US CISA adds a Google Chromium V8 flaw to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
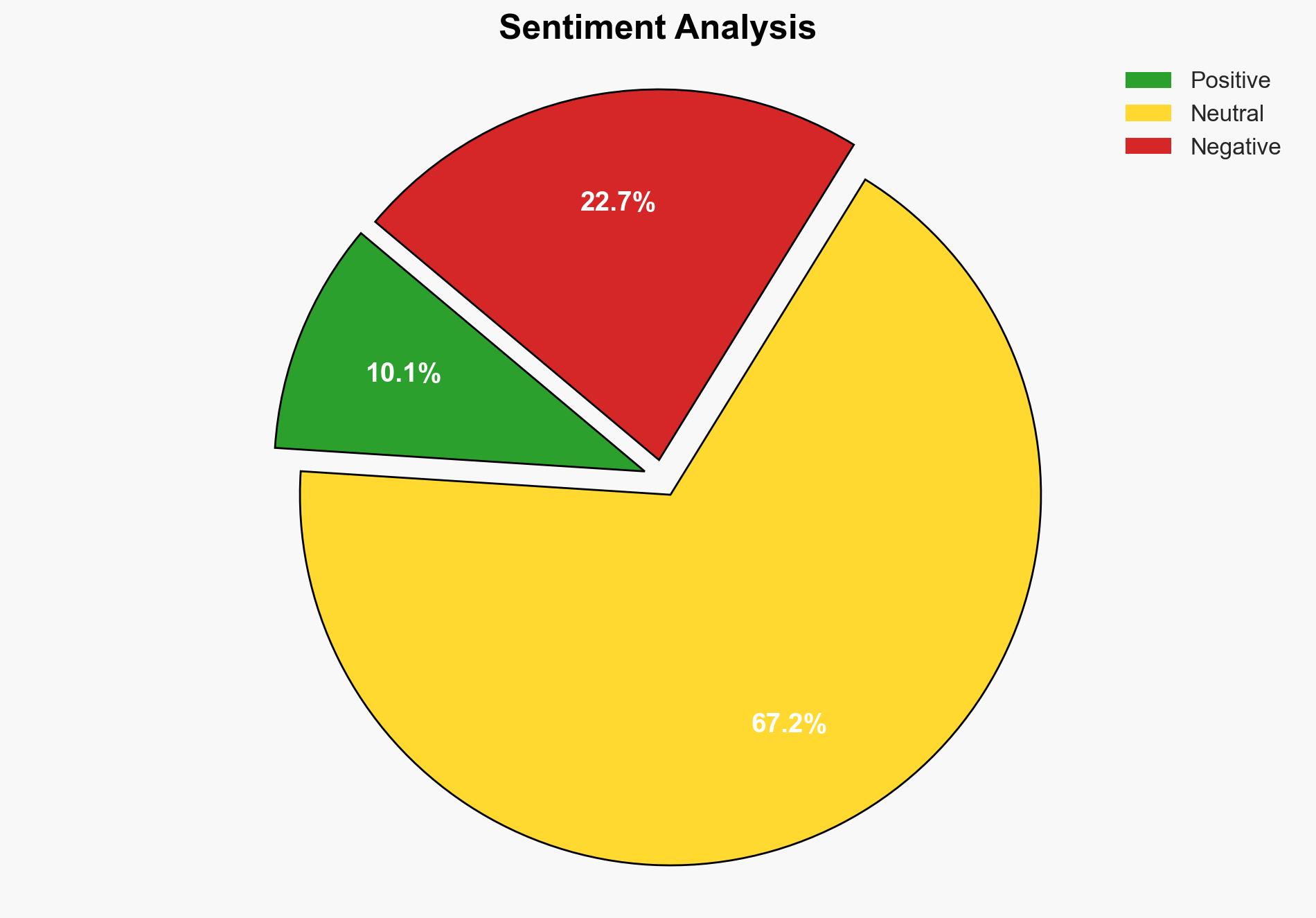
The addition of a Google Chromium V8 flaw to the CISA Known Exploited Vulnerabilities catalog highlights a significant cybersecurity threat, potentially exploited by nation-state actors and commercial spyware vendors. The most supported hypothesis is that this vulnerability is actively being exploited by sophisticated threat actors, necessitating immediate mitigation efforts. Confidence Level: High. Recommended action includes prioritizing patching efforts and enhancing monitoring for exploitation attempts.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is actively being exploited by nation-state actors and commercial spyware vendors to conduct targeted attacks.
Hypothesis 2: The vulnerability is primarily being exploited by opportunistic cybercriminals for financial gain rather than targeted espionage.
The first hypothesis is more likely due to the involvement of Google’s Threat Analysis Group, which typically investigates sophisticated threats, and the nature of the vulnerability, which allows for remote code execution, a common goal for espionage activities.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerability is being exploited in the wild as reported by credible sources like Google’s Threat Analysis Group. The assumption that nation-state actors are involved is based on historical patterns of behavior.
Red Flags: The lack of detailed information on the specific attacks and targets could indicate potential information withholding or deception by involved parties.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant data breaches, intellectual property theft, and disruption of critical infrastructure. Politically, it could escalate tensions between nations if state-sponsored actors are implicated. Economically, affected organizations could face substantial financial losses and reputational damage.
5. Recommendations and Outlook
- Actionable Steps: Organizations should immediately apply the latest security patches, enhance network monitoring for unusual activity, and conduct security audits to identify potential exploitation.
- Best-case Scenario: Rapid patching and mitigation efforts prevent widespread exploitation, minimizing impact.
- Worst-case Scenario: Delayed response leads to significant breaches and geopolitical tensions.
- Most-likely Scenario: A mix of successful mitigations and isolated incidents of exploitation occur, with ongoing monitoring required.
6. Key Individuals and Entities
Clément Lecigne: Member of Google’s Threat Analysis Group, involved in investigating the vulnerability.
Pierluigi Paganini: Author reporting on the vulnerability.
Entities: U.S. Cybersecurity and Infrastructure Security Agency (CISA), Google, Google’s Threat Analysis Group.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us