US Sanctions 10 North Korean Entities for Laundering 127M in Crypto and IT Fraud – Internet
Published on: 2025-11-05
Intelligence Report: US Sanctions 10 North Korean Entities for Laundering 127M in Crypto and IT Fraud – Internet
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that North Korea is systematically using cyber operations and fraudulent employment schemes to fund its weapons programs, with a high confidence level. The recommended action is to enhance international cooperation to disrupt these financial networks and increase cybersecurity measures globally.
2. Competing Hypotheses
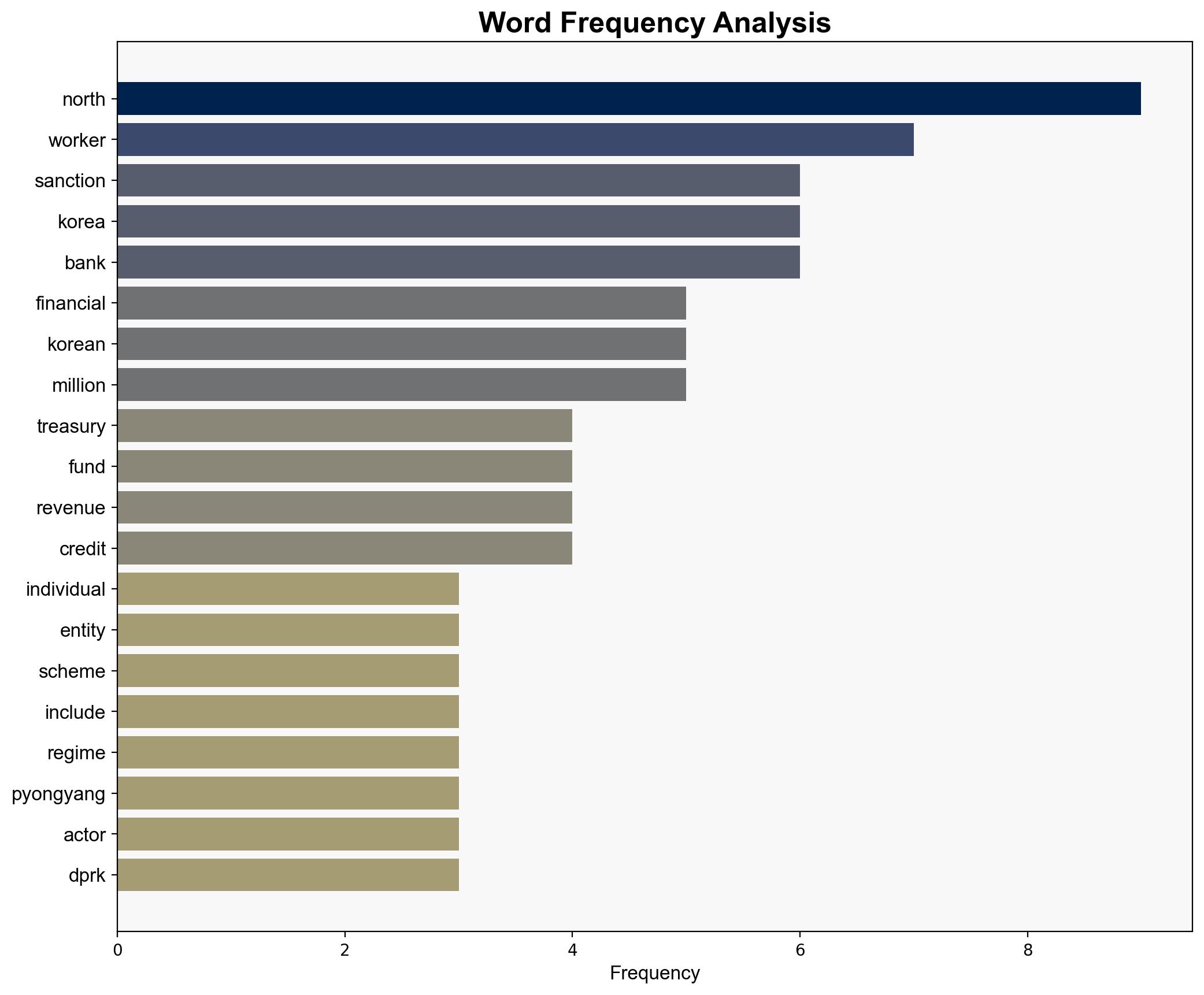
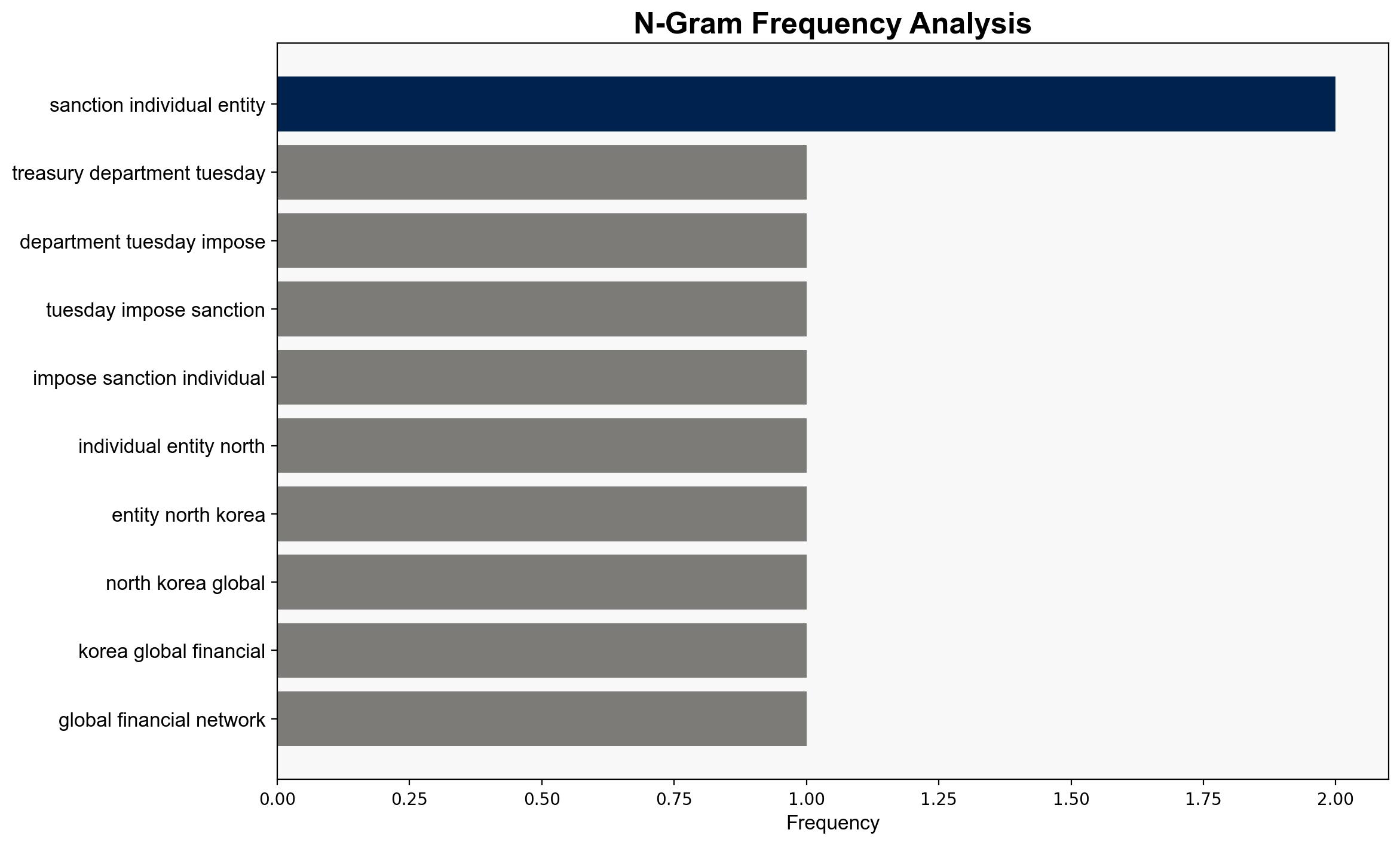
Hypothesis 1: North Korea is using a coordinated network of cybercriminals and fraudulent employment schemes to launder money and fund its nuclear weapons program. This involves sophisticated cyber operations and collaboration with foreign entities to evade sanctions.
Hypothesis 2: The activities are primarily driven by independent cybercriminals within North Korea, with limited state oversight, and the funds are used for a variety of purposes, not solely for weapons development.
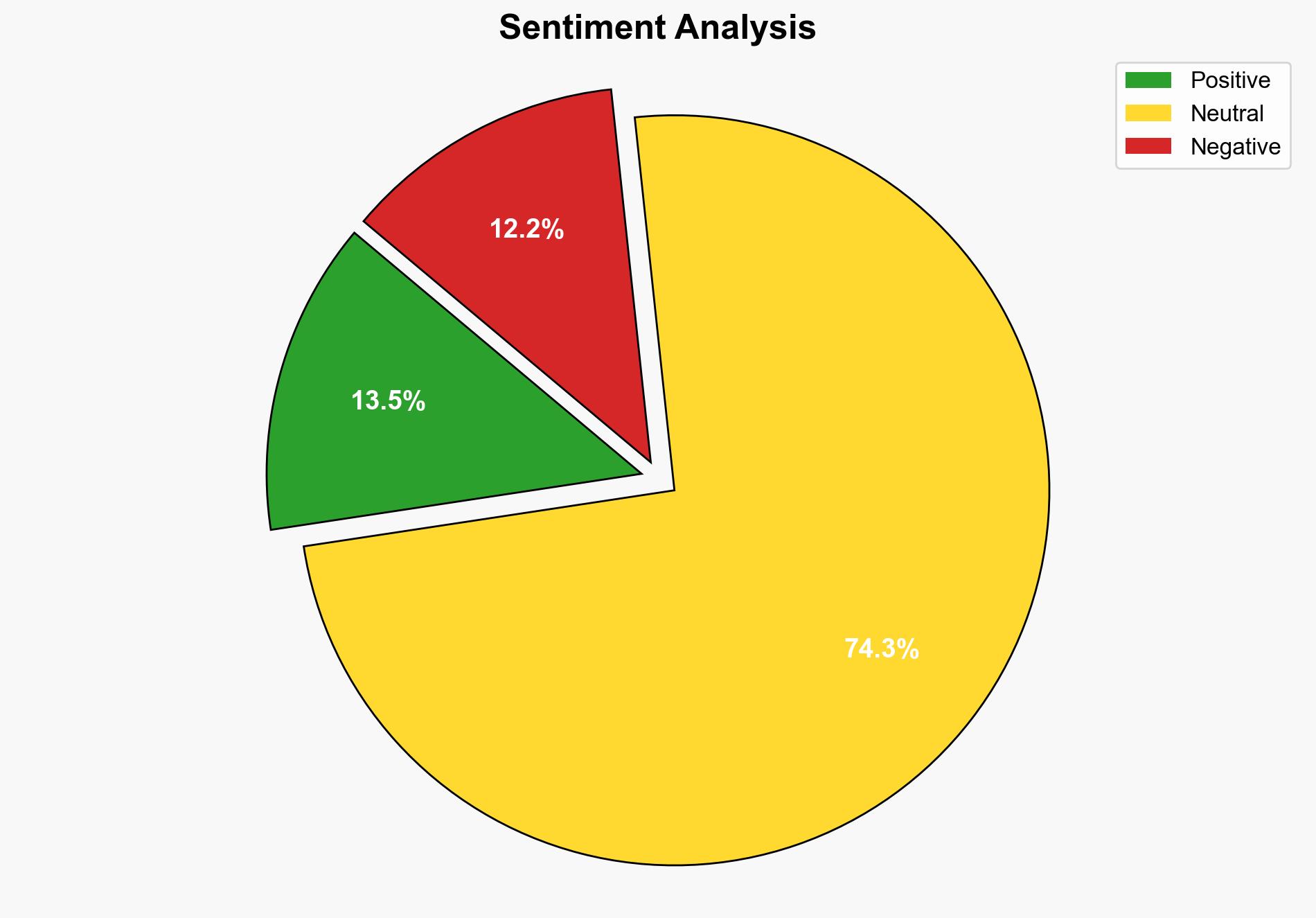
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the structured involvement of state-sponsored actors and the strategic alignment with North Korea’s known objectives.
3. Key Assumptions and Red Flags
– Assumption: North Korea’s state apparatus directly controls and benefits from these operations.
– Red Flag: The potential underestimation of the role of non-state actors or independent cybercriminals.
– Blind Spot: Limited visibility into the internal decision-making processes of North Korean entities and their foreign partners.
4. Implications and Strategic Risks
– The continued success of these operations could embolden North Korea to expand its cyber capabilities, posing a greater threat to global financial systems.
– Potential escalation in cyber warfare tactics as North Korea seeks to counteract sanctions.
– Increased geopolitical tensions, particularly with countries implicated in facilitating these transactions, such as China and Russia.
5. Recommendations and Outlook
- Enhance international collaboration on cybersecurity to detect and prevent similar schemes.
- Strengthen sanctions enforcement and close loopholes exploited by North Korean entities.
- Best-case scenario: Successful disruption of North Korea’s financial networks, reducing its ability to fund weapons programs.
- Worst-case scenario: Escalation of cyber attacks targeting critical infrastructure in retaliation.
- Most likely scenario: Continued cat-and-mouse game with incremental improvements in detection and prevention.
6. Key Individuals and Entities
– Jang Kuk Chol
– Jang Ho Jong
– Son (affiliated with Credit Bank)
– Yong Su (KMCTC)
– Ryu Jong (Credit Bank)
– Ho Yong Chol
– Han Hong Gil
– Jong Sung Hyok
– Choe Chun Pom
– Ri Jin Hyok
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus