UK’s digital future hinges on addressing critical legacy IT vulnerabilities in public sector systems.
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Addressing UK’s Technical Debt is Only Way to Secure Country’s Digital Future
1. BLUF (Bottom Line Up Front)
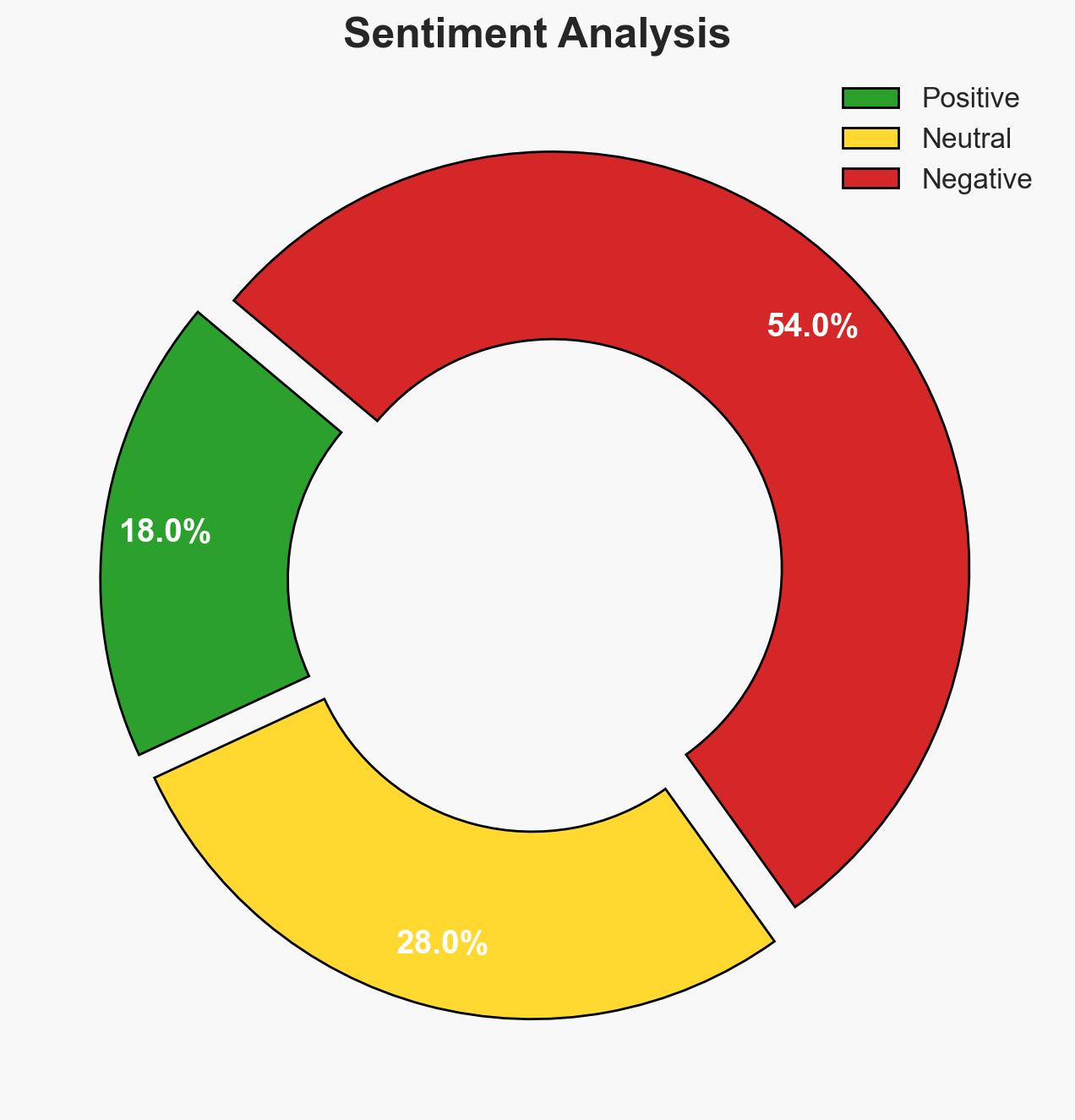
The UK’s reliance on outdated IT infrastructure poses a significant cybersecurity risk, potentially undermining national resilience efforts. The most likely hypothesis is that without strategic modernization, critical services remain vulnerable to cyber threats, impacting national security and public trust. Confidence in this assessment is moderate due to existing data on outdated systems but limited insight into specific threat actor intentions.
2. Competing Hypotheses
- Hypothesis A: The UK’s outdated IT infrastructure significantly increases vulnerability to cyberattacks, necessitating immediate modernization efforts. Supporting evidence includes the high percentage of legacy systems in use and the increased frequency of cyberattacks. Key uncertainties involve the specific capabilities and intentions of potential adversaries exploiting these vulnerabilities.
- Hypothesis B: The current IT infrastructure, despite being outdated, can be sufficiently secured through targeted risk management and incremental upgrades, avoiding the need for a complete overhaul. This hypothesis is supported by the potential for real-time inventories and lifecycle assessments to mitigate risks. However, it contradicts the urgency implied by the high percentage of outdated systems.
- Assessment: Hypothesis A is currently better supported due to the substantial evidence of widespread outdated systems and the inherent risks they pose. Indicators that could shift this judgment include successful implementation of comprehensive risk management strategies or significant improvements in cyber defense capabilities.
3. Key Assumptions and Red Flags
- Assumptions: The percentage of outdated systems accurately reflects the overall vulnerability; adversaries are actively seeking to exploit these vulnerabilities; modernization efforts will effectively reduce risk.
- Information Gaps: Detailed intelligence on adversary capabilities and intentions regarding exploiting UK infrastructure; specific timelines and resources required for modernization.
- Bias & Deception Risks: Potential bias from stakeholders advocating for modernization investments; risk of underestimating adversary capabilities or overestimating the effectiveness of incremental upgrades.
4. Implications and Strategic Risks
Failure to address the UK’s technical debt could lead to increased vulnerability to cyberattacks, impacting national security and public trust. Over time, this could erode confidence in public sector services and strain international partnerships.
- Political / Geopolitical: Potential strain on international relations if allies perceive the UK as a weak link in cybersecurity.
- Security / Counter-Terrorism: Increased risk of cyberattacks targeting critical infrastructure, potentially facilitating broader terrorist activities.
- Cyber / Information Space: Heightened threat of data breaches and information manipulation, undermining public trust and operational integrity.
- Economic / Social: Potential economic impact from disrupted services and increased costs associated with emergency responses to cyber incidents.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of current IT infrastructure, prioritize systems for immediate risk mitigation, and enhance monitoring of potential cyber threats.
- Medium-Term Posture (1–12 months): Develop a strategic plan for phased modernization, invest in cybersecurity training for IT staff, and strengthen international cybersecurity partnerships.
- Scenario Outlook:
- Best: Successful modernization reduces vulnerabilities, enhancing national security and public trust.
- Worst: Delays in modernization lead to significant cyber incidents, damaging critical infrastructure and public confidence.
- Most-Likely: Incremental improvements mitigate some risks, but full modernization is required for long-term resilience.
6. Key Individuals and Entities
- Rob Lay, Director of Solutions Engineering UK&I at Cisco
- UK Government Departments (specific departments not clearly identifiable from open sources in this snippet)
7. Thematic Tags
cybersecurity, national security, IT infrastructure, risk management, public sector, modernization, resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us