Vulnerabilities in NPM, PNPM, VLT, and Bun allow bypassing of supply chain protections, risking malicious cod…
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
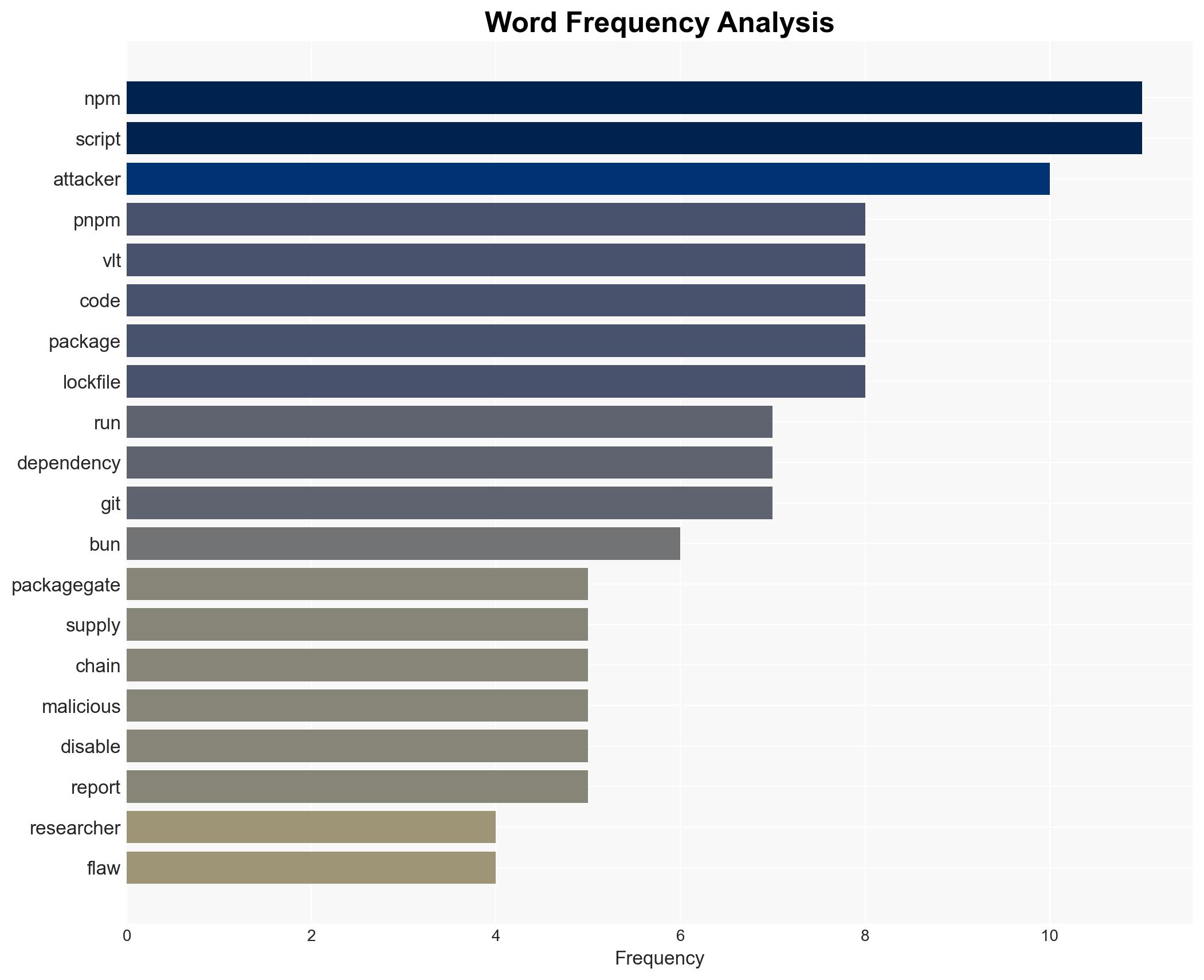
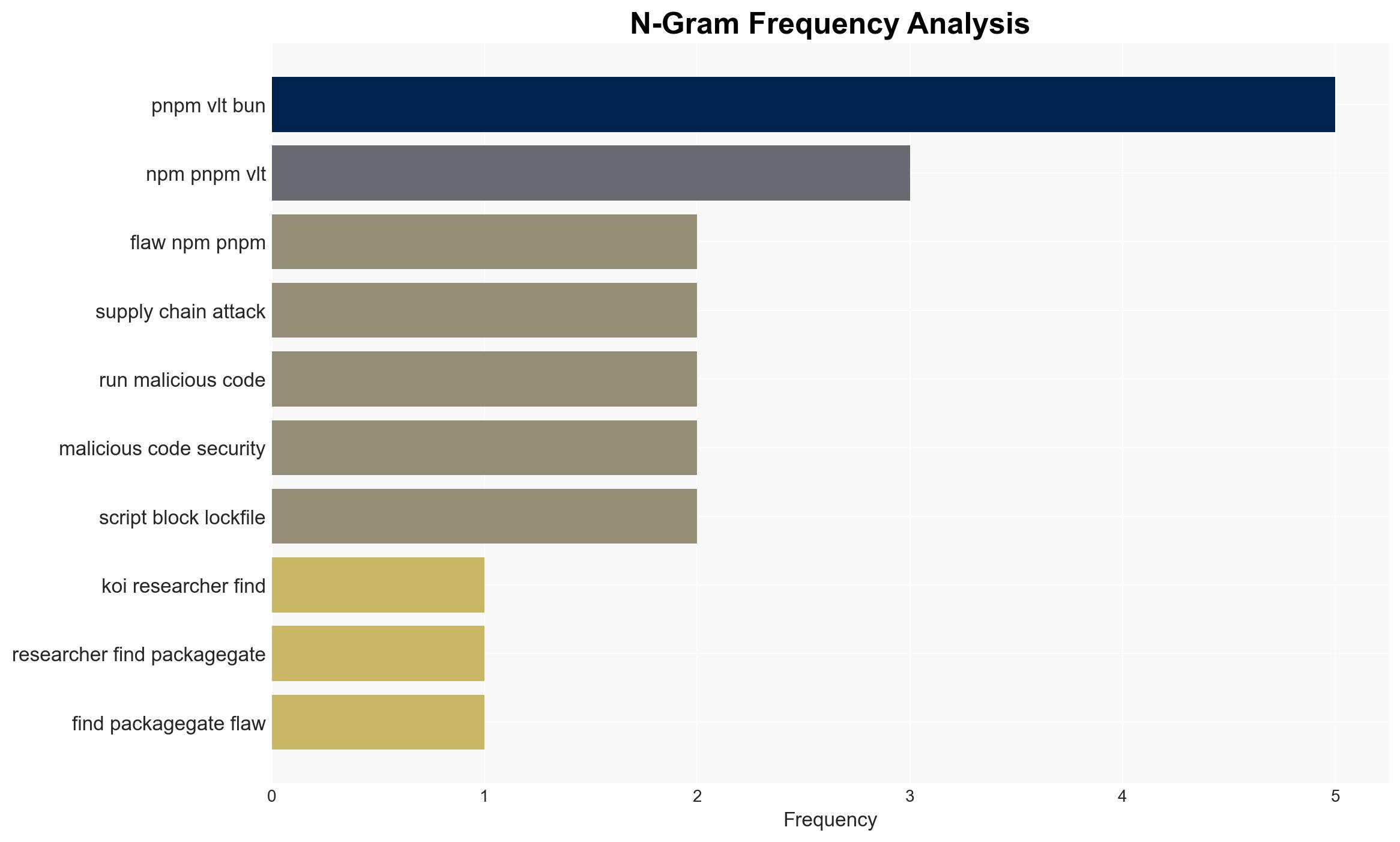
Intelligence Report: PackageGate bugs let attackers bypass protections in NPM PNPM VLT and Bun
1. BLUF (Bottom Line Up Front)
The discovery of “PackageGate” vulnerabilities in major JavaScript package managers like NPM, PNPM, VLT, and Bun poses a significant risk to software supply chain security, potentially affecting numerous organizations relying on these tools. The most likely hypothesis is that these vulnerabilities will lead to increased exploitation attempts, particularly in environments that have not yet applied available patches. Overall confidence in this assessment is moderate, given the partial remediation and varying responses from affected entities.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities will be widely exploited by threat actors due to the critical nature of the flaws and the widespread use of affected package managers. This is supported by the history of similar vulnerabilities being exploited and the existence of proof-of-concept exploits. However, the extent of exploitation may be limited by the speed of patch adoption and awareness.
- Hypothesis B: The vulnerabilities will have limited exploitation due to rapid patching by most affected package managers and increased awareness among developers. This is supported by the fact that PNPM, VLT, and Bun have already addressed the issues, reducing the attack surface. However, NPM’s dismissal of the vulnerabilities as expected behavior could undermine this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the critical nature of the vulnerabilities and the potential for exploitation in environments using NPM, which has not addressed the issues. Indicators that could shift this judgment include widespread patch adoption or a significant increase in awareness and mitigation efforts.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are technically feasible to exploit; affected organizations are slow to adopt patches; threat actors have the capability and intent to exploit these flaws.
- Information Gaps: The exact number of organizations using each affected package manager; detailed timelines for patch adoption across different sectors.
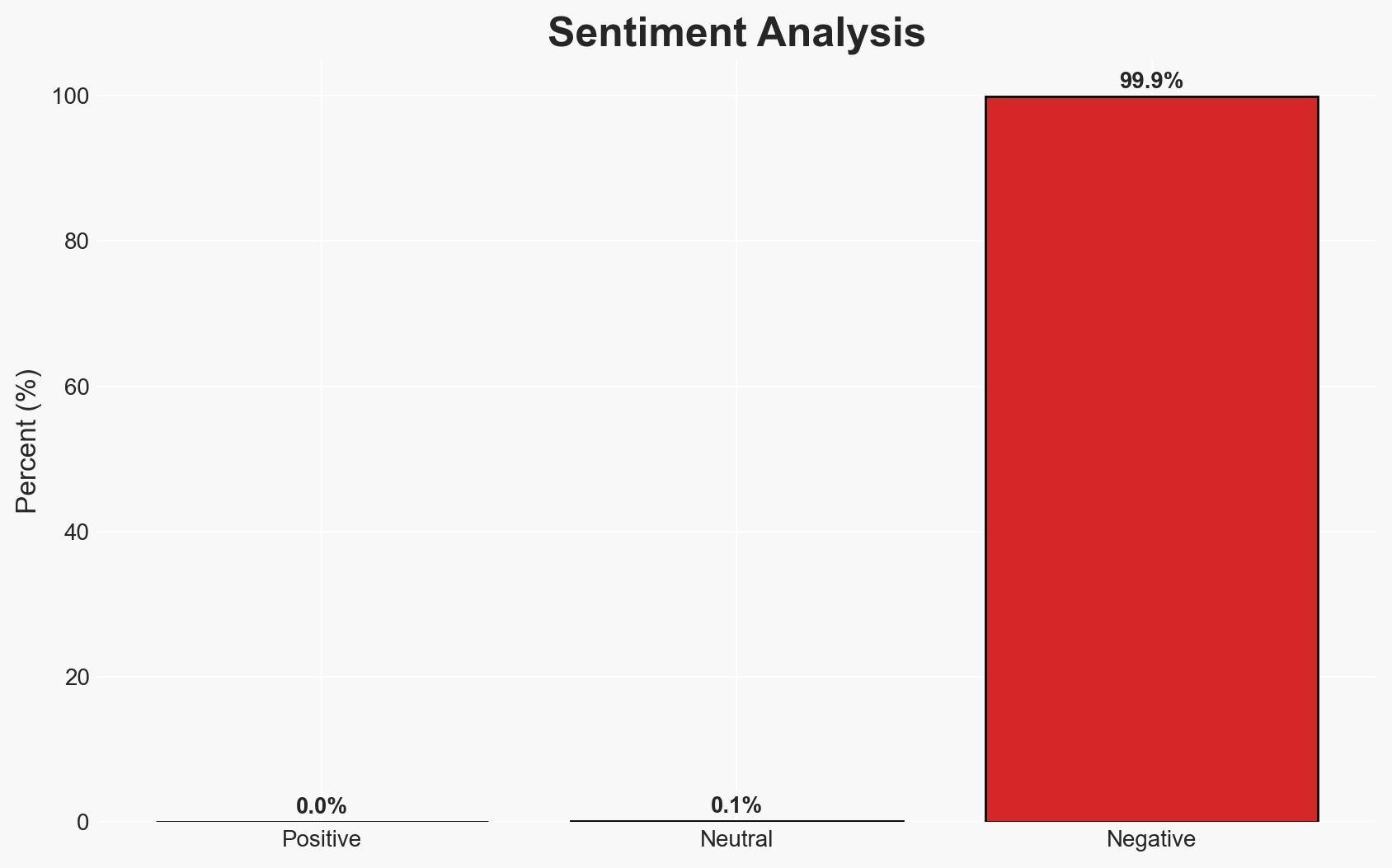
- Bias & Deception Risks: Potential bias in the reporting from security researchers focusing on the severity of the vulnerabilities; possible underestimation of NPM’s response strategy.
4. Implications and Strategic Risks
The discovery of “PackageGate” vulnerabilities could lead to increased cyber threats and necessitate a reevaluation of software supply chain security strategies. Over time, this may influence broader security policies and practices.
- Political / Geopolitical: Potential for increased scrutiny on software supply chain security, possibly leading to regulatory changes.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks exploiting these vulnerabilities, impacting critical infrastructure reliant on JavaScript environments.
- Cyber / Information Space: Increased focus on securing software supply chains and potential shifts in best practices for dependency management.
- Economic / Social: Potential economic impact on organizations facing breaches; increased demand for cybersecurity solutions and expertise.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage organizations to apply available patches immediately; increase monitoring for signs of exploitation; conduct awareness campaigns on the risks associated with these vulnerabilities.
- Medium-Term Posture (1–12 months): Develop and promote best practices for software supply chain security; foster partnerships with cybersecurity firms to enhance detection and response capabilities.
- Scenario Outlook:
- Best Case: Rapid patch adoption and increased awareness lead to minimal exploitation.
- Worst Case: Widespread exploitation results in significant breaches and economic damage.
- Most Likely: Moderate exploitation occurs, prompting a gradual shift in security practices.
6. Key Individuals and Entities
- Security firm Koi
- NPM
- PNPM
- VLT
- Bun
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, software supply chain, vulnerabilities, JavaScript, package managers, threat actors, patch management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us