US CISA adds Fortinet FortiWeb flaw to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-07-20

AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
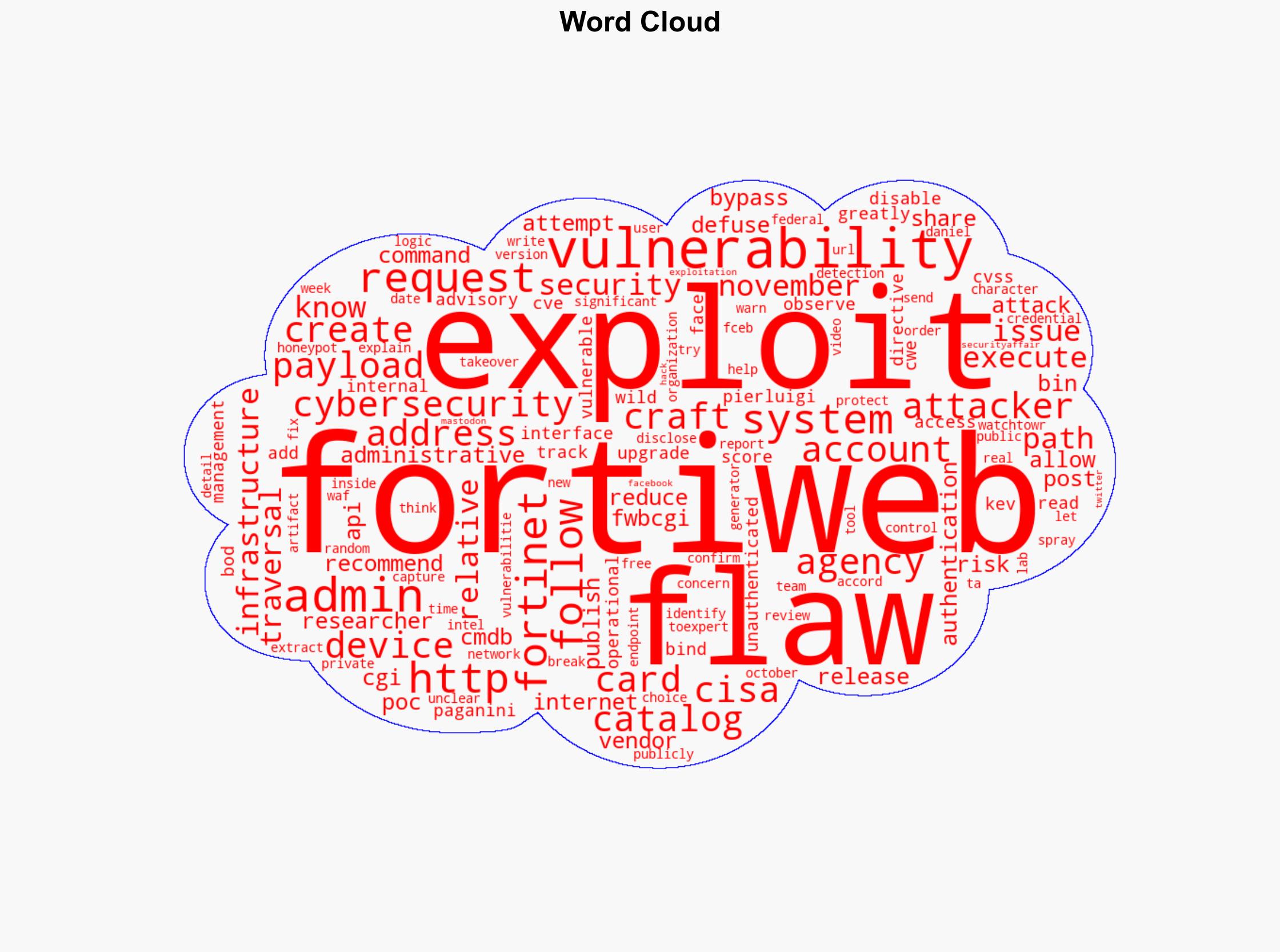
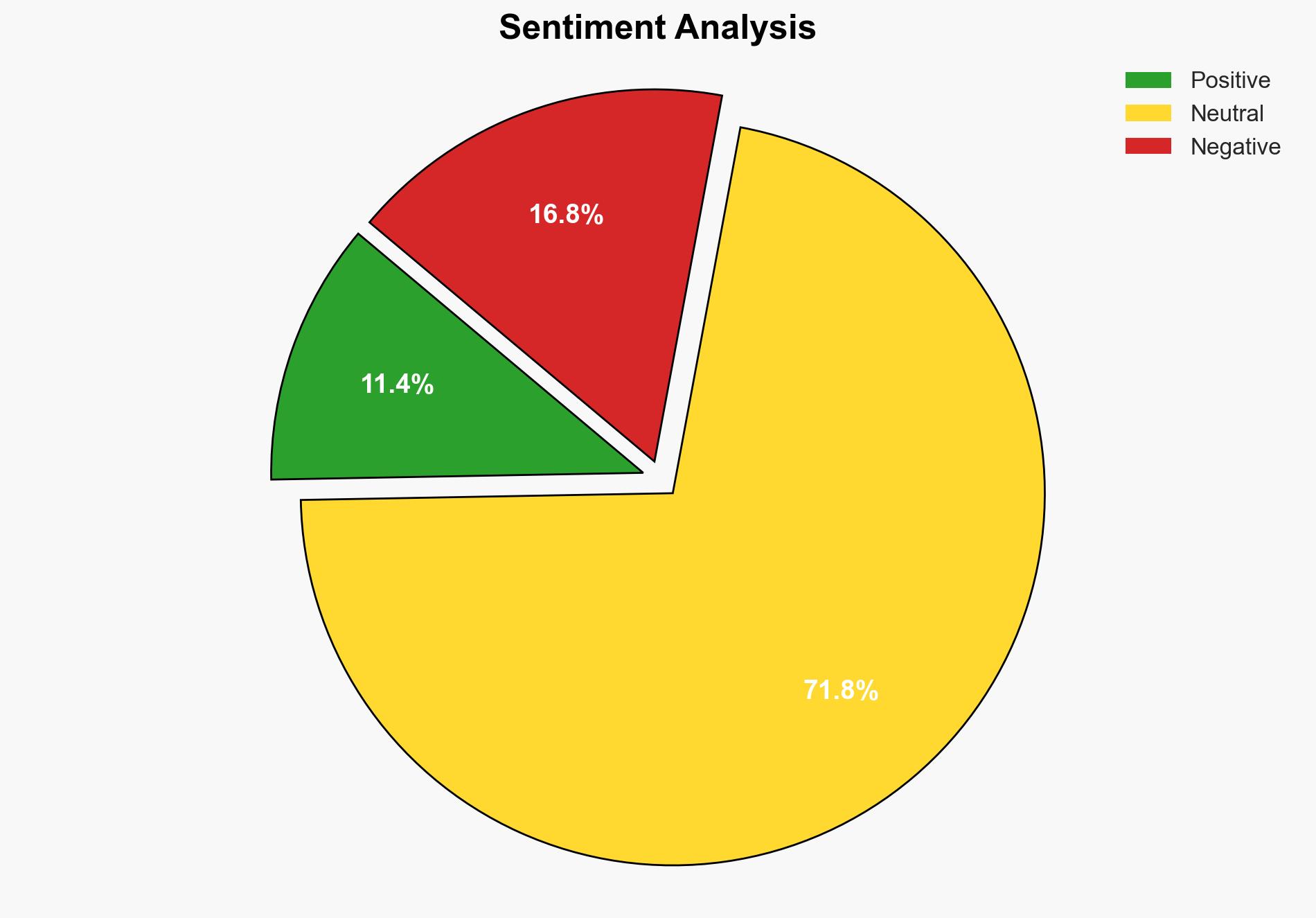
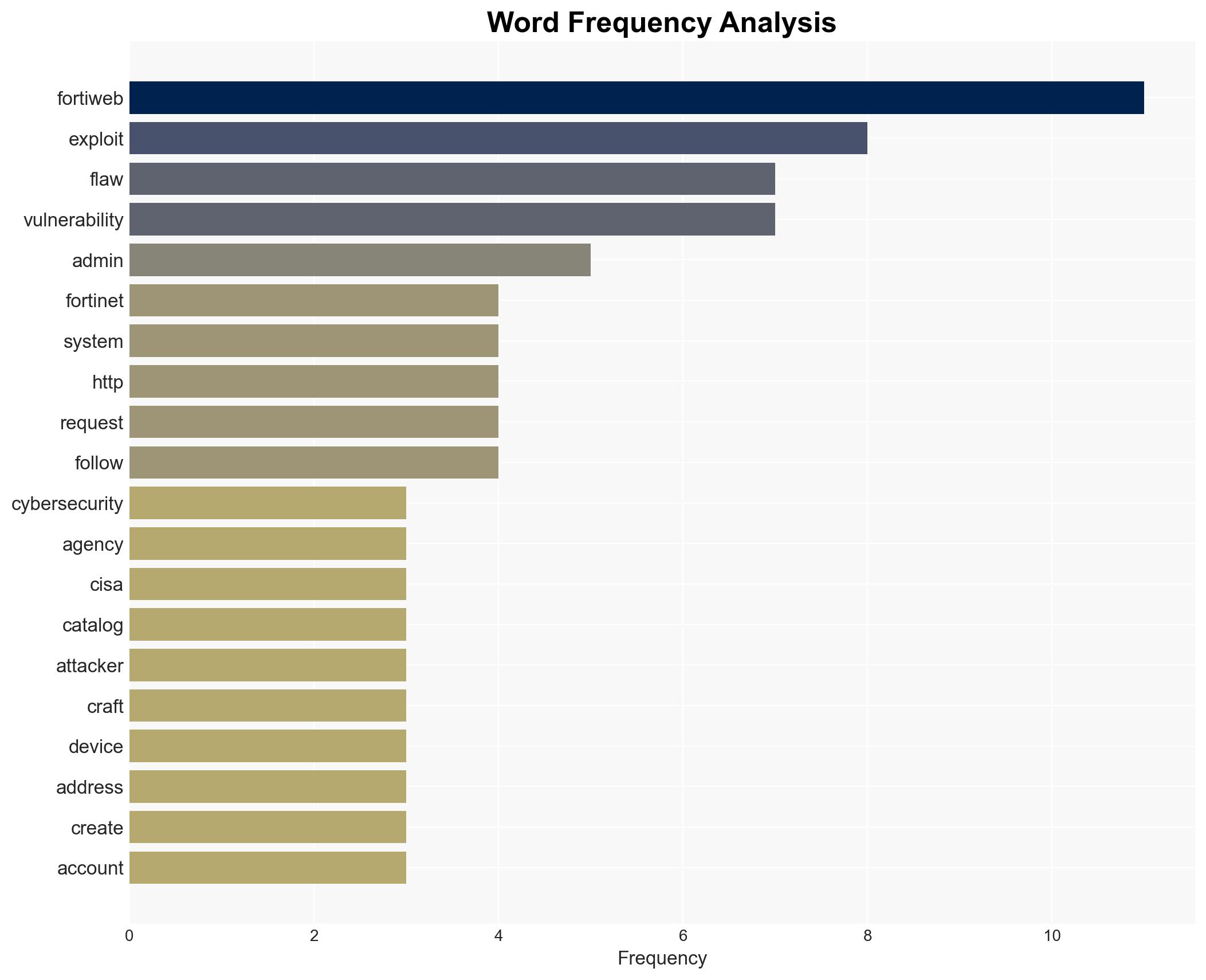
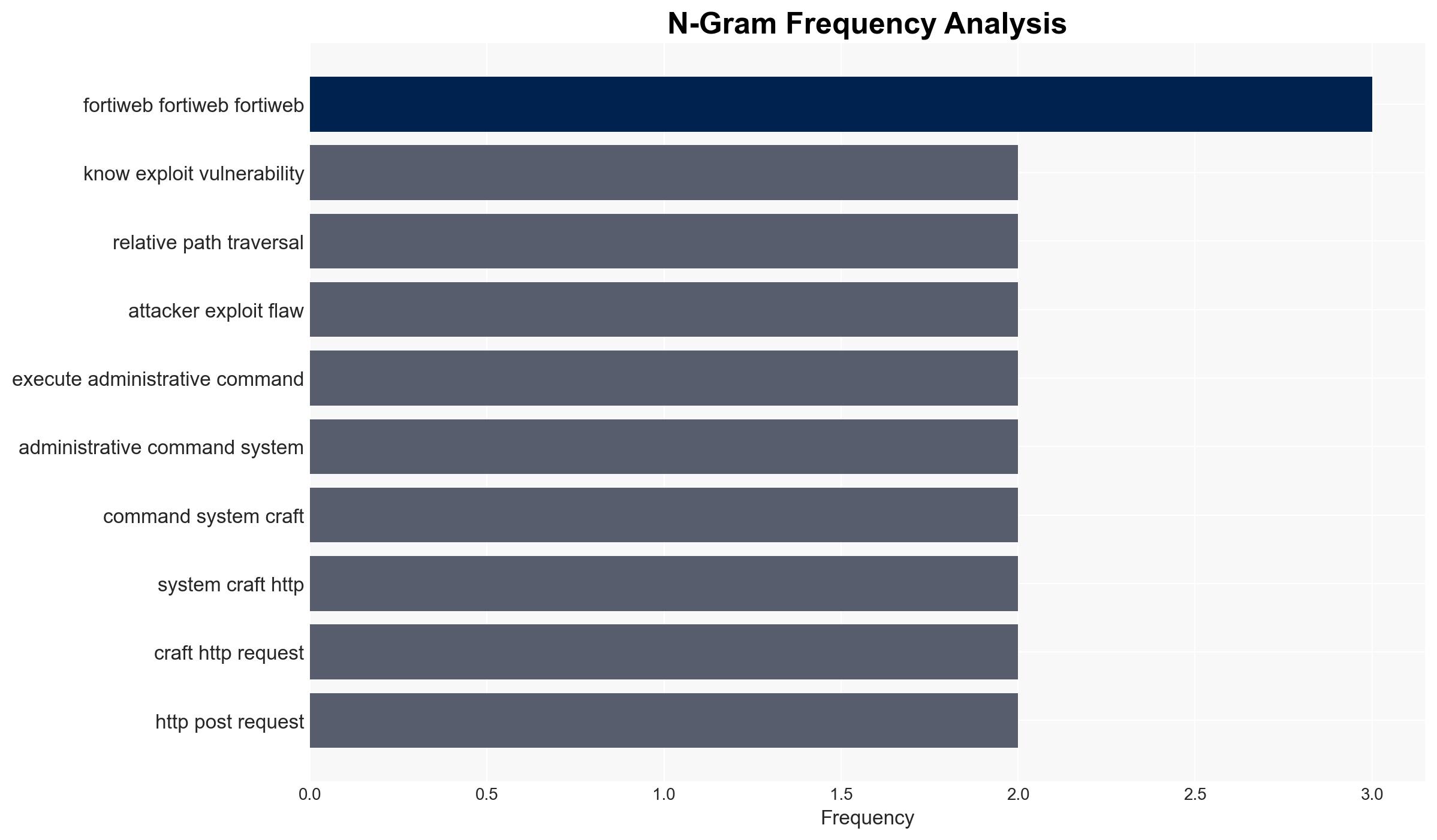
The vulnerability in Fortinet FortiWeb, a critical cybersecurity product, poses a significant risk due to its potential for remote exploitation by unauthenticated attackers. The most supported hypothesis is that this vulnerability will be actively exploited by threat actors to gain unauthorized access to systems, potentially leading to widespread data breaches and operational disruptions. Confidence Level: High. Recommended action includes immediate patching of vulnerable systems, enhanced monitoring for unusual activity, and dissemination of threat intelligence to stakeholders.
2. Competing Hypotheses
Hypothesis 1: The Fortinet FortiWeb vulnerability will be actively exploited by cybercriminals and state-sponsored actors to conduct targeted attacks on critical infrastructure and private organizations.
Hypothesis 2: The vulnerability will see limited exploitation due to rapid patch deployment and effective mitigation strategies by organizations, minimizing its impact.
Hypothesis 1 is more likely due to the high-profile nature of the vulnerability, the availability of proof-of-concept exploits, and historical patterns of exploitation following public disclosures. Hypothesis 2 is plausible but less likely given the typical lag in patch deployment and the attractiveness of the target for attackers.
3. Key Assumptions and Red Flags
Assumptions: Organizations will follow CISA’s directives and patch vulnerabilities promptly. Cybercriminals have the capability to exploit the vulnerability effectively.
Red Flags: Delays in patch deployment, lack of awareness among smaller organizations, and potential misinformation about the vulnerability’s impact.
Deception Indicators: False claims of patching or mitigation by organizations, potentially leading to a false sense of security.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant operational disruptions, data breaches, and loss of sensitive information. Politically, it could strain international relations if state-sponsored actors are involved. Economically, affected organizations could face financial losses and reputational damage. Informationally, there is a risk of misinformation spreading about the vulnerability’s impact and mitigation.
5. Recommendations and Outlook
- Actionable Steps: Immediate patching of Fortinet FortiWeb systems, enhanced network monitoring, and sharing of threat intelligence with relevant stakeholders.
- Best-case Scenario: Rapid patch deployment and effective mitigation reduce the vulnerability’s impact, preventing major incidents.
- Worst-case Scenario: Widespread exploitation leads to significant data breaches and operational disruptions across multiple sectors.
- Most-likely Scenario: Moderate exploitation occurs, with some organizations experiencing breaches due to delayed patching and inadequate security measures.
6. Key Individuals and Entities
Pierluigi Paganini (Cybersecurity Expert), Daniel Card (Researcher), Fortinet (Cybersecurity Vendor), CISA (Cybersecurity and Infrastructure Security Agency)
7. Thematic Tags
Cybersecurity, Vulnerability Management, Threat Intelligence, Risk Mitigation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·