Veeam Data Platform v13 strengthens AI-driven analysis – Help Net Security
Published on: 2025-11-19
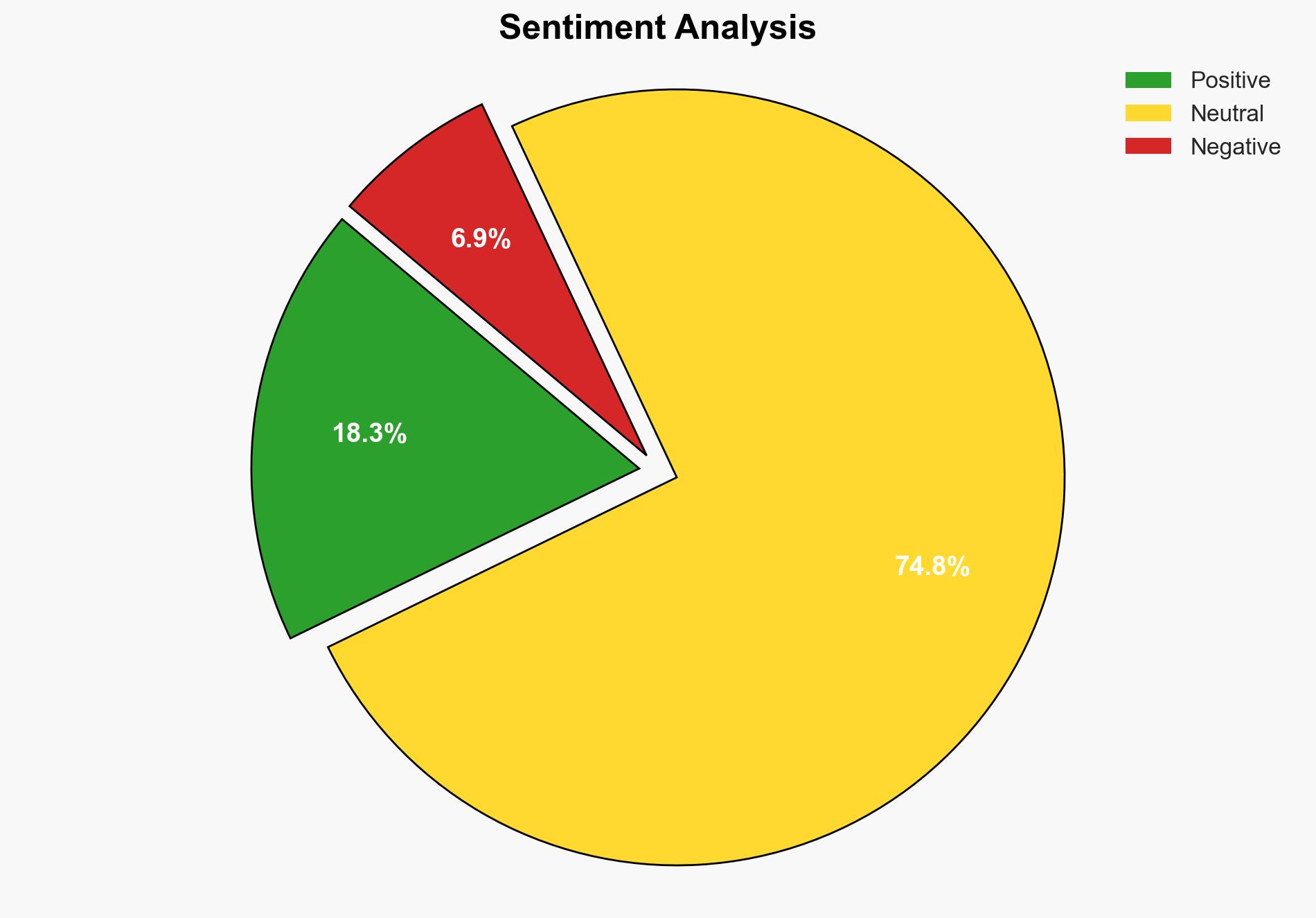
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Veeam Data Platform v13 and AI-Driven Analysis
1. BLUF (Bottom Line Up Front)
The Veeam Data Platform v13 represents a significant advancement in AI-driven cybersecurity capabilities, enhancing threat detection and response. The most supported hypothesis is that Veeam’s innovations will strengthen organizational resilience against cyber threats, particularly in cloud environments. Confidence level: Moderate. Recommended action: Organizations should evaluate integrating Veeam’s platform to enhance their cybersecurity posture, especially those heavily reliant on cloud infrastructure.
2. Competing Hypotheses
Hypothesis 1: Veeam’s new platform will significantly enhance cybersecurity for organizations, particularly those using cloud and hybrid environments, by providing advanced AI-driven threat detection and response capabilities.
Hypothesis 2: Despite the enhancements, Veeam’s platform may face challenges in adoption due to integration complexities, potential security vulnerabilities, or resistance from organizations already committed to other cybersecurity solutions.
Hypothesis 1 is more likely, given the platform’s comprehensive features and integration capabilities with existing security tools, which align with current cybersecurity needs and trends.
3. Key Assumptions and Red Flags
Assumptions:
– Organizations are seeking advanced AI-driven cybersecurity solutions.
– Veeam’s integration with existing platforms will be seamless and effective.
Red Flags:
– Potential over-reliance on AI could lead to vulnerabilities if not properly managed.
– The possibility of undisclosed security flaws in the new platform.
4. Implications and Strategic Risks
The adoption of Veeam’s platform could lead to a shift in the cybersecurity landscape, with increased emphasis on AI-driven solutions. However, there is a risk of escalating cyber threats as adversaries adapt to these new defenses. Economically, organizations may face increased costs associated with integrating and maintaining the new platform. Politically, this could influence cybersecurity policy development, emphasizing AI and cloud security.
5. Recommendations and Outlook
- Organizations should conduct a thorough risk assessment before integrating Veeam’s platform, focusing on potential vulnerabilities and integration challenges.
- Best-case scenario: Successful integration leads to enhanced cybersecurity and reduced threat exposure.
- Worst-case scenario: Integration challenges or security flaws lead to increased vulnerability.
- Most-likely scenario: Gradual adoption with iterative improvements as organizations adapt to the new capabilities.
6. Key Individuals and Entities
Veeam Software (Developer of the platform)
7. Thematic Tags
Cybersecurity, AI-Driven Analysis, Cloud Security, Threat Detection, Data Resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us