University of Sydney alerts community after personal data breach from compromised code repository
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Sydney Uni data goes walkabout after criminals raid code repo
1. BLUF (Bottom Line Up Front)
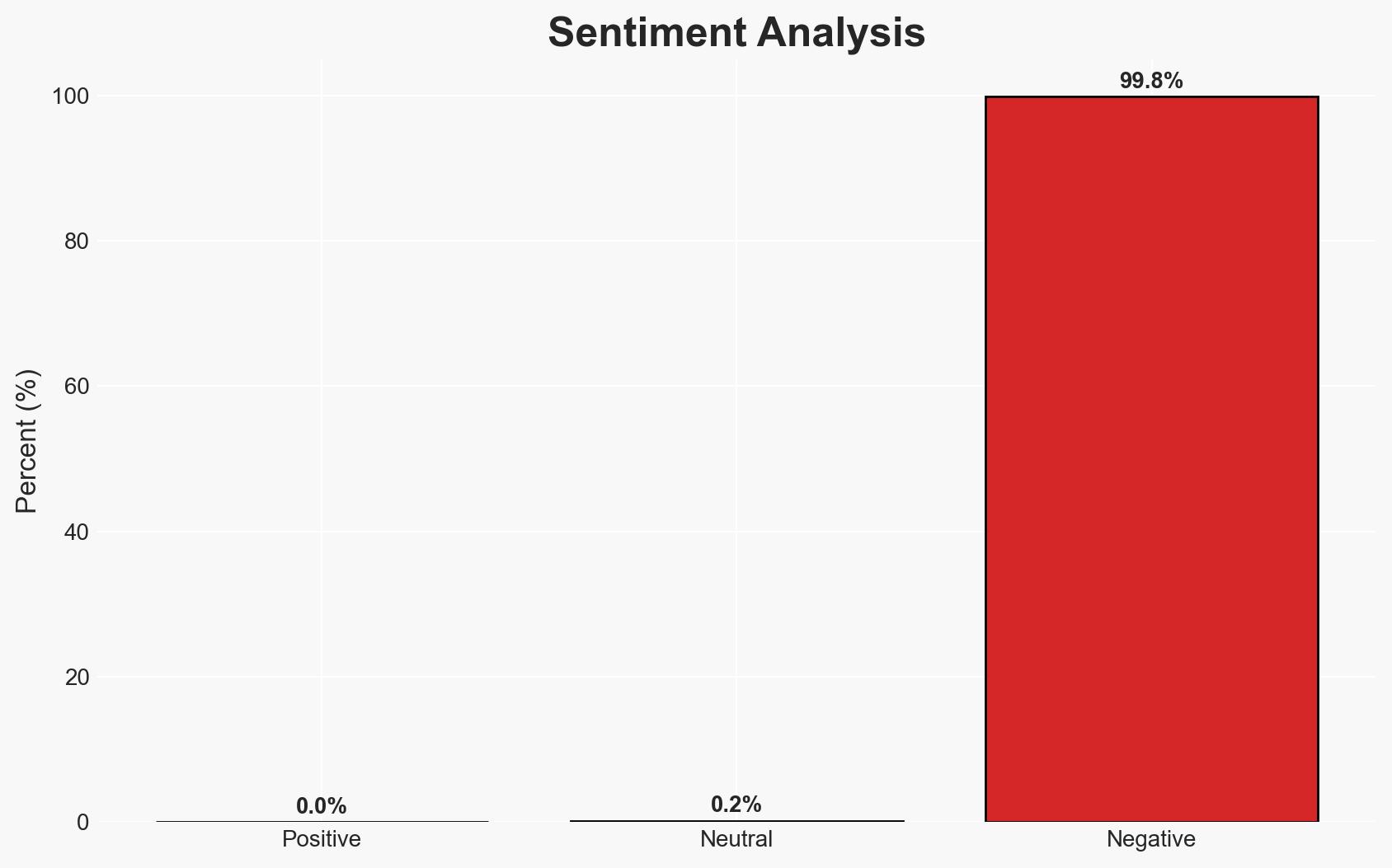
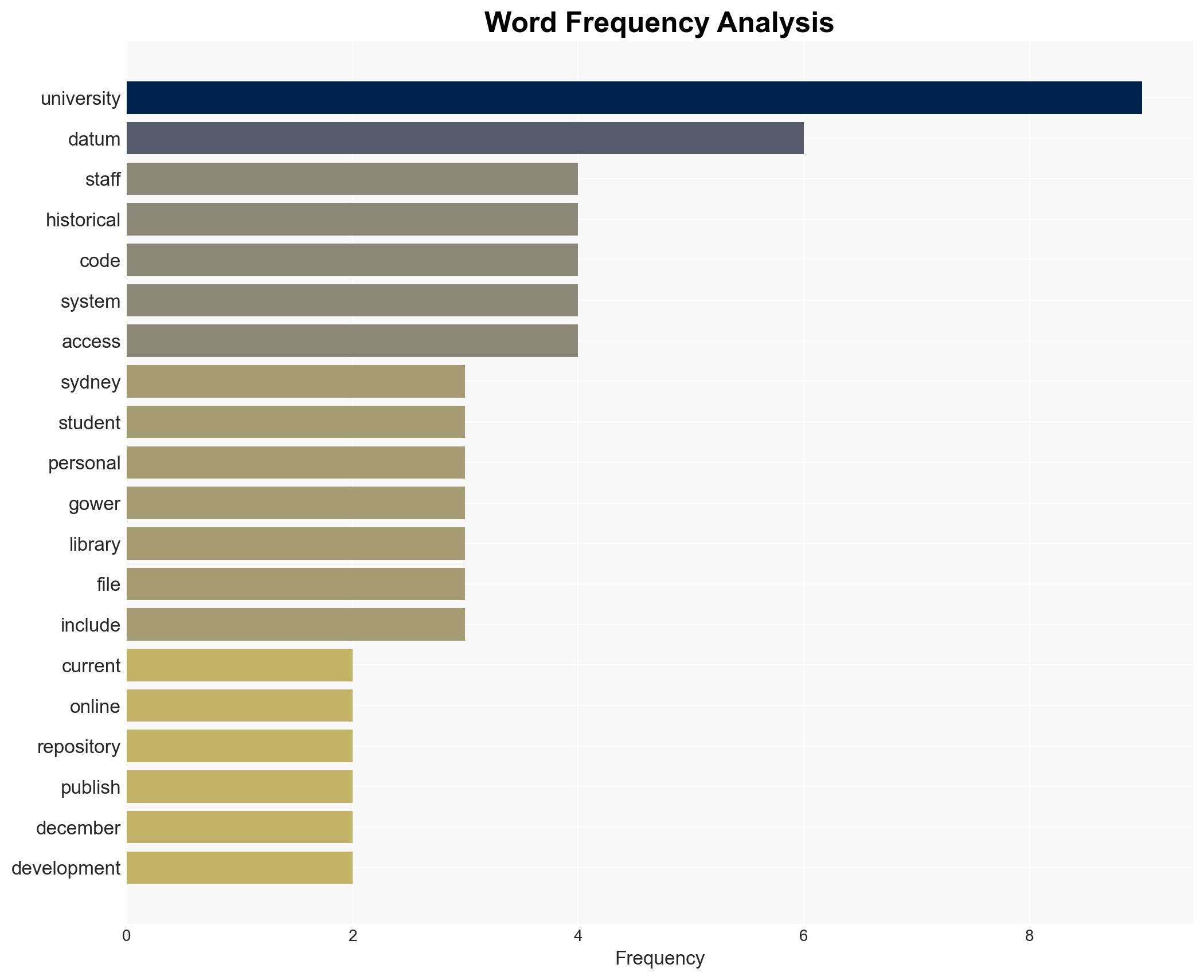
The University of Sydney experienced a data breach involving historical personal data from its code repository, affecting approximately 27,500 individuals. The breach appears limited to a single platform, with no evidence of data misuse so far. The most likely hypothesis is that the breach was opportunistic rather than targeted. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was an opportunistic attack, exploiting vulnerabilities in the university’s code repository. Supporting evidence includes the lack of immediate data misuse and the historical nature of the data. Key uncertainties include the attackers’ identity and intent.
- Hypothesis B: The breach was a targeted attack aimed at obtaining specific personal information for malicious purposes. Contradicting evidence includes the absence of data misuse and the broad scope of affected individuals, which suggests a lack of specific targeting.
- Assessment: Hypothesis A is currently better supported due to the lack of evidence indicating targeted data misuse and the nature of the data involved. Indicators that could shift this judgment include evidence of data being used in identity theft or other malicious activities.
3. Key Assumptions and Red Flags
- Assumptions: The breach was not part of a coordinated campaign; the data has not been used maliciously; the university’s response measures are adequate; the attackers did not access other systems.
- Information Gaps: Identity and motives of the attackers; potential vulnerabilities in other university systems; full extent of data accessed.
- Bias & Deception Risks: Potential underestimation of the threat due to lack of immediate data misuse; reliance on university-provided information which may be biased towards minimizing perceived impact.
4. Implications and Strategic Risks
This incident highlights vulnerabilities in academic institutions’ data management practices, with potential long-term reputational and security implications.
- Political / Geopolitical: Limited direct impact, but could influence policy on data protection in educational institutions.
- Security / Counter-Terrorism: Minimal immediate impact, but underscores the need for improved cybersecurity in non-traditional targets.
- Cyber / Information Space: Potential for increased scrutiny on academic cybersecurity practices; may prompt similar attacks if vulnerabilities are perceived.
- Economic / Social: Potential reputational damage to the university; could affect student and staff trust and enrollment.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation; enhance monitoring of affected individuals’ data; review and secure other repositories.
- Medium-Term Posture (1–12 months): Develop a comprehensive cybersecurity strategy; engage with cybersecurity experts; enhance staff training on data protection.
- Scenario Outlook: Best: No misuse of data occurs, and security is strengthened. Worst: Data is used for identity theft, leading to reputational damage. Most-Likely: Limited misuse, with increased focus on cybersecurity improvements.
6. Key Individuals and Entities
- Nicole Gower, Vice President of Operations, University of Sydney
- University of Sydney
- External cybersecurity partners (not specified)
7. Thematic Tags
cybersecurity, data breach, higher education, personal data protection, information security, risk management, incident response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us