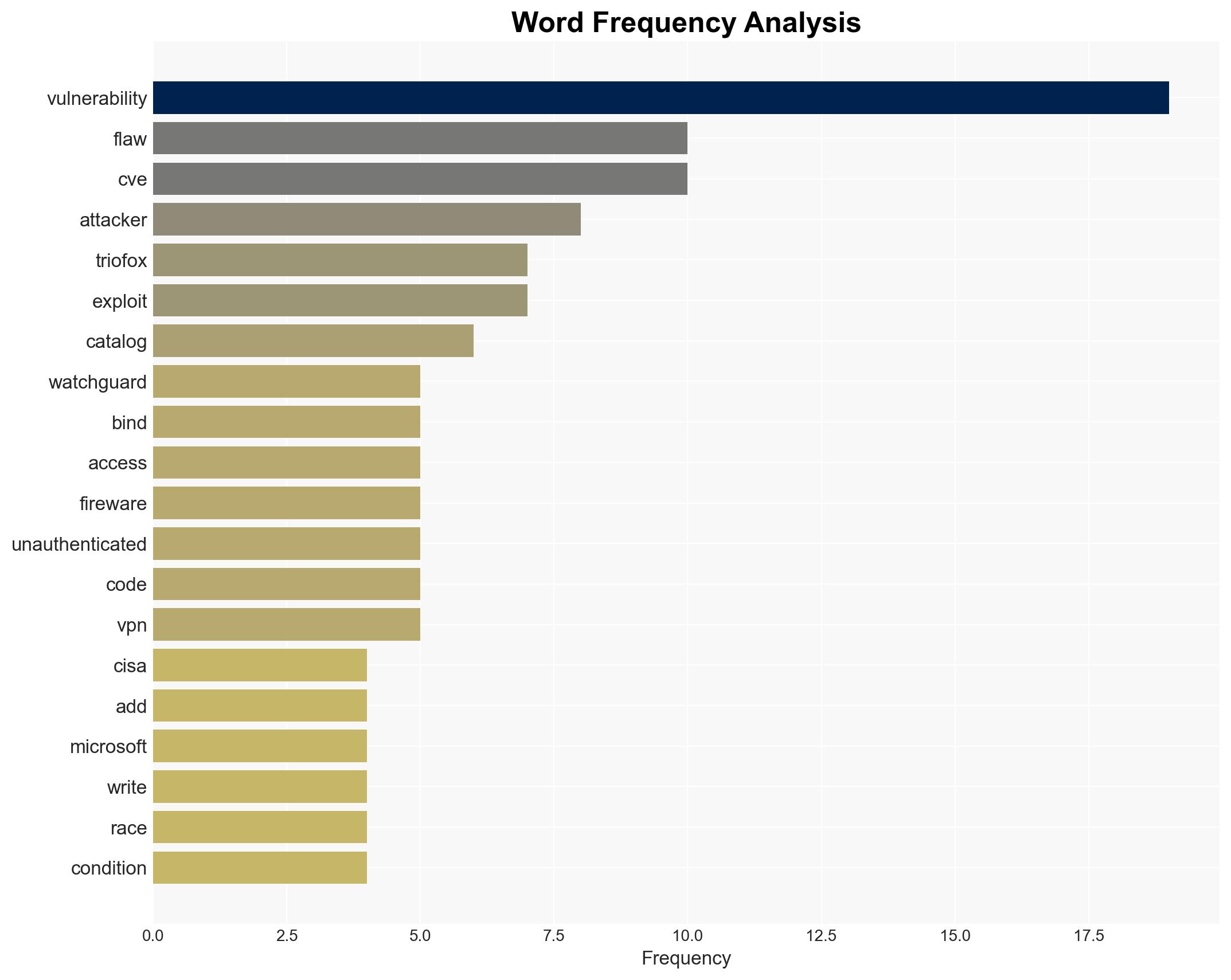
US CISA adds WatchGuard Firebox Microsoft Windows and Gladinet Triofox flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-11-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US CISA adds WatchGuard Firebox Microsoft Windows and Gladinet Triofox flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
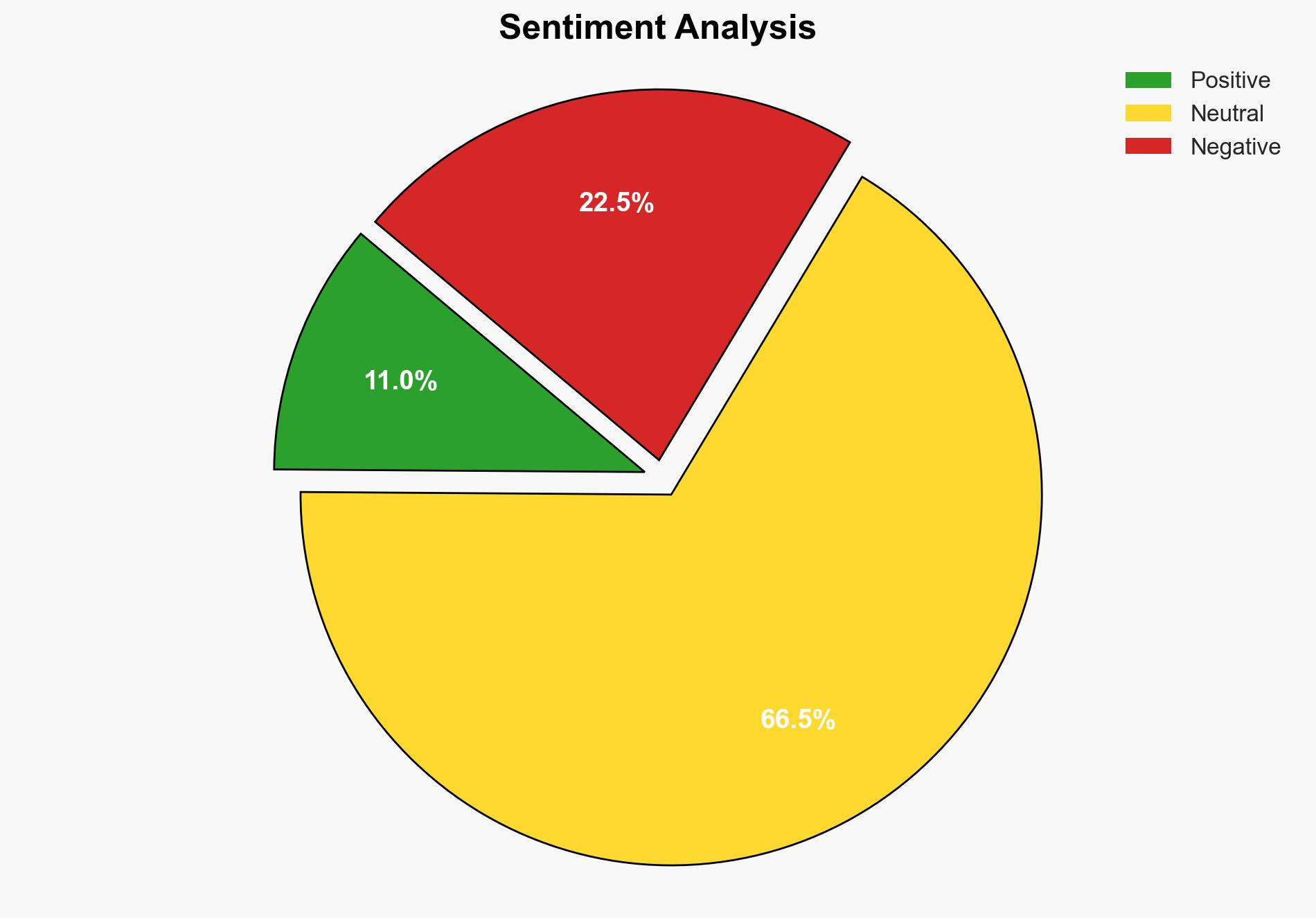
The inclusion of vulnerabilities in WatchGuard Firebox, Microsoft Windows, and Gladinet Triofox in CISA’s Known Exploited Vulnerabilities catalog highlights significant cybersecurity risks. The most supported hypothesis is that these vulnerabilities are actively exploited by threat actors, necessitating immediate patching and security measures to mitigate potential breaches. Confidence Level: High. Recommended action includes urgent patching of affected systems and enhanced monitoring for potential exploitation attempts.
2. Competing Hypotheses
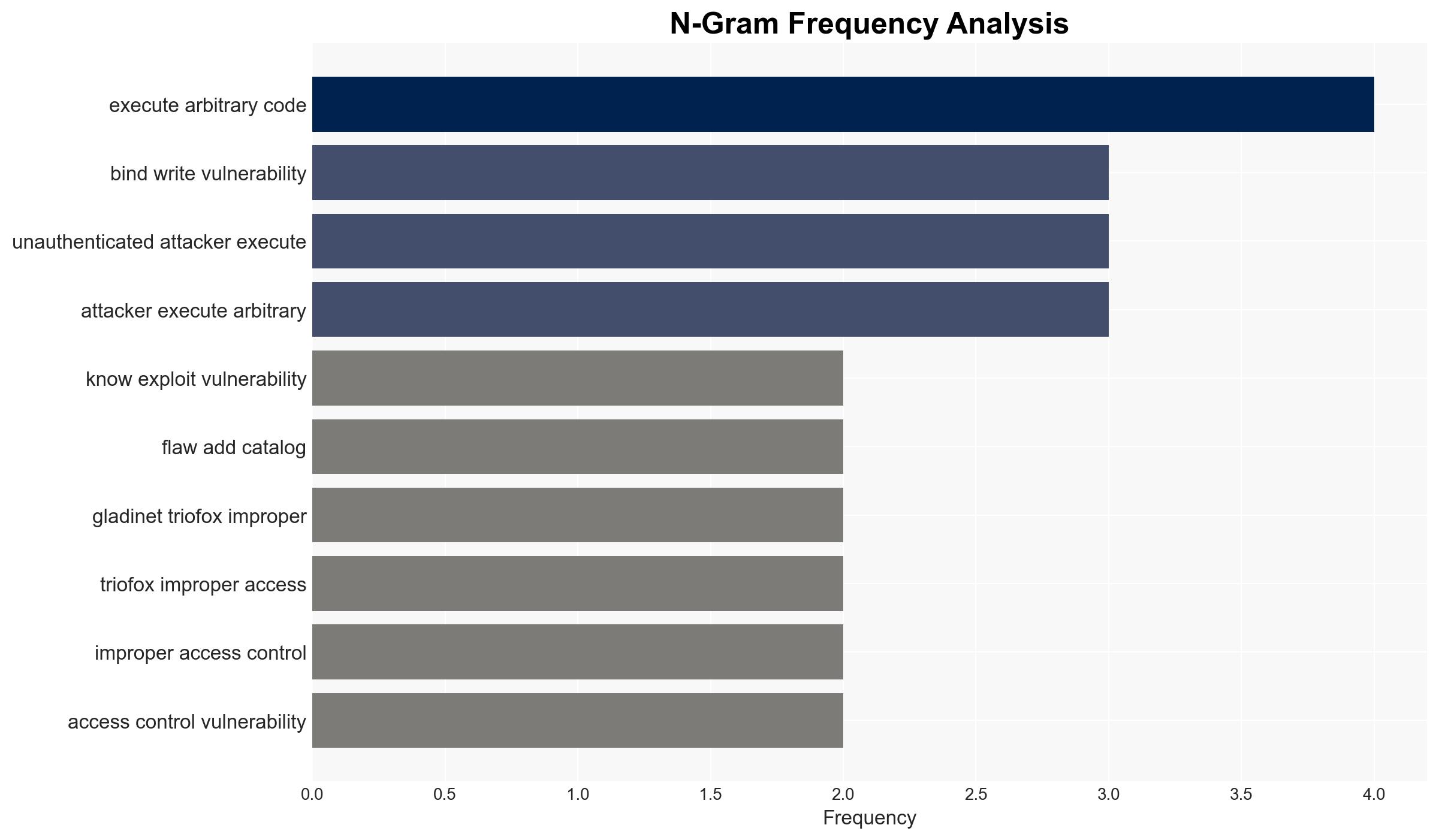
Hypothesis 1: The vulnerabilities are being actively exploited by sophisticated threat actors, including state-sponsored groups, to gain unauthorized access and execute arbitrary code, primarily targeting critical infrastructure and sensitive data systems.
Hypothesis 2: The vulnerabilities are primarily being exploited by opportunistic cybercriminals focusing on financial gain through ransomware and data theft, rather than targeted attacks on critical infrastructure.
Hypothesis 1 is more likely due to the nature of the vulnerabilities, which allow for remote code execution and privilege escalation, making them attractive to advanced persistent threat (APT) groups. The strategic value of exploiting such vulnerabilities aligns with state-sponsored objectives.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerabilities are not yet fully patched across all affected systems, increasing the risk of exploitation. Additionally, it is assumed that the vulnerabilities are known to a wide range of threat actors.
Red Flags: The rapid inclusion of these vulnerabilities in the CISA catalog suggests high confidence in their exploitation, indicating possible insider knowledge or intelligence sharing among threat actors.
Deception Indicators: There is a risk of misinformation regarding the extent of exploitation or the effectiveness of patches, potentially leading to a false sense of security among organizations.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant disruptions in critical infrastructure, data breaches, and financial losses. Politically, state-sponsored exploitation could escalate tensions between nations, especially if linked to cyber espionage. Economically, affected organizations may face increased costs related to incident response and legal liabilities. Informationally, successful exploitation could undermine trust in digital systems and lead to broader societal impacts.
5. Recommendations and Outlook
- Actionable Steps: Organizations should prioritize patching affected systems, conduct thorough security audits, and enhance monitoring for signs of exploitation. Collaboration with cybersecurity agencies for threat intelligence sharing is crucial.
- Best-case Scenario: Rapid patching and proactive security measures prevent significant exploitation, minimizing impact.
- Worst-case Scenario: Widespread exploitation leads to major data breaches and critical infrastructure disruptions, escalating geopolitical tensions.
- Most-likely Scenario: Mixed success in patching efforts results in sporadic exploitation, with some high-profile incidents drawing attention to cybersecurity vulnerabilities.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Key entities include US CISA, WatchGuard, Microsoft, Gladinet, and Google’s Mandiant.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology