US Intensifies Maritime Operations Against Tanker Evading Venezuela Oil Sanctions
Published on: 2025-12-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Tanker defies Coast Guard as US escalates Venezuela oil blockade
1. BLUF (Bottom Line Up Front)
The U.S. is engaged in a high-stakes pursuit of the oil tanker Bella 1, which is suspected of evading sanctions related to Venezuelan oil. This incident highlights the increasing complexity and risks associated with U.S. maritime enforcement efforts. The situation could escalate further, impacting geopolitical relations and regional stability. Overall confidence in this assessment is moderate due to significant information gaps and potential for deception.
2. Competing Hypotheses
- Hypothesis A: The Bella 1 is deliberately evading U.S. sanctions as part of a coordinated effort by sanctioned entities to undermine U.S. economic pressure. This is supported by the ship’s evasive maneuvers and sanction-evasion tactics. However, the specific command and control structure behind these actions remains unclear.
- Hypothesis B: The Bella 1’s actions are the result of miscommunication or misunderstanding of U.S. enforcement intentions, possibly exacerbated by independent actors within the shipping industry. This is less supported given the deliberate nature of the ship’s maneuvers and historical compliance by other vessels.
- Assessment: Hypothesis A is currently better supported due to the vessel’s sophisticated evasion tactics and the broader context of sanctioned entities’ operations. Indicators such as direct communications intercepts or corroborating intelligence from allied nations could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The Bella 1 is acting under direct orders from a sanctioned entity; U.S. forces have the capability to safely board and seize the tanker; international maritime laws will support U.S. actions.
- Information Gaps: The identity and intentions of the command structure behind Bella 1; the full extent of the “shadow fleet” operations; potential responses from Venezuela or allied nations.
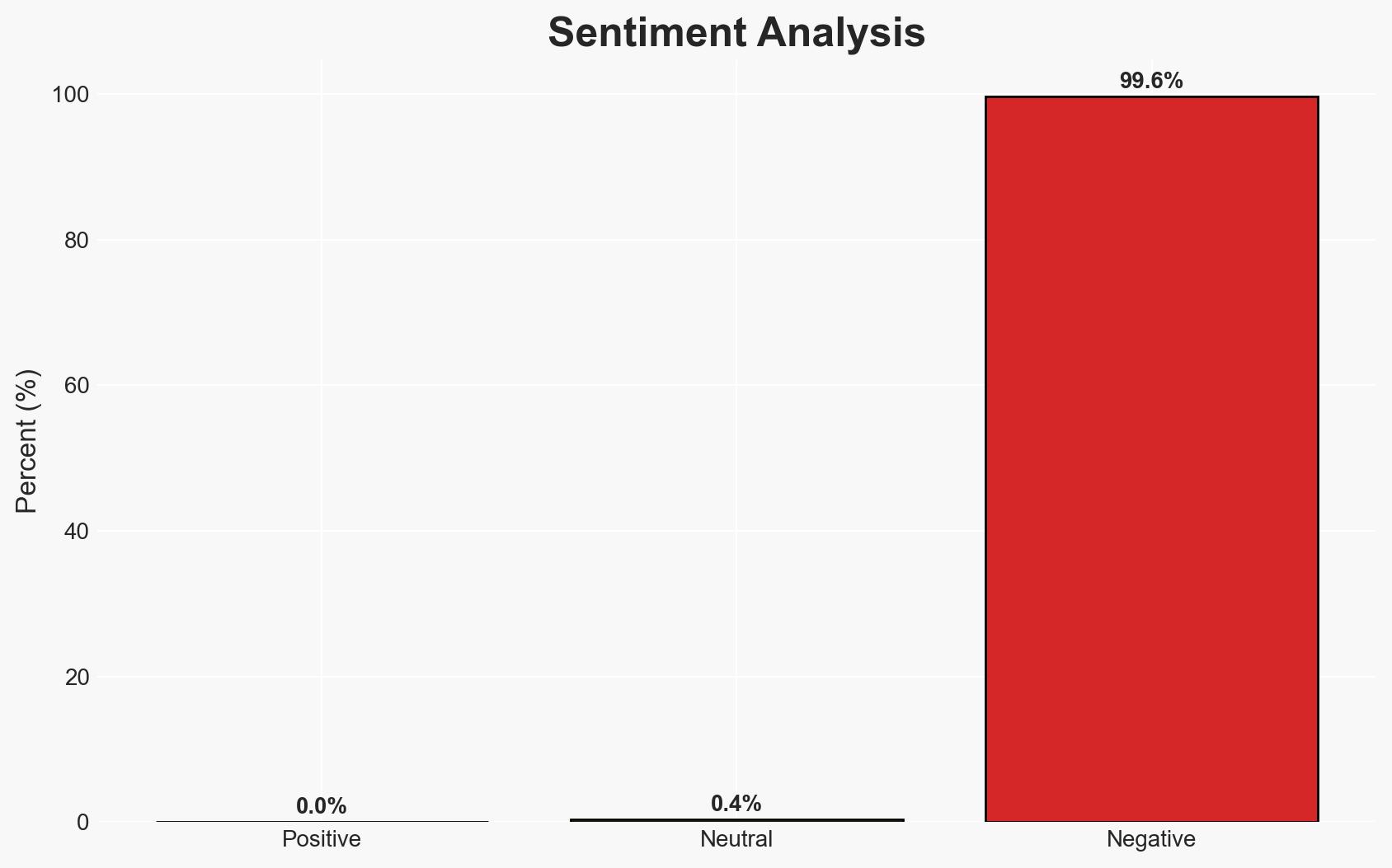
- Bias & Deception Risks: Confirmation bias in interpreting evasive actions as hostile; potential misinformation from involved parties; reliance on incomplete or biased open-source reporting.
4. Implications and Strategic Risks
This development could lead to heightened tensions between the U.S. and Venezuela, with potential spillover effects on regional stability. The U.S.’s aggressive enforcement could deter future sanction evasions but also provoke retaliatory measures.
- Political / Geopolitical: Possible escalation in U.S.-Venezuela tensions; impact on U.S. relations with countries involved in the “shadow fleet.”
- Security / Counter-Terrorism: Increased risk of maritime confrontations; potential for asymmetric responses from sanctioned entities.
- Cyber / Information Space: Potential for cyber operations targeting U.S. maritime assets or information warfare campaigns to sway public opinion.
- Economic / Social: Disruption in oil markets; potential economic impacts on countries reliant on Venezuelan oil.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance maritime surveillance and intelligence-sharing with allies; prepare diplomatic channels for de-escalation; monitor for retaliatory actions.
- Medium-Term Posture (1–12 months): Strengthen partnerships with regional allies; invest in maritime enforcement capabilities; develop contingency plans for potential escalation.
- Scenario Outlook:
- Best: Successful seizure of Bella 1 with minimal diplomatic fallout; increased deterrence against sanction evasion.
- Worst: Escalation into a broader conflict with Venezuela or allied nations; significant disruption to global oil markets.
- Most-Likely: Continued cat-and-mouse enforcement actions with periodic diplomatic tensions; gradual adaptation by sanctioned entities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
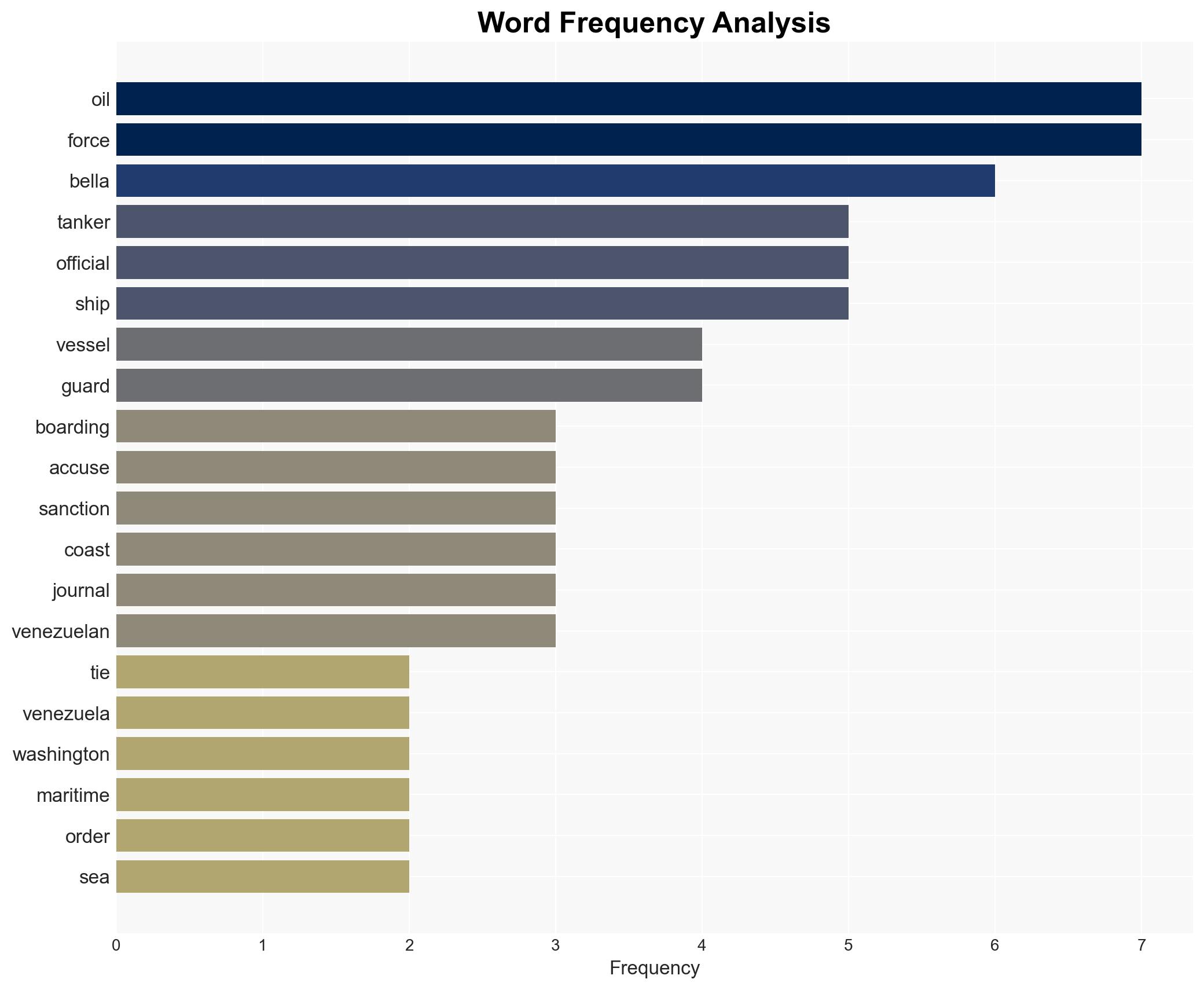
Counter-Terrorism, sanctions, maritime security, Venezuela, oil trade, international law, U.S. foreign policy, economic pressure
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us