Video captures ‘ambush’ when residents come home with AirTag taped on car – USA Today
Published on: 2025-10-17
Intelligence Report: Video captures ‘ambush’ when residents come home with AirTag taped on car – USA Today
1. BLUF (Bottom Line Up Front)
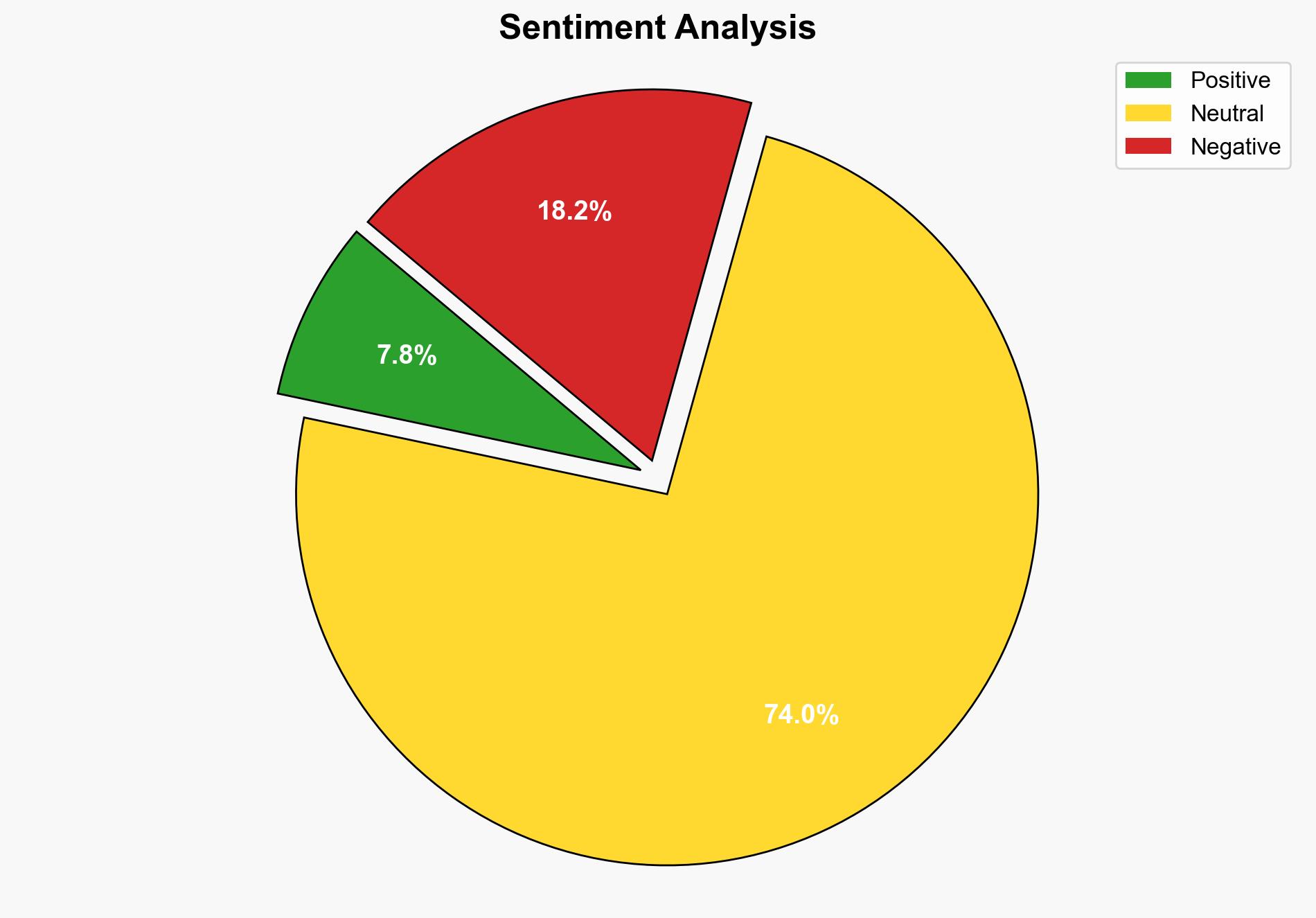
The most supported hypothesis is that the use of AirTags in this context was part of a premeditated criminal strategy to facilitate robbery by tracking the victim’s movements. Confidence in this assessment is moderate due to the reliance on available evidence and the potential for other interpretations. Recommended action includes enhancing public awareness about the misuse of tracking devices and encouraging law enforcement to develop countermeasures against such tactics.
2. Competing Hypotheses
1. **Hypothesis A**: The AirTag was used intentionally by the suspects to track and ambush the victim as part of a coordinated robbery attempt.
2. **Hypothesis B**: The AirTag was coincidentally attached to the vehicle and unrelated to the robbery, possibly placed by a third party for non-criminal purposes.
Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported by the evidence, including the timing of the ambush and the arrest of suspects linked to the incident. Hypothesis B lacks direct evidence and is less plausible given the context.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the suspects had prior knowledge of the AirTag’s location and functionality. Another assumption is that the AirTag was not placed by someone unrelated to the suspects.
– **Red Flags**: The absence of direct evidence linking the suspects to the placement of the AirTag. Additionally, the lack of a response from Apple regarding the misuse of their product raises questions about corporate responsibility.
4. Implications and Strategic Risks
The misuse of consumer tracking technology like AirTags poses significant risks, including privacy violations and facilitating criminal activities. If unchecked, this could lead to increased public fear and potential legal actions against technology companies. There is also a risk of escalation if criminals widely adopt such tactics, potentially leading to more sophisticated and organized crimes.
5. Recommendations and Outlook
- Enhance public education on the potential misuse of tracking devices and how to detect them.
- Encourage technology companies to implement stricter security measures and provide tools for users to detect unauthorized tracking.
- Law enforcement should develop specialized units to address technology-facilitated crimes.
- Scenario Projections:
- Best Case: Increased awareness and preventive measures reduce the misuse of tracking devices.
- Worst Case: Criminals adapt and refine their tactics, leading to more sophisticated crimes.
- Most Likely: Incremental improvements in public awareness and technology security measures mitigate some risks.
6. Key Individuals and Entities
– Luis Charles
– Omardy Maldonado Rodriguez
– Apple Inc.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus