Under the Radar How Non-Web Protocols Are Redefining the Attack Surface – Zscaler.com
Published on: 2025-10-16
Intelligence Report: Under the Radar How Non-Web Protocols Are Redefining the Attack Surface – Zscaler.com
1. BLUF (Bottom Line Up Front)
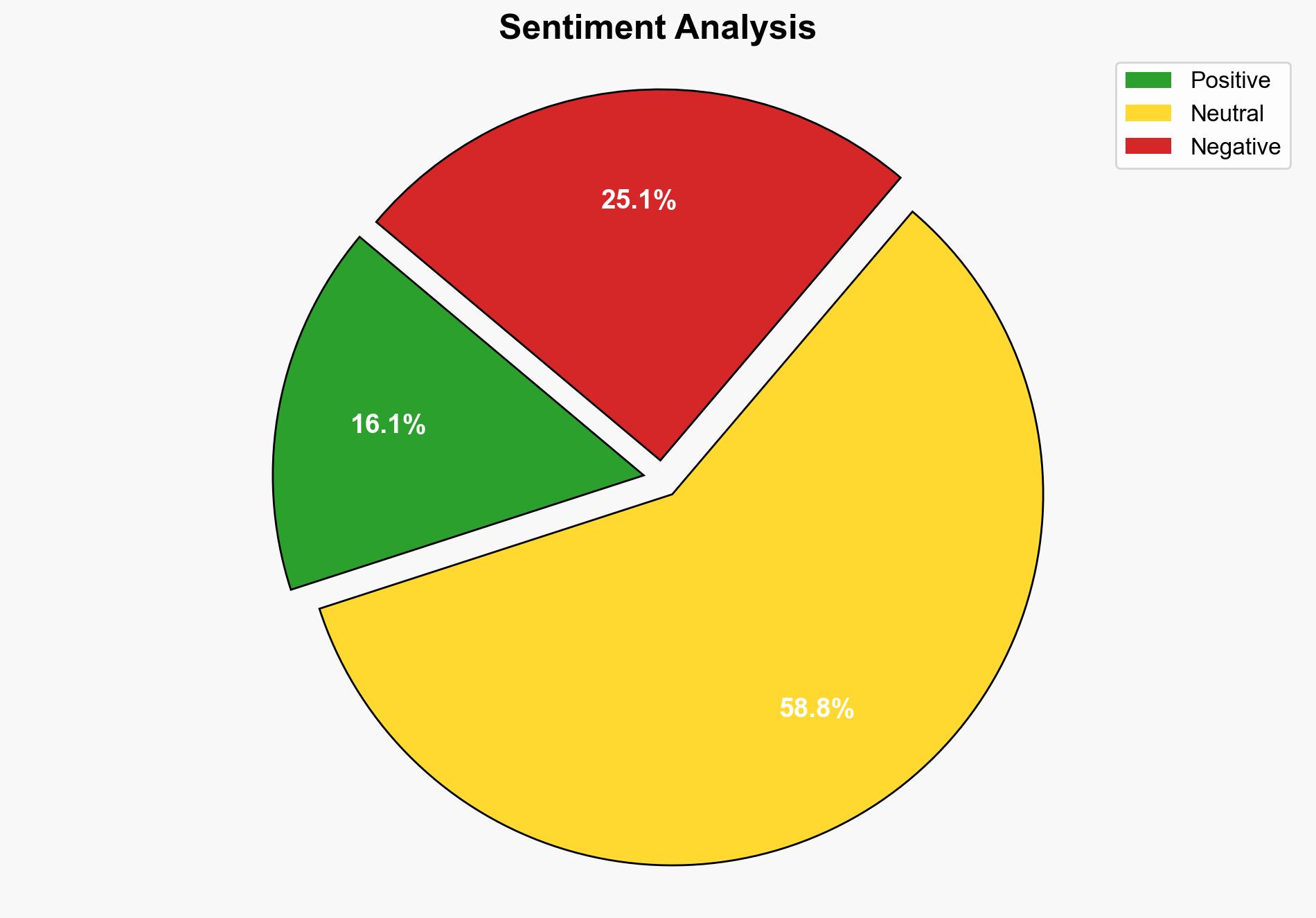
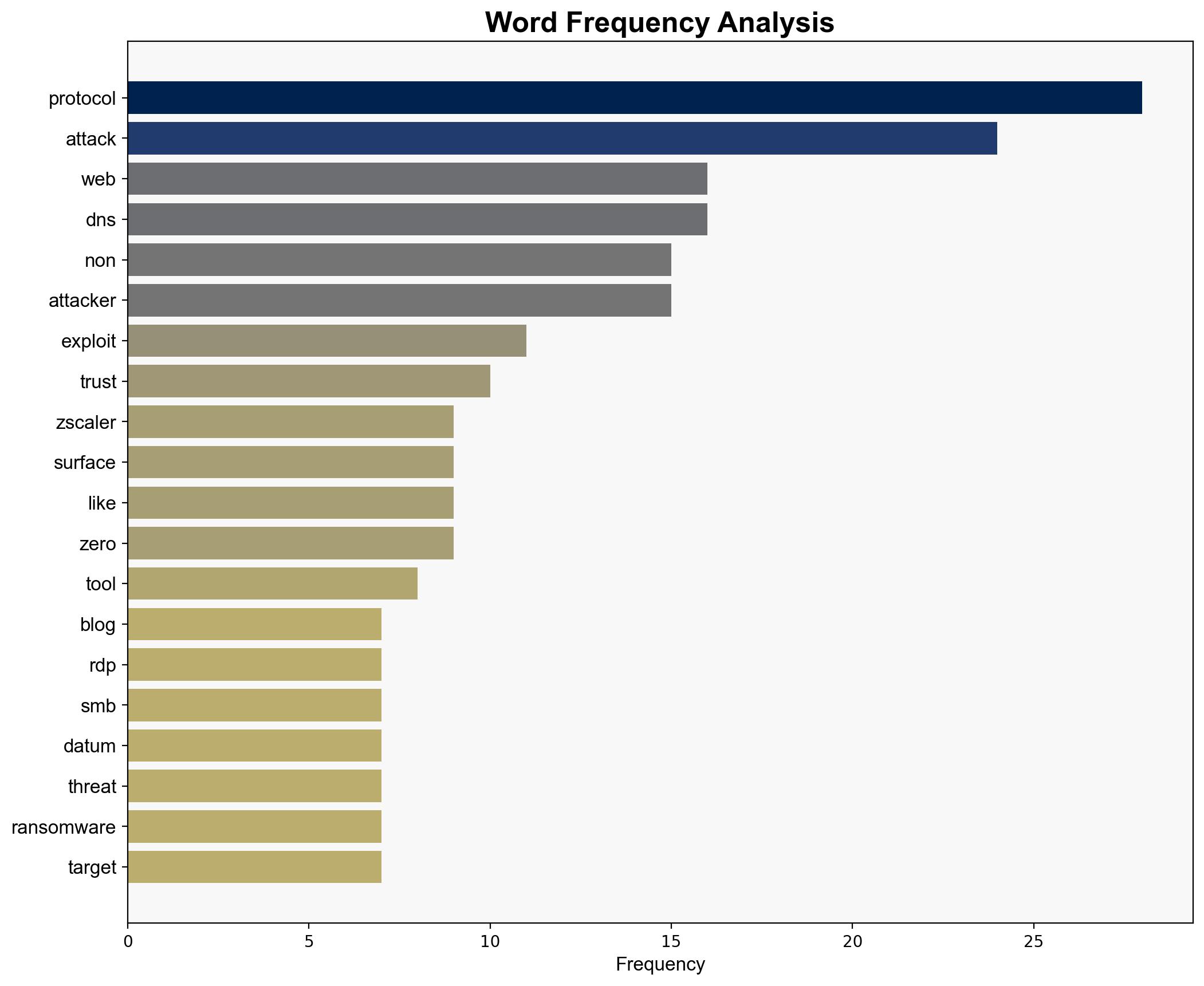
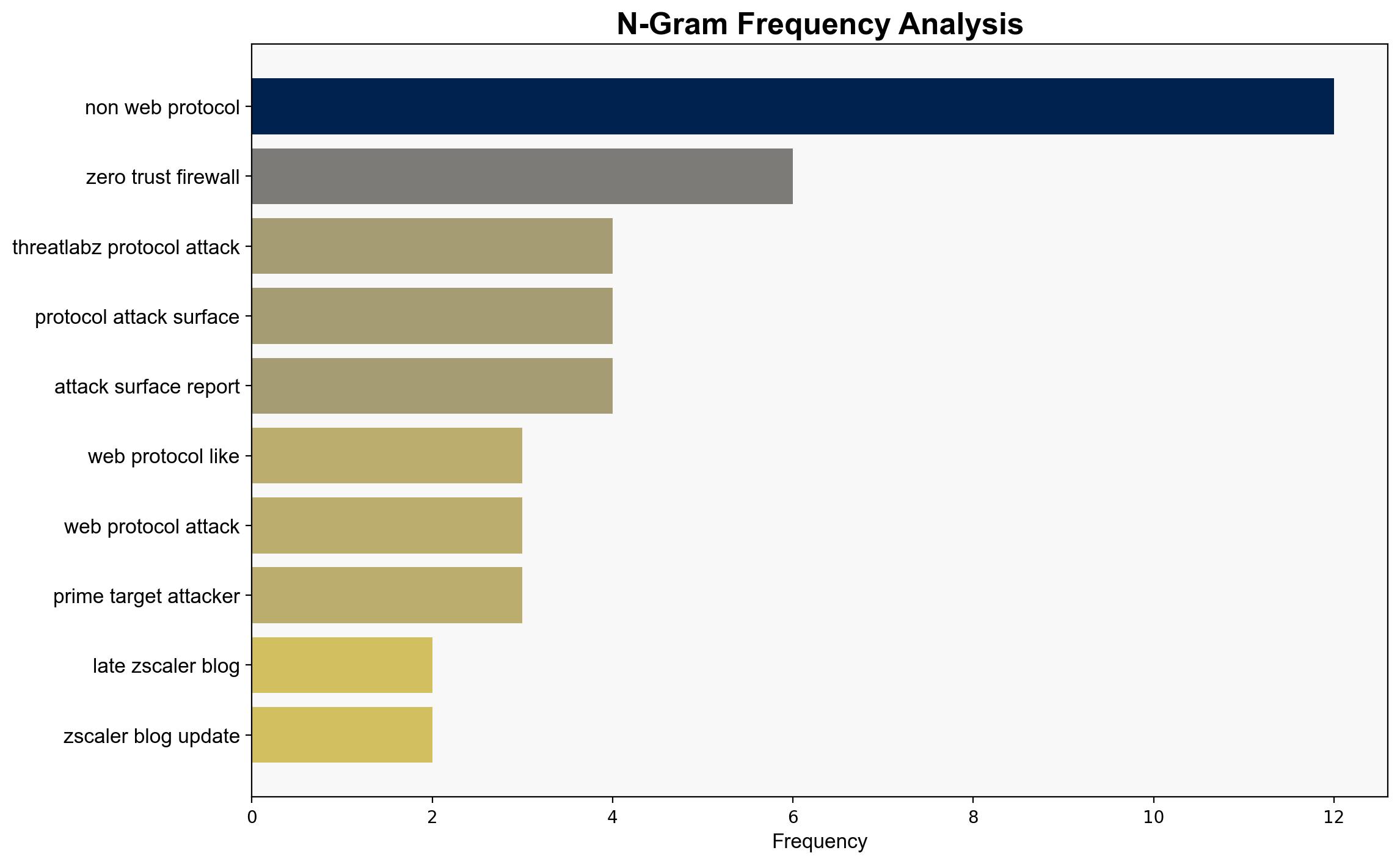
Non-web protocols are increasingly exploited by cyber attackers, creating a significant shift in the attack surface that traditional defenses fail to address. The most supported hypothesis suggests that attackers are leveraging these protocols to bypass conventional security measures, necessitating a strategic pivot towards more comprehensive monitoring and defense strategies. Confidence Level: High. Recommended Action: Enhance detection capabilities for non-web protocols and update security frameworks to address these emerging threats.
2. Competing Hypotheses
Hypothesis 1: Attackers are primarily exploiting non-web protocols due to their inherent vulnerabilities and the lack of adequate monitoring tools, making them an attractive target for data exfiltration and command-and-control activities.
Hypothesis 2: The surge in non-web protocol attacks is a temporary trend driven by recent vulnerabilities and will decline as organizations patch systems and update security measures.
3. Key Assumptions and Red Flags
Hypothesis 1 Assumptions: Non-web protocols are less monitored, and current security tools are inadequate. Attackers have the capability to exploit these protocols effectively.
Hypothesis 2 Assumptions: Organizations will respond quickly to patch vulnerabilities, and the trend will diminish as a result.
Red Flags: Over-reliance on patching as a solution, underestimation of attackers’ adaptability, and potential biases in threat reporting.
4. Implications and Strategic Risks
The exploitation of non-web protocols could lead to increased data breaches, ransomware attacks, and persistent threats within critical infrastructure sectors. Economic disruptions, loss of consumer trust, and geopolitical tensions could escalate if these vulnerabilities are not addressed. The potential for cascading effects is high, particularly if attackers leverage these protocols for lateral movement within networks.
5. Recommendations and Outlook
- Invest in advanced monitoring tools specifically designed for non-web protocols.
- Conduct regular security audits and vulnerability assessments focused on non-web protocols.
- Scenario Projections:
- Best Case: Organizations rapidly adapt, reducing the attack surface and mitigating risks.
- Worst Case: Continued exploitation leads to significant breaches and economic impact.
- Most Likely: A gradual increase in awareness and adaptation, with intermittent breaches.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Key entities include Zscaler and its ThreatLabZ research team, which provides critical insights into the evolving threat landscape.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus