US extends Cybersecurity Information Sharing Act deadline to September amid DHS funding negotiations
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US punts renewal of threat data sharing law to September
1. BLUF (Bottom Line Up Front)
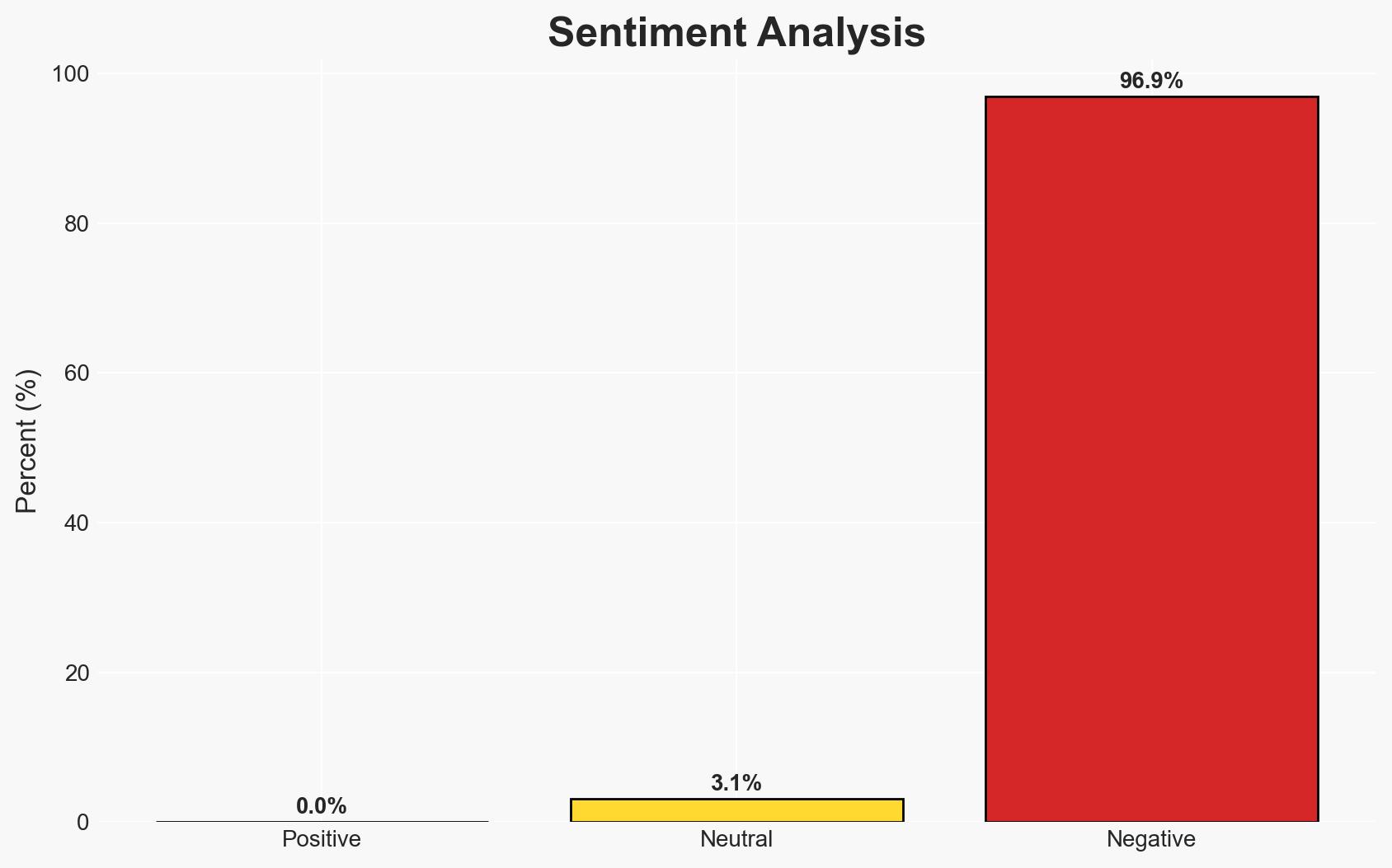
The extension of the Cybersecurity Information Sharing Act (CISA) 2015 to September 2026 is likely, providing temporary legal protection for threat data sharing between public and private sectors. This development is critical for maintaining cybersecurity collaboration, although a long-term solution remains necessary. Overall confidence in this assessment is moderate, given legislative uncertainties and political dynamics.
2. Competing Hypotheses
- Hypothesis A: The extension of CISA 2015 will be approved, ensuring continued legal protection for cybersecurity information sharing. This is supported by the passage of the DHS Appropriations Act in the House and the recognition of the importance of such collaboration by industry leaders. However, uncertainties remain regarding Senate approval and potential political opposition.
- Hypothesis B: The extension may face significant hurdles in the Senate, potentially leading to another lapse in legal protections. This hypothesis considers the contentious nature of the DHS funding package and opposition related to ICE funding, which could stall or derail the process.
- Assessment: Hypothesis A is currently better supported due to the successful passage in the House and the strategic importance of cybersecurity collaboration. Key indicators that could shift this judgment include Senate opposition or amendments to the DHS funding package.
3. Key Assumptions and Red Flags
- Assumptions: The Senate will prioritize cybersecurity over political disputes; industry stakeholders will continue to advocate for CISA 2015; the temporary extension will provide sufficient time for legislative action.
- Information Gaps: Specific positions of key Senate members on the DHS funding package; potential amendments that could affect CISA 2015’s extension.
- Bias & Deception Risks: Potential bias from industry sources emphasizing the necessity of CISA 2015; political narratives that may exaggerate or downplay the importance of the extension for partisan gain.
4. Implications and Strategic Risks
The extension of CISA 2015, if approved, will temporarily stabilize cybersecurity collaboration but leaves long-term uncertainty unresolved. This situation could influence broader legislative dynamics and cybersecurity strategies.
- Political / Geopolitical: Potential for increased partisan conflict over DHS funding, impacting broader legislative agendas.
- Security / Counter-Terrorism: Continued legal protection for threat data sharing enhances national security posture against cyber threats.
- Cyber / Information Space: Reinforced collaboration may deter adversaries by reducing exploitable gaps in cybersecurity defenses.
- Economic / Social: Stability in cybersecurity practices could bolster confidence in digital infrastructure, supporting economic resilience.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Senate proceedings closely; engage with key stakeholders to advocate for the extension; prepare contingency plans for potential lapse scenarios.
- Medium-Term Posture (1–12 months): Develop a comprehensive legislative strategy for a permanent solution; enhance public-private partnerships in cybersecurity information sharing.
- Scenario Outlook:
- Best: Permanent legislative solution enacted, ensuring stable cybersecurity collaboration.
- Worst: Extension fails, leading to significant gaps in threat data sharing and increased vulnerability.
- Most-Likely: Temporary extension approved, with ongoing negotiations for a long-term resolution.
6. Key Individuals and Entities
- Cynthia Kaiser, Senior Vice President, Ransomware Research Center at Halcyon
- Marc van Zadelhoff, CEO, Mimecast
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
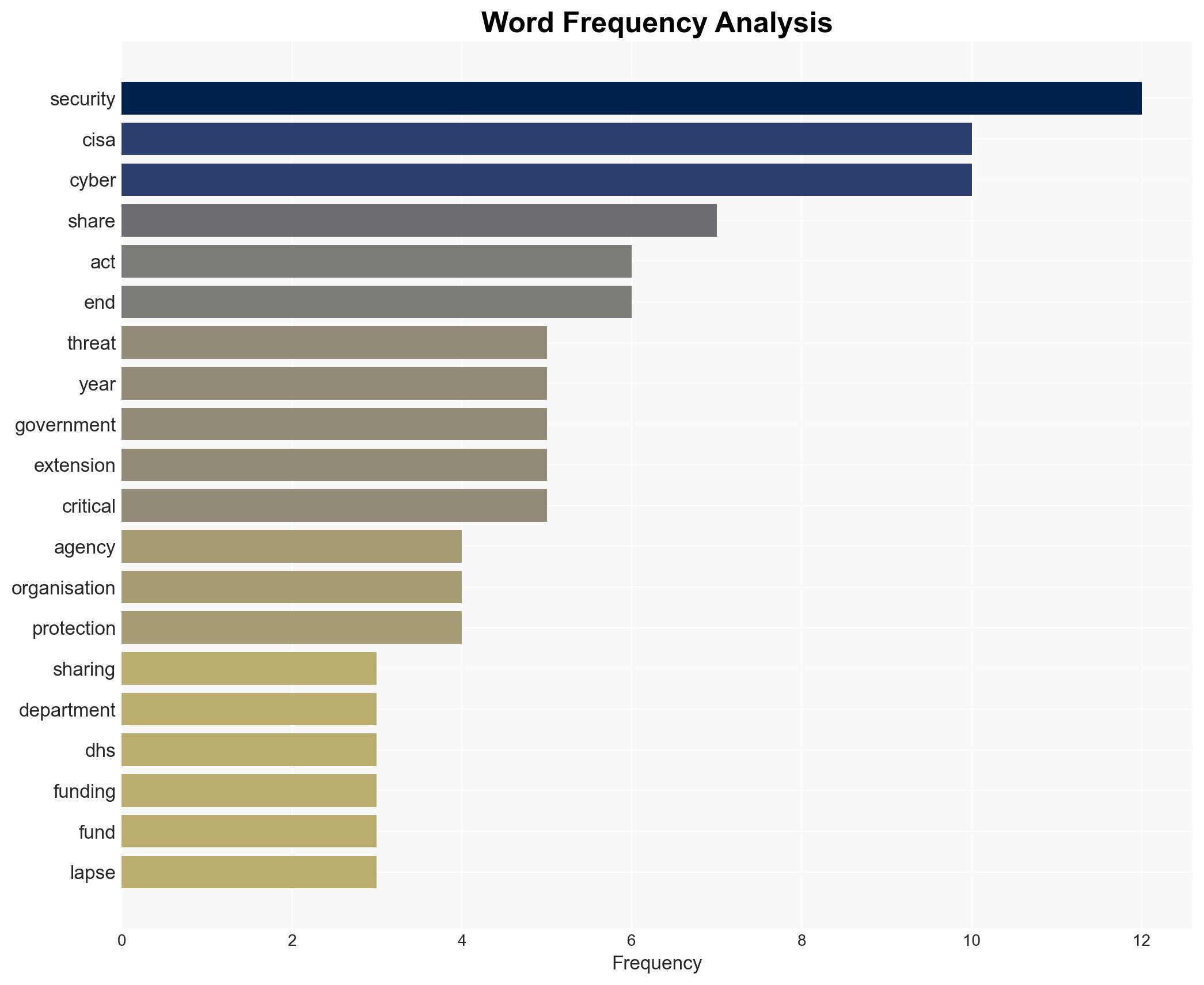
cybersecurity, legislative process, information sharing, national security, public-private partnership, DHS funding, political dynamics
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us