Undercover Operation Foils Major Terror Plot Against Jewish Community in Greater Manchester
Published on: 2025-12-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: How gun plot targeting Jewish community was stopped
1. BLUF (Bottom Line Up Front)
The thwarting of a planned terrorist attack targeting the Jewish community in Greater Manchester highlights the effectiveness of undercover operations in counter-terrorism efforts. The operation, involving an undercover operative, prevented what could have been a highly lethal attack. This incident underscores the persistent threat posed by individuals inspired by extremist ideologies. Overall confidence in this assessment is moderate due to potential information gaps regarding the broader network and motivations.
2. Competing Hypotheses
- Hypothesis A: The plot was primarily driven by Saadaoui’s personal radicalization and admiration for IS figures, with limited external support. Evidence includes his expressed admiration for IS and the nature of his interactions with the undercover operative. However, uncertainties remain about potential undisclosed networks or supporters.
- Hypothesis B: The plot was part of a larger, coordinated effort involving multiple actors beyond those identified. This hypothesis is less supported due to the lack of evidence indicating broader organizational involvement, but cannot be entirely ruled out without further intelligence.
- Assessment: Hypothesis A is currently better supported given the available evidence of Saadaoui’s individual radicalization and the absence of clear links to a larger network. Indicators such as discovery of additional conspirators or communications could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Saadaoui acted primarily on personal motivations; the undercover operative’s information is reliable; the plot was not part of a larger coordinated effort.
- Information Gaps: Details on any potential broader network or additional conspirators; full extent of Saadaoui’s communications and connections.
- Bias & Deception Risks: Potential for confirmation bias in assessing the threat as isolated; reliance on a single undercover source may introduce bias or deception risks.
4. Implications and Strategic Risks
This development could influence future counter-terrorism strategies and community relations. It may also affect public perceptions of safety and security.
- Political / Geopolitical: Potential for increased scrutiny on immigration and integration policies; heightened tensions between communities.
- Security / Counter-Terrorism: Reinforces the need for robust intelligence operations and community engagement to prevent radicalization.
- Cyber / Information Space: Monitoring of online platforms for extremist content remains crucial; potential for increased cyber surveillance.
- Economic / Social: Possible impacts on local business and tourism due to perceived security threats; community cohesion challenges.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of extremist activities online; increase community outreach to improve trust and cooperation.
- Medium-Term Posture (1–12 months): Develop partnerships with community leaders to counter radicalization; invest in intelligence capabilities and undercover operations.
- Scenario Outlook:
- Best: Successful integration of counter-radicalization measures reduces threat levels.
- Worst: Emergence of new plots due to undetected networks or increased radicalization.
- Most-Likely: Continued isolated threats with periodic disruptions by law enforcement.
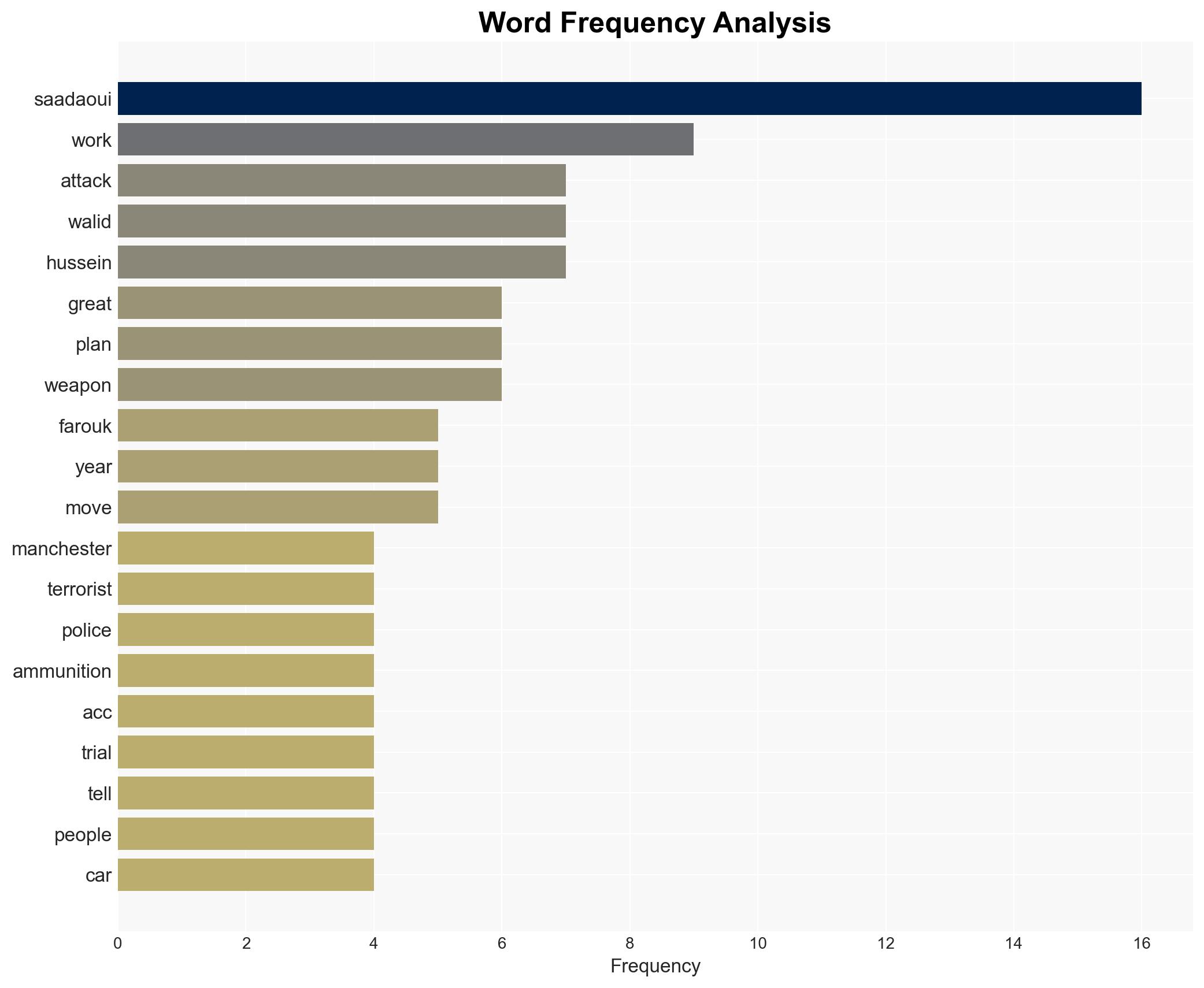
6. Key Individuals and Entities
- Walid Saadaoui
- Amar Hussein
- Farouk (undercover operative)
- Greater Manchester Police
7. Thematic Tags
national security threats, counter-terrorism, radicalization, undercover operations, extremist ideology, community relations, intelligence operations, security threats
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us