US Five Plead Guilty in North Korean IT Worker Fraud Scheme – Infosecurity Magazine
Published on: 2025-11-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
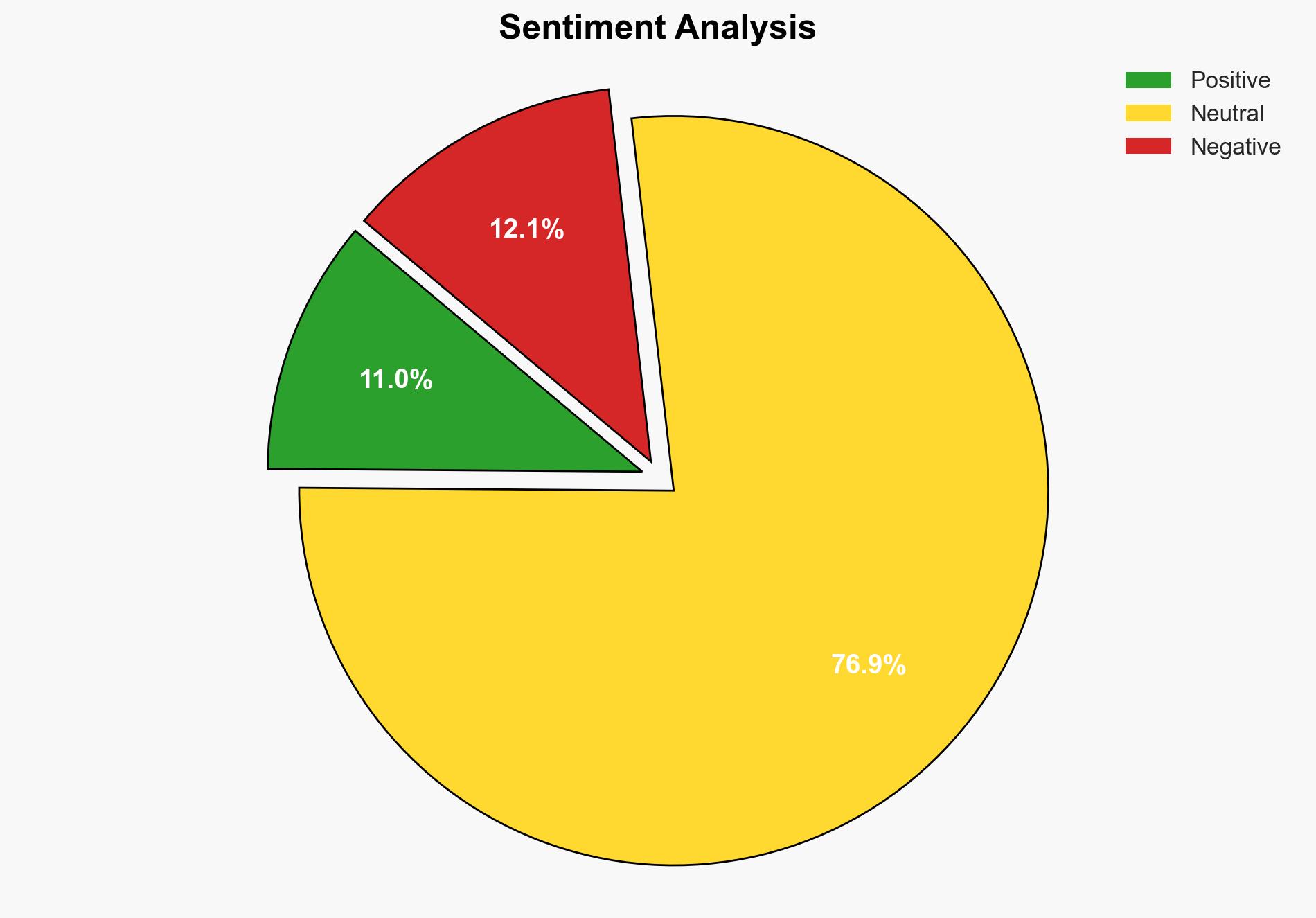
The most supported hypothesis is that the North Korean regime is leveraging international cybercrime, specifically through remote IT worker schemes, to circumvent sanctions and fund its strategic priorities. This is evidenced by the involvement of North Korean actors in the fraudulent scheme and the subsequent financial gains directed to the regime. Confidence Level: High. Recommended action includes strengthening international collaboration on cybersecurity measures and enhancing vetting processes for remote workers.
2. Competing Hypotheses
Hypothesis 1: The primary objective of the scheme was to generate revenue for the North Korean regime by exploiting vulnerabilities in the global IT and cryptocurrency sectors. This is supported by the DoJ’s findings that the scheme involved identity theft and cryptocurrency theft, with funds directed to North Korea.
Hypothesis 2: The scheme was primarily a criminal enterprise driven by individual financial gain, with incidental benefits to the North Korean regime. This hypothesis is less supported due to the structured involvement of known North Korean hacking groups and the strategic alignment with the regime’s financial needs.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the individuals involved were knowingly aiding the North Korean regime. The effectiveness of international sanctions on North Korea is assumed to be a driving factor for such schemes.
Red Flags: The involvement of known North Korean hacking groups like the Lazarus Group suggests state-level orchestration. The use of false identities and remote work to infiltrate companies indicates sophisticated planning and execution.
4. Implications and Strategic Risks
The continuation of such schemes poses significant risks, including the erosion of trust in remote work environments and the potential for increased cyberattacks on financial institutions. Politically, this could strain international relations and lead to heightened sanctions or cyber countermeasures. Economically, successful schemes could destabilize cryptocurrency markets and impact global financial systems.
5. Recommendations and Outlook
- Enhance international cooperation on cybersecurity, particularly in tracking and preventing state-sponsored cybercrime.
- Implement stricter vetting processes for remote workers, including background checks and identity verification.
- Best-case scenario: Improved cybersecurity measures prevent future schemes, reducing North Korea’s ability to fund its regime through illicit means.
- Worst-case scenario: Escalation of cyberattacks leads to significant financial losses and geopolitical tensions.
- Most-likely scenario: Continued attempts by North Korea to exploit cyber vulnerabilities, necessitating ongoing vigilance and adaptation of security protocols.
6. Key Individuals and Entities
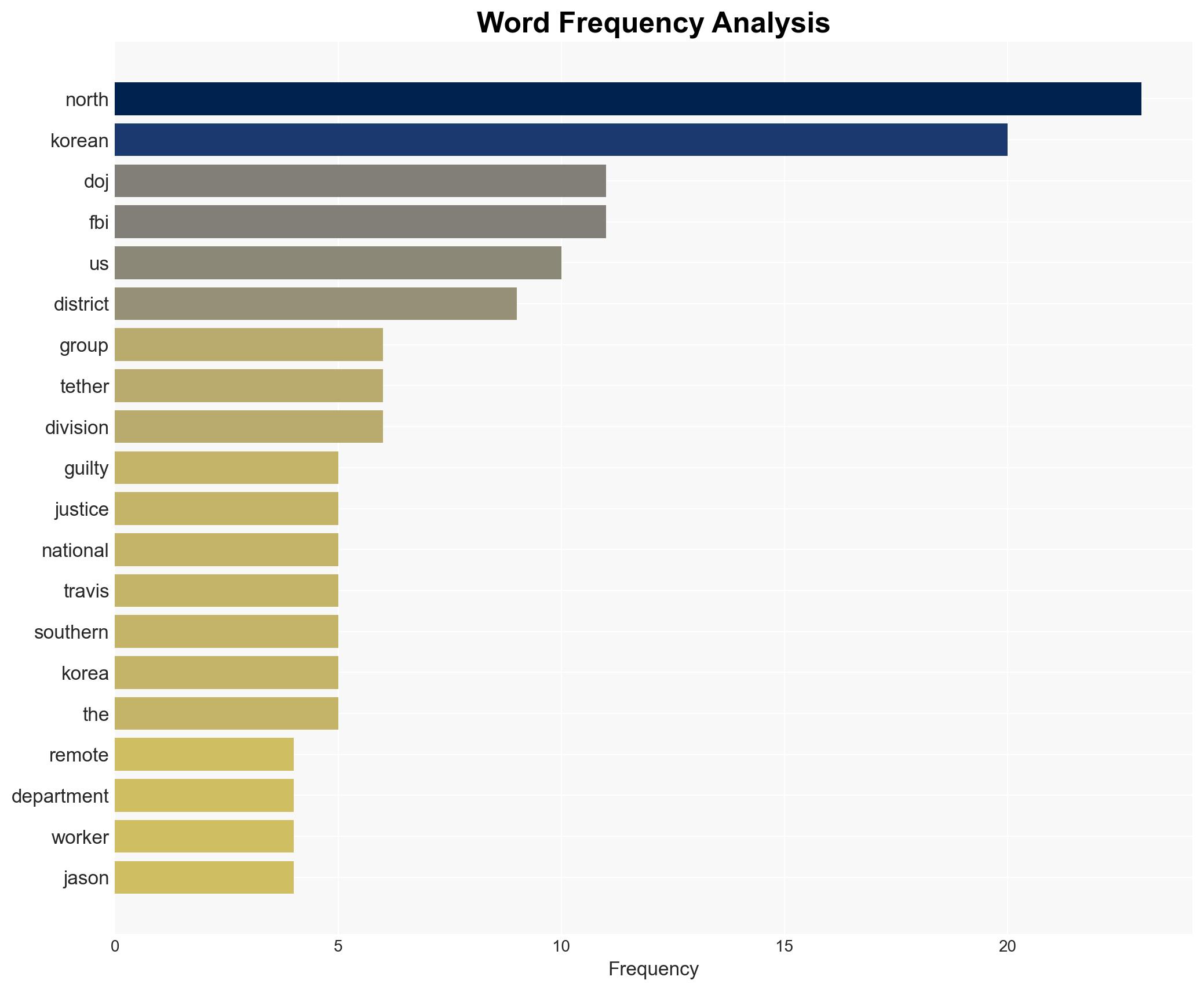
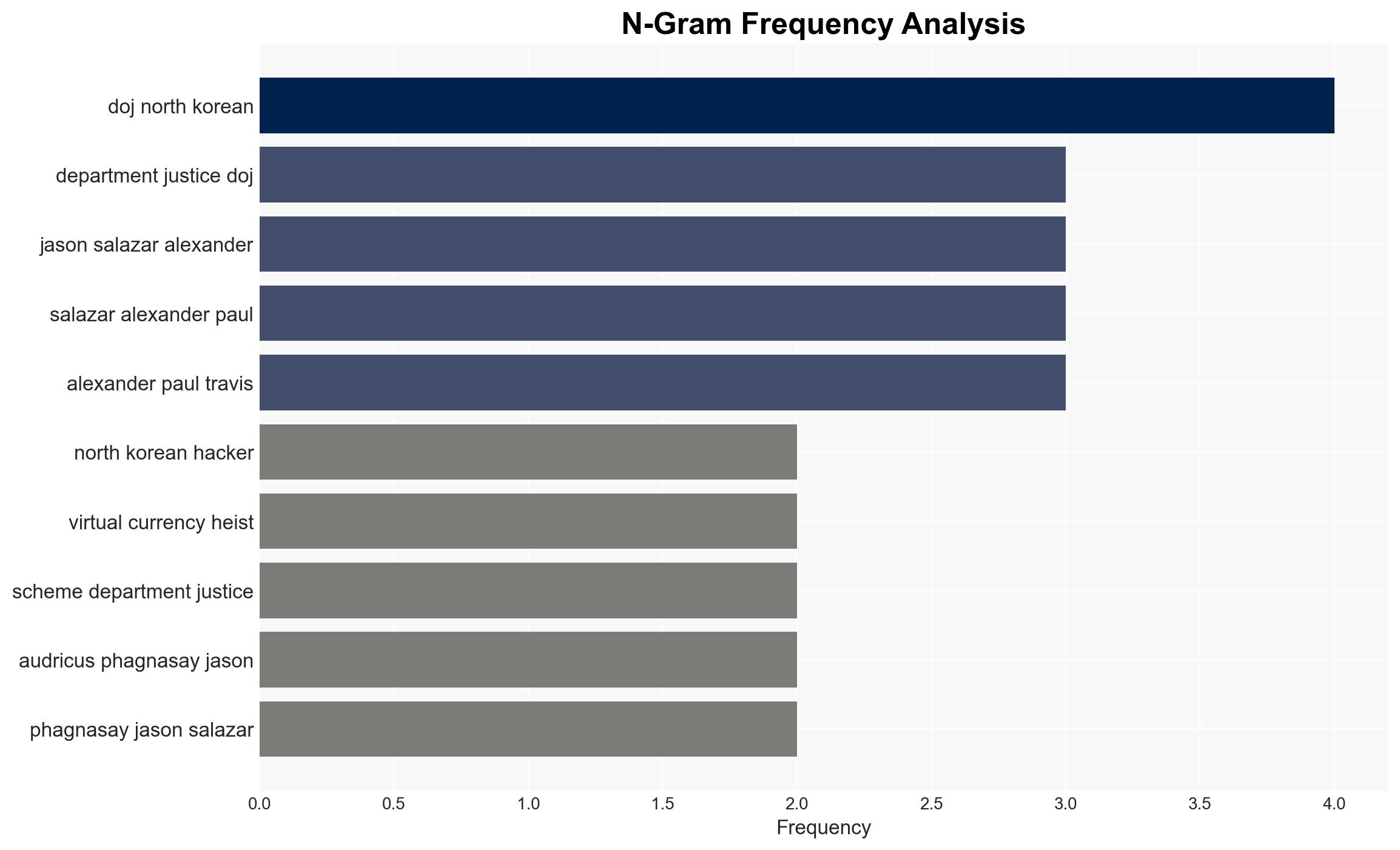
Audricus Phagnasay, Jason Salazar, Alexander Paul Travis, Erick Ntekereze Prince, Oleksandr Didenko, Lazarus Group, APT38.
7. Thematic Tags
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us
·