US infiltration against China’s National Time Service Center ‘proves once again it is the largest source of cyberattack’ FM – Globalsecurity.org
Published on: 2025-10-25
Intelligence Report: US infiltration against China’s National Time Service Center ‘proves once again it is the largest source of cyberattack’ FM – Globalsecurity.org
1. BLUF (Bottom Line Up Front)
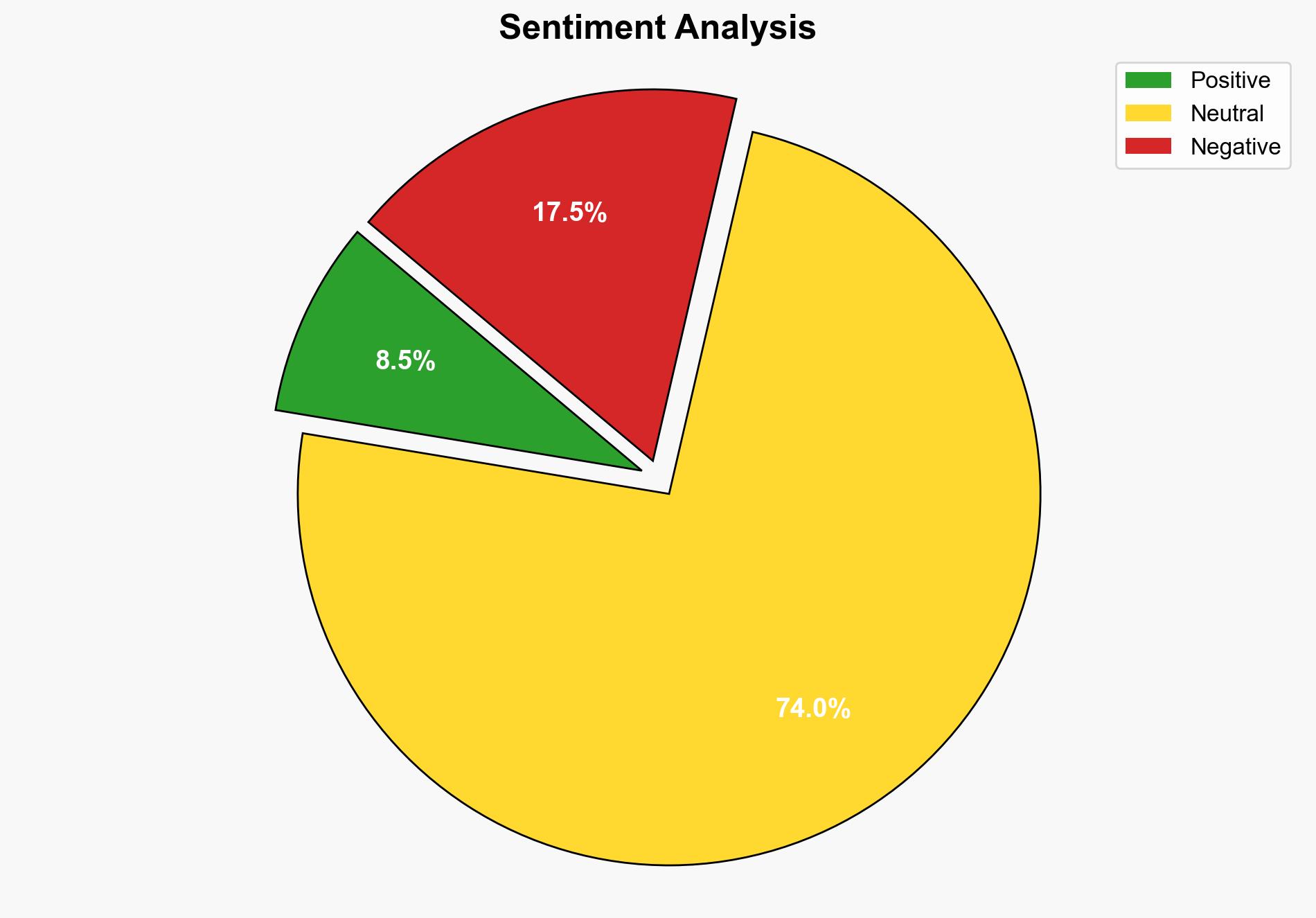
The most supported hypothesis is that the allegations of US cyber infiltration are part of a strategic narrative by China to highlight perceived threats and justify its cybersecurity measures. Confidence level: Moderate. Recommended action: Increase monitoring of cyber activities and engage in diplomatic dialogue to clarify intentions and reduce tensions.
2. Competing Hypotheses
1. **Hypothesis 1**: The US has conducted cyber operations against China’s National Time Service Center as part of broader intelligence-gathering efforts.
– **Supporting Evidence**: Historical precedence of US cyber operations; technical analysis reports cited by China.
– **Contradictory Evidence**: Lack of independent verification of the claims; potential bias in source reporting.
2. **Hypothesis 2**: The allegations are part of a strategic narrative by China to reinforce its cybersecurity posture and rally domestic and international support against perceived US aggression.
– **Supporting Evidence**: Timing of the announcement coincides with heightened US-China tensions; emphasis on the narrative of US as a global cyber threat.
– **Contradictory Evidence**: Technical reports suggesting actual cyber activity; potential risks of international backlash if claims are unfounded.
Using ACH 2.0, Hypothesis 2 is better supported due to the strategic context and lack of corroborated evidence for Hypothesis 1.
3. Key Assumptions and Red Flags
– **Assumptions**: The technical analysis provided by China is accurate and unbiased; the US has the capability and intent to target such infrastructure.
– **Red Flags**: Lack of independent verification of the cyberattack; potential for cognitive bias in interpreting China’s narrative as purely defensive.
– **Blind Spots**: Limited insight into internal US cyber operations; potential underestimation of China’s own cyber capabilities and intentions.
4. Implications and Strategic Risks
– **Patterns**: Increasing frequency of cyber-related accusations between the US and China, indicative of escalating cyber tensions.
– **Cascading Threats**: Potential for retaliatory cyberattacks, impacting global infrastructure and economic stability.
– **Escalation Scenarios**: Heightened diplomatic tensions could lead to broader geopolitical conflicts, impacting international alliances and trade.
5. Recommendations and Outlook
- Enhance cyber defense mechanisms and intelligence-sharing with allies to mitigate risks.
- Engage in diplomatic dialogue with China to clarify intentions and reduce misinterpretations.
- Scenario Projections:
- Best Case: Diplomatic engagement leads to de-escalation and improved cybersecurity cooperation.
- Worst Case: Continued cyber exchanges lead to significant infrastructure disruptions and geopolitical conflict.
- Most Likely: Ongoing cyber skirmishes with periodic diplomatic interventions to manage tensions.
6. Key Individuals and Entities
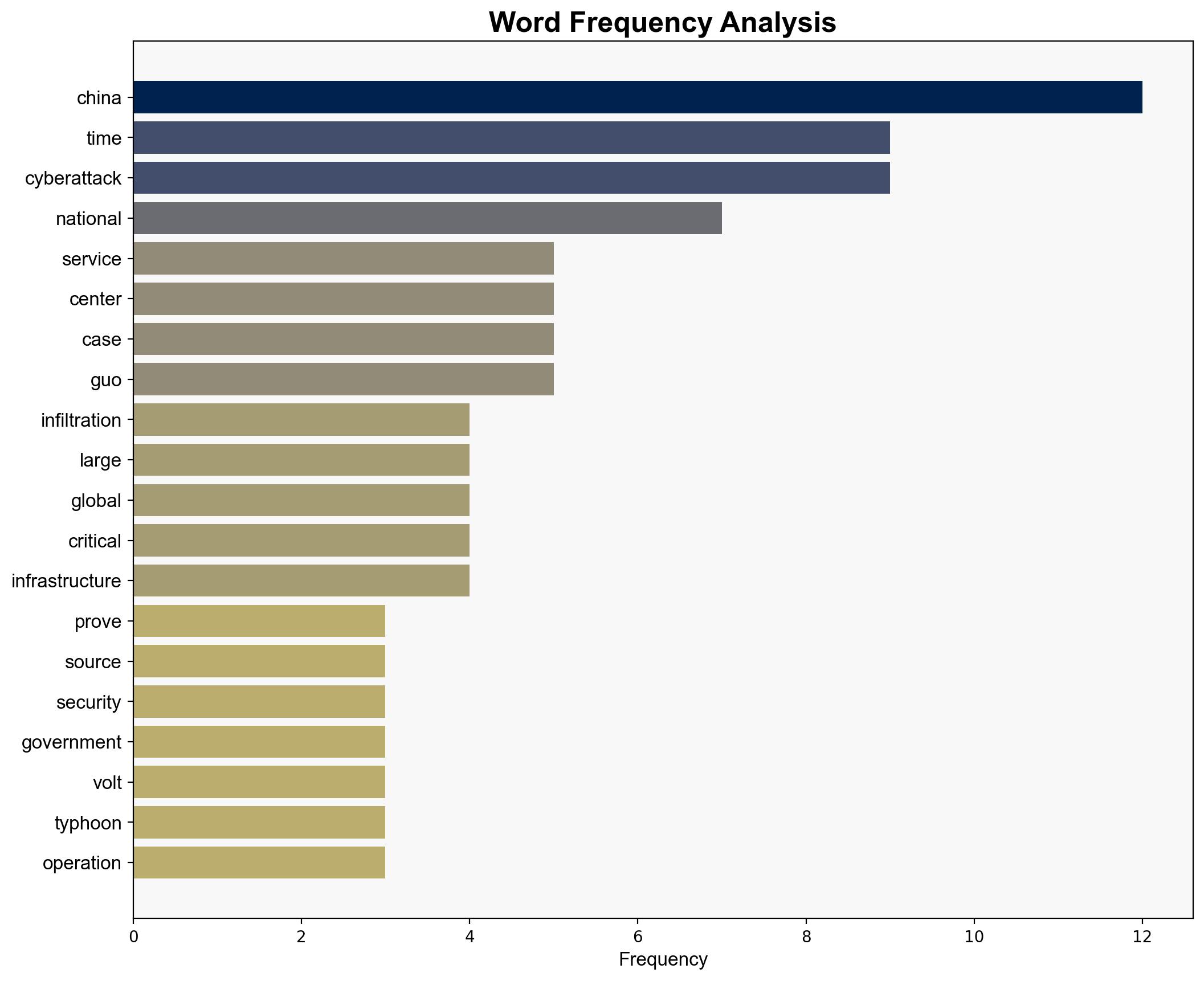
– Guo Jiakun
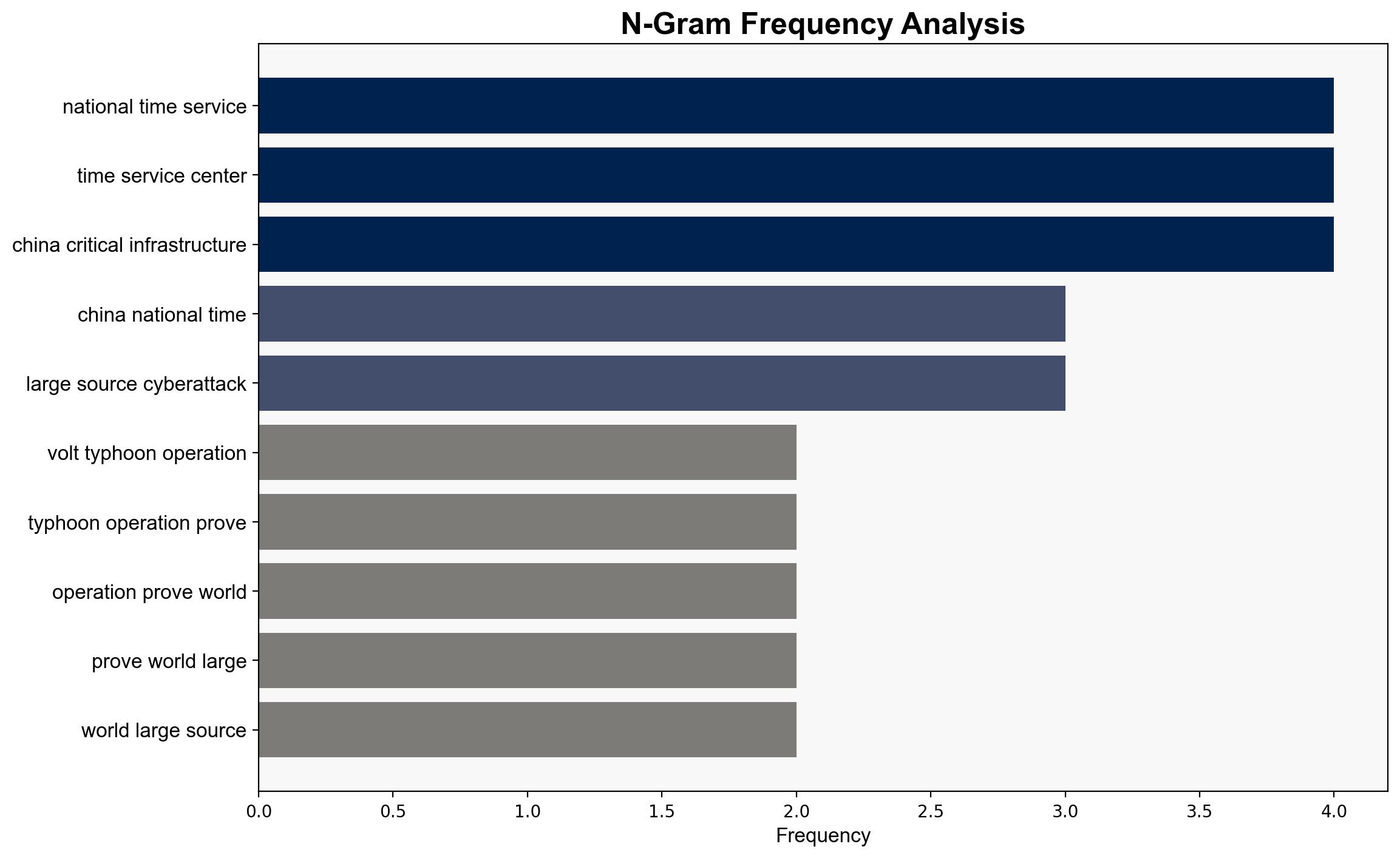
– National Time Service Center
– National Security Agency (NSA)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus