US Removes Sanctions on Three Individuals Linked to Predator Spyware Development
Published on: 2026-01-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US Lifts Sanctions on Trio Accused of Work on Predator Spyware
1. BLUF (Bottom Line Up Front)
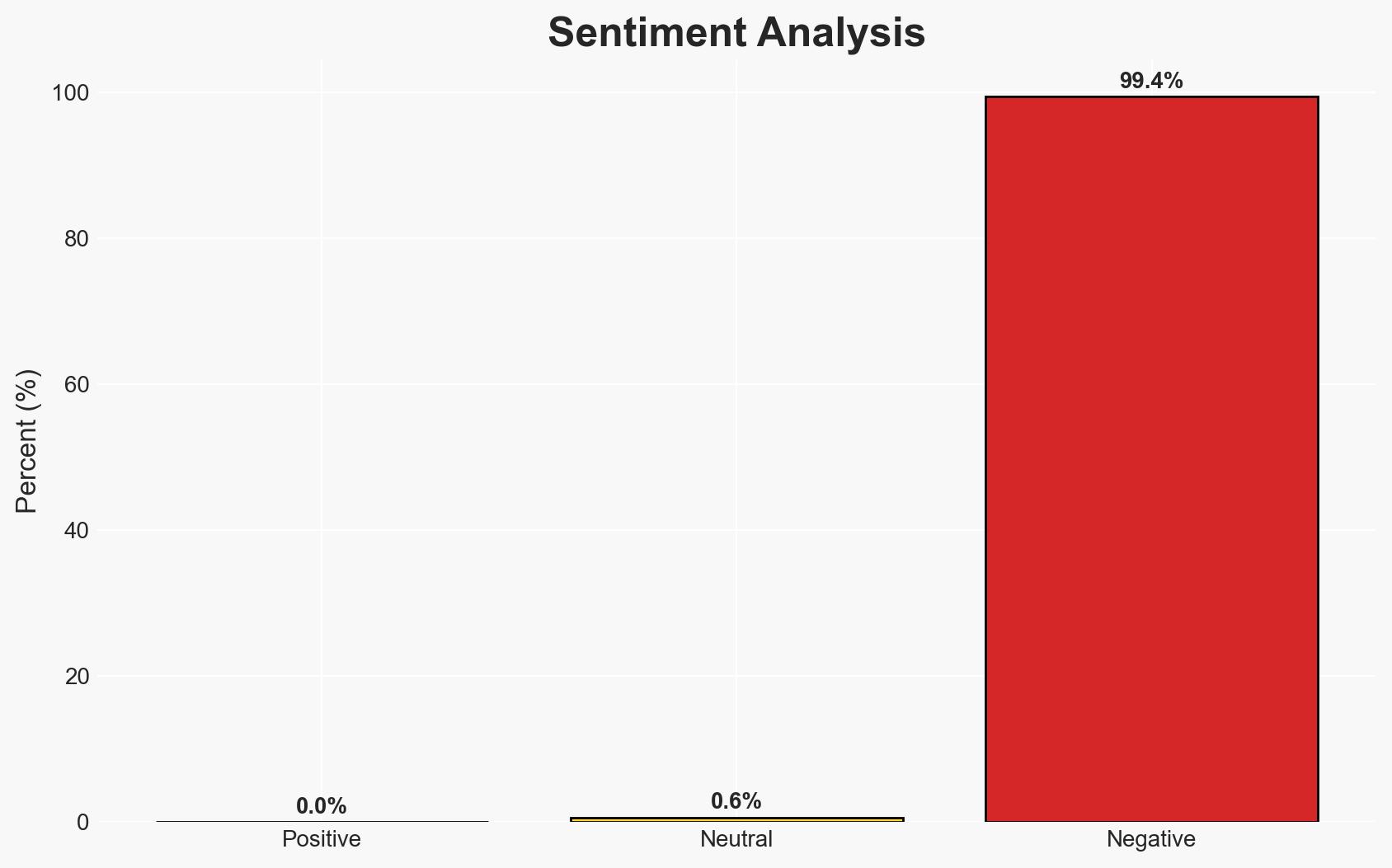
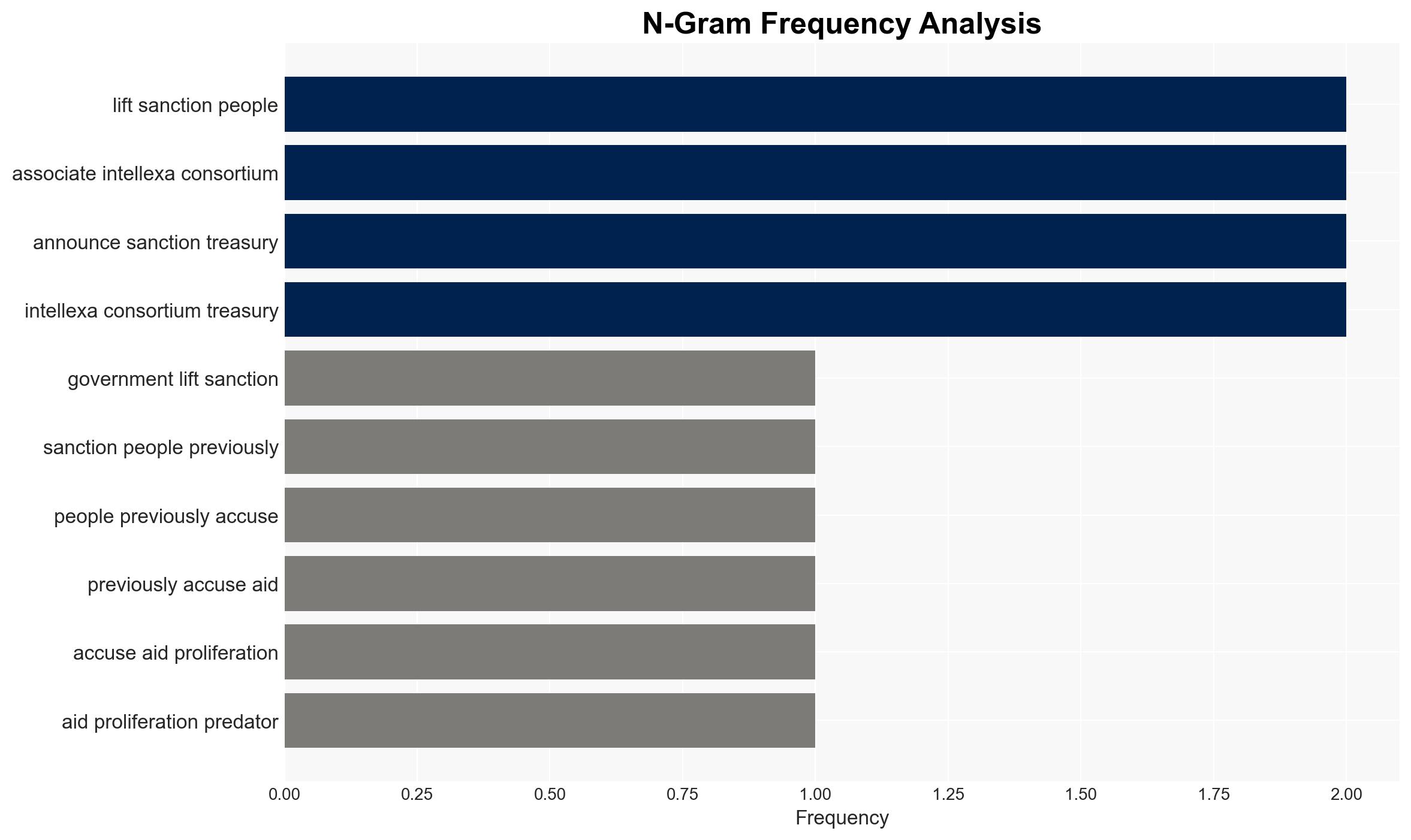
The US government has lifted sanctions on three individuals previously accused of aiding in the proliferation of the Predator spyware. This decision may indicate a shift in the US approach to managing international cyber threats, potentially affecting US national security and foreign relations. The most likely hypothesis is that these individuals have sufficiently demonstrated dissociation from the Intellexa Consortium. Overall confidence in this judgment is moderate.
2. Competing Hypotheses
- Hypothesis A: The individuals have genuinely distanced themselves from the Intellexa Consortium, leading to the lifting of sanctions. Supporting evidence includes the Treasury’s statement on demonstrated measures of separation. Key uncertainties involve the nature and verification of these measures.
- Hypothesis B: The lifting of sanctions is a strategic decision by the US government to recalibrate its stance on international cyber threats, possibly to facilitate diplomatic engagements or due to insufficient evidence. Contradicting evidence includes the ongoing sanctions against other entities associated with Intellexa.
- Assessment: Hypothesis A is currently better supported due to the Treasury’s explicit mention of the individuals’ efforts to separate from Intellexa. Indicators that could shift this judgment include new evidence of continued involvement with Intellexa or changes in US diplomatic priorities.
3. Key Assumptions and Red Flags
- Assumptions: The individuals’ separation from Intellexa is genuine and verifiable; US policy decisions are based on credible intelligence; Intellexa remains a significant cyber threat.
- Information Gaps: Details on the measures taken by the individuals to dissociate from Intellexa; the rationale behind the US government’s decision-making process.
- Bias & Deception Risks: Potential cognitive bias in interpreting Treasury’s actions as purely administrative; risk of manipulation by the individuals or Intellexa to appear compliant.
4. Implications and Strategic Risks
This development could influence international perceptions of US cyber policy and affect the operational landscape for cyber threats. It may also impact US relations with countries involved in the Intellexa network.
- Political / Geopolitical: Potential recalibration of US diplomatic relations with countries linked to Intellexa.
- Security / Counter-Terrorism: Possible changes in the threat landscape if Intellexa’s capabilities are perceived as diminished.
- Cyber / Information Space: Implications for global cyber norms and the proliferation of surveillance technologies.
- Economic / Social: Limited direct economic impact, but potential social implications if surveillance technologies are misused.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Intellexa’s activities for compliance; engage with international partners to assess the impact of the decision.
- Medium-Term Posture (1–12 months): Develop resilience measures against potential misuse of commercial spyware; strengthen partnerships for intelligence sharing.
- Scenario Outlook: Best: Individuals remain dissociated, reducing Intellexa’s threat. Worst: Re-engagement with Intellexa, increasing cyber threats. Most-Likely: Continued monitoring and diplomatic engagement.
6. Key Individuals and Entities
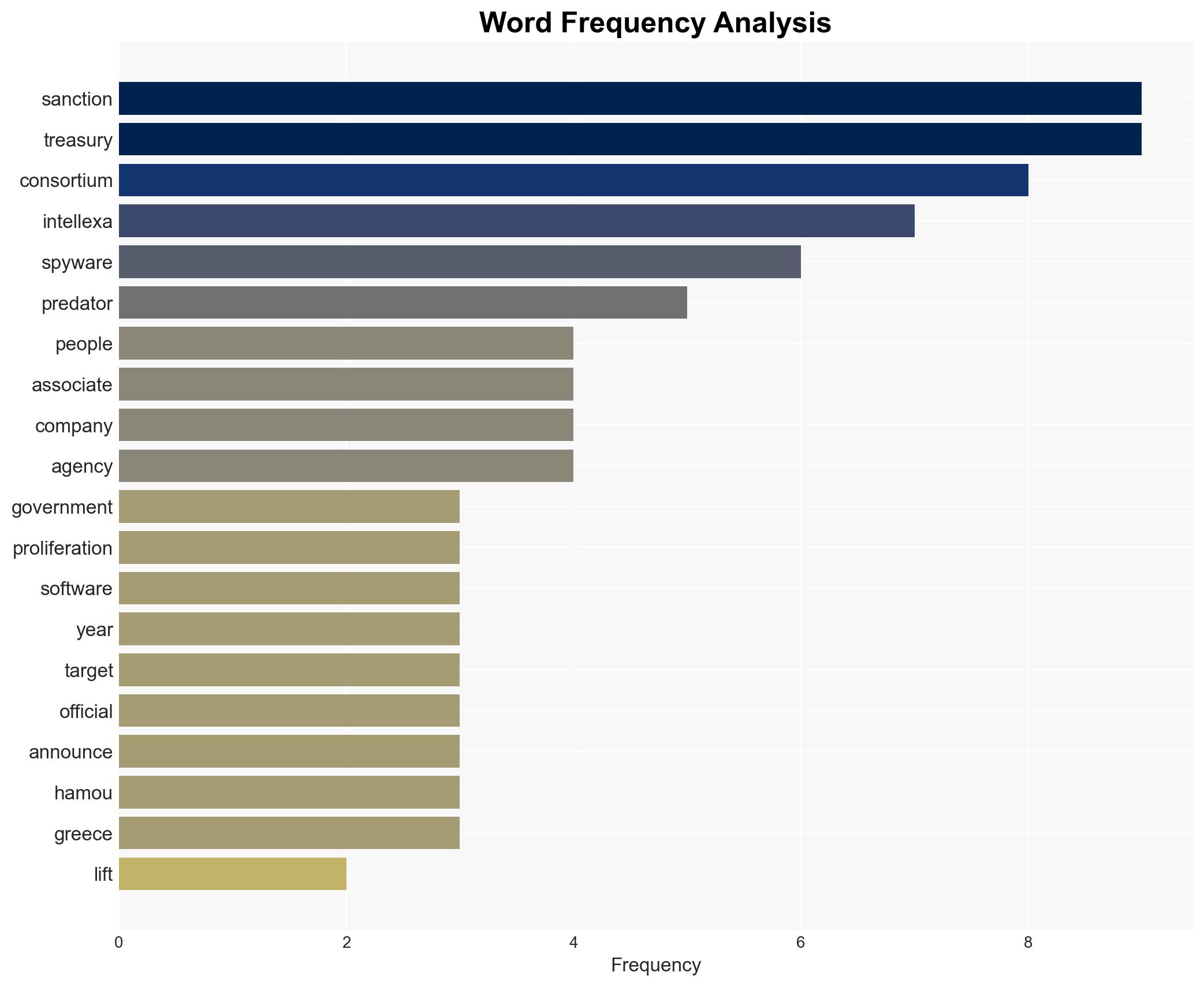
- Sara Aleksandra Fayssal Hamou
- Andrea Nicola Constantino Hermes Gambazzi
- Merom Harpaz
- Intellexa Consortium
- Tal Dilian
7. Thematic Tags
cybersecurity, sanctions, cyber-espionage, international relations, surveillance technology, US Treasury, Intellexa Consortium
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us