Under Armour faces class action lawsuit as data of 72 million customers reportedly surfaces online
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Under Armour ransomware breach data of 72 million customers appears on the dark web
1. BLUF (Bottom Line Up Front)
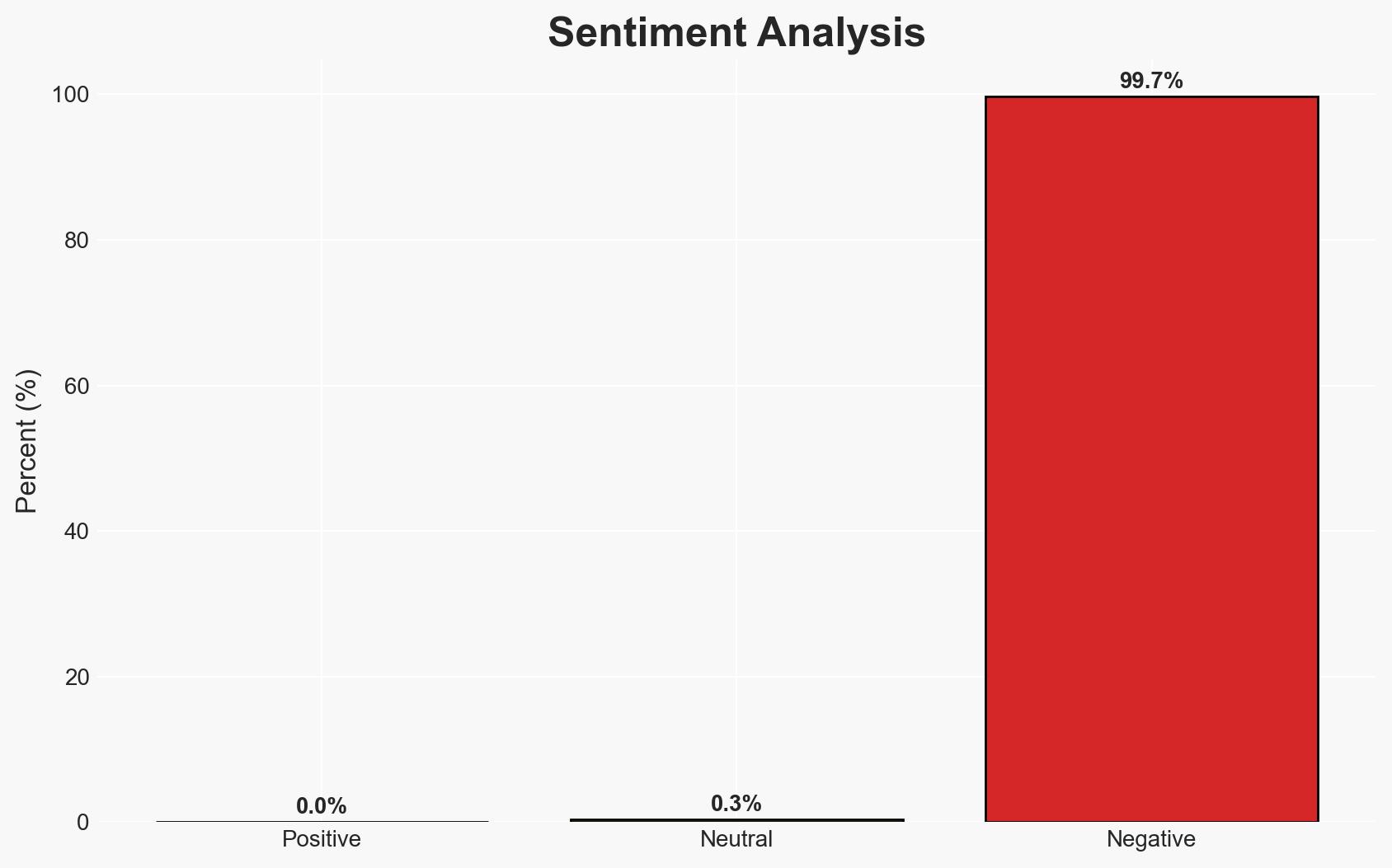
The Under Armour data breach, attributed to the Everest ransomware group, has resulted in the exposure of sensitive information of approximately 72 million customers. The breach is likely severe, with data now circulating on the dark web. This assessment is made with moderate confidence due to corroborated claims from multiple sources and the visible presence of data on underground forums.
2. Competing Hypotheses
- Hypothesis A: The breach is extensive, and a significant portion of Under Armour’s customer data is compromised and available on the dark web. This is supported by the Everest group’s claims, the presence of data on hacker forums, and the lawsuit alleging large-scale data exfiltration. However, the exact extent of the breach remains uncertain due to limited official confirmation.
- Hypothesis B: The breach is less severe than claimed, with only a subset of data exposed. This is supported by Under Armour’s cautious public statements and the possibility of exaggeration by the ransomware group. However, the lack of detailed denial from Under Armour weakens this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the corroborated presence of data on multiple platforms and the lack of strong counter-evidence from Under Armour. Key indicators that could shift this judgment include official confirmation of the breach’s scope or credible denial of data authenticity.
3. Key Assumptions and Red Flags
- Assumptions: The data on hacker forums is authentic; the Everest group had access to Under Armour’s systems; Under Armour’s public statements are strategically cautious.
- Information Gaps: Specific details on the breach’s technical aspects, the exact volume of compromised data, and Under Armour’s internal response measures.
- Bias & Deception Risks: Potential bias in corporate communications aiming to minimize reputational damage; possible exaggeration by cybercriminals to enhance their leverage.
4. Implications and Strategic Risks
The breach could lead to increased scrutiny on corporate data protection practices and influence future regulatory measures. It may also embolden ransomware groups if perceived as successful.
- Political / Geopolitical: Potential for increased regulatory pressure on data protection standards globally.
- Security / Counter-Terrorism: Heightened risk of similar attacks on other corporations, potentially increasing the operational tempo of ransomware groups.
- Cyber / Information Space: Possible increase in cybercriminal activity and data trading on dark web forums.
- Economic / Social: Potential financial losses for Under Armour and erosion of customer trust, impacting brand reputation and market position.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web forums for data leaks, engage with cybersecurity firms for breach analysis, and communicate transparently with affected customers.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity infrastructure, conduct regular security audits, and develop partnerships with law enforcement for threat intelligence sharing.
- Scenario Outlook:
- Best Case: Breach impact is contained, and Under Armour successfully mitigates reputational damage.
- Worst Case: Further data leaks occur, leading to significant financial and reputational harm.
- Most-Likely: Continued legal and regulatory challenges, with moderate impact on customer trust and corporate operations.
6. Key Individuals and Entities
- Under Armour
- Everest Ransomware Group
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, ransomware, corporate risk, dark web, data protection, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us