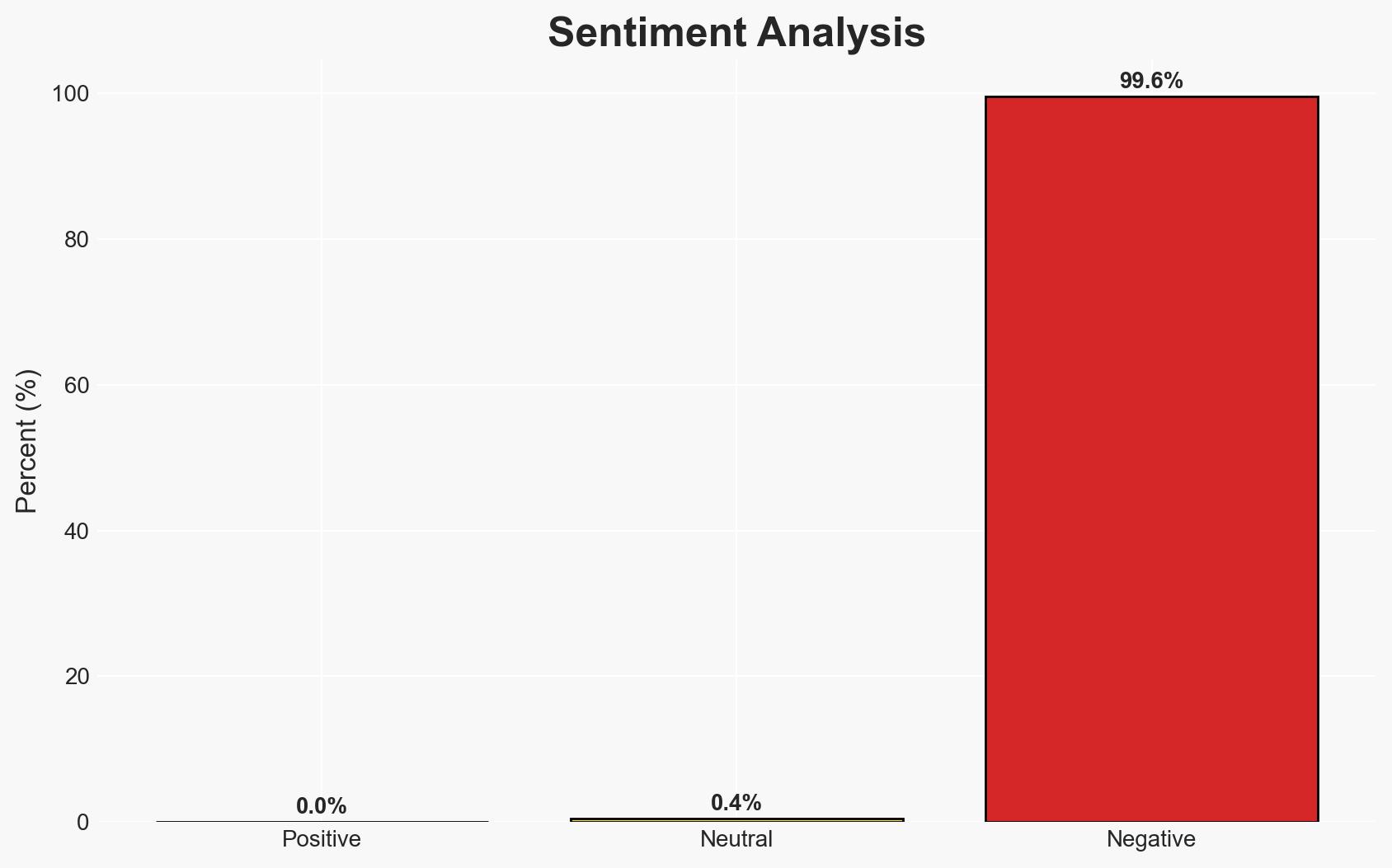
- Bias & Deception Risks: Potential bias in attributing all activities to state sponsorship; reliance on public court documents which may omit classified details; possible deception by North Korean actors to obscure true objectives.
4. Implications and Strategic Risks
This development could lead to increased tensions between the U.S. and North Korea, particularly if further state involvement is confirmed. The operation may prompt U.S. companies to enhance cybersecurity measures, impacting North Korean revenue streams.
- Political / Geopolitical: Potential for increased sanctions or diplomatic actions against North Korea and associated entities.
- Security / Counter-Terrorism: Heightened alert for similar infiltration tactics in other sectors; potential for retaliatory cyber operations.
- Cyber / Information Space: Increased focus on securing freelance and remote work platforms; potential for escalated cyber conflicts.
- Economic / Social: Disruption in the IT job market; potential loss of trust in remote work platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of freelance platforms; increase awareness campaigns for companies on identity verification; initiate diplomatic dialogues with allies to address the threat.
- Medium-Term Posture (1–12 months): Develop partnerships with tech firms to improve identity verification technologies; strengthen international cooperation on cybercrime enforcement.
- Scenario Outlook:
- Best: Successful disruption of North Korean operations with minimal economic impact.
- Worst: Escalation into broader cyber conflicts with significant economic and security repercussions.
- Most-Likely: Continued low-level operations with periodic disruptions and sanctions.
6. Key Individuals and Entities
- Oleksandr Didenko – Ukrainian national involved in the scheme.
- Christina Marie Chapman – Operated a “laptop farm” in Arizona.
- Famous Chollima (WageMole) – North Korean state-backed group.
- James Barnacle – FBI Assistant Director in Charge, New York Field Office.
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, identity theft, North Korea, sanctions, IT security, state-sponsored operations, economic infiltration
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us