Watch out your work mobile apps could be a huge security risk – here’s what to look out for – TechRadar
Published on: 2025-04-17
Intelligence Report: Watch out your work mobile apps could be a huge security risk – here’s what to look out for – TechRadar
1. BLUF (Bottom Line Up Front)
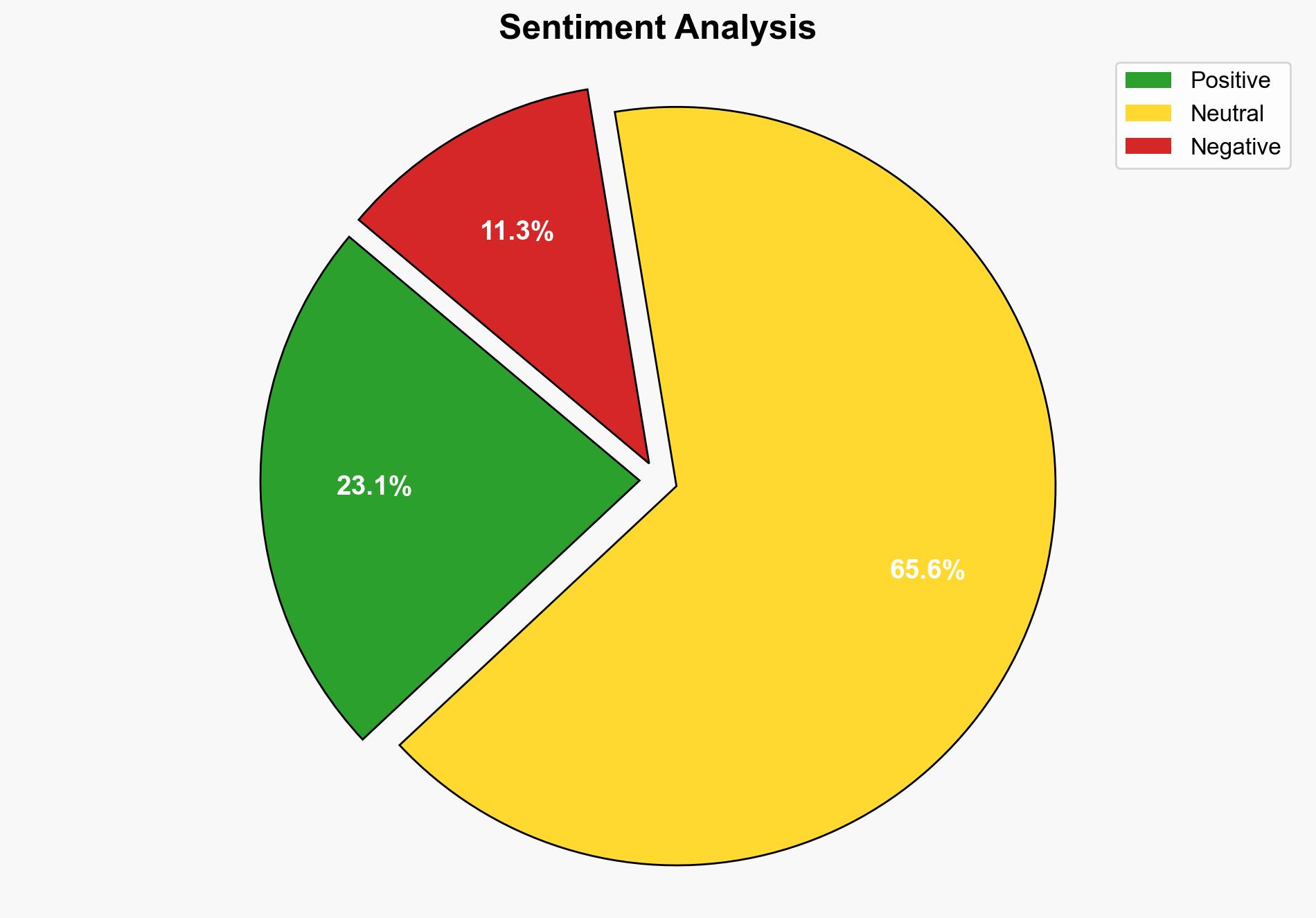
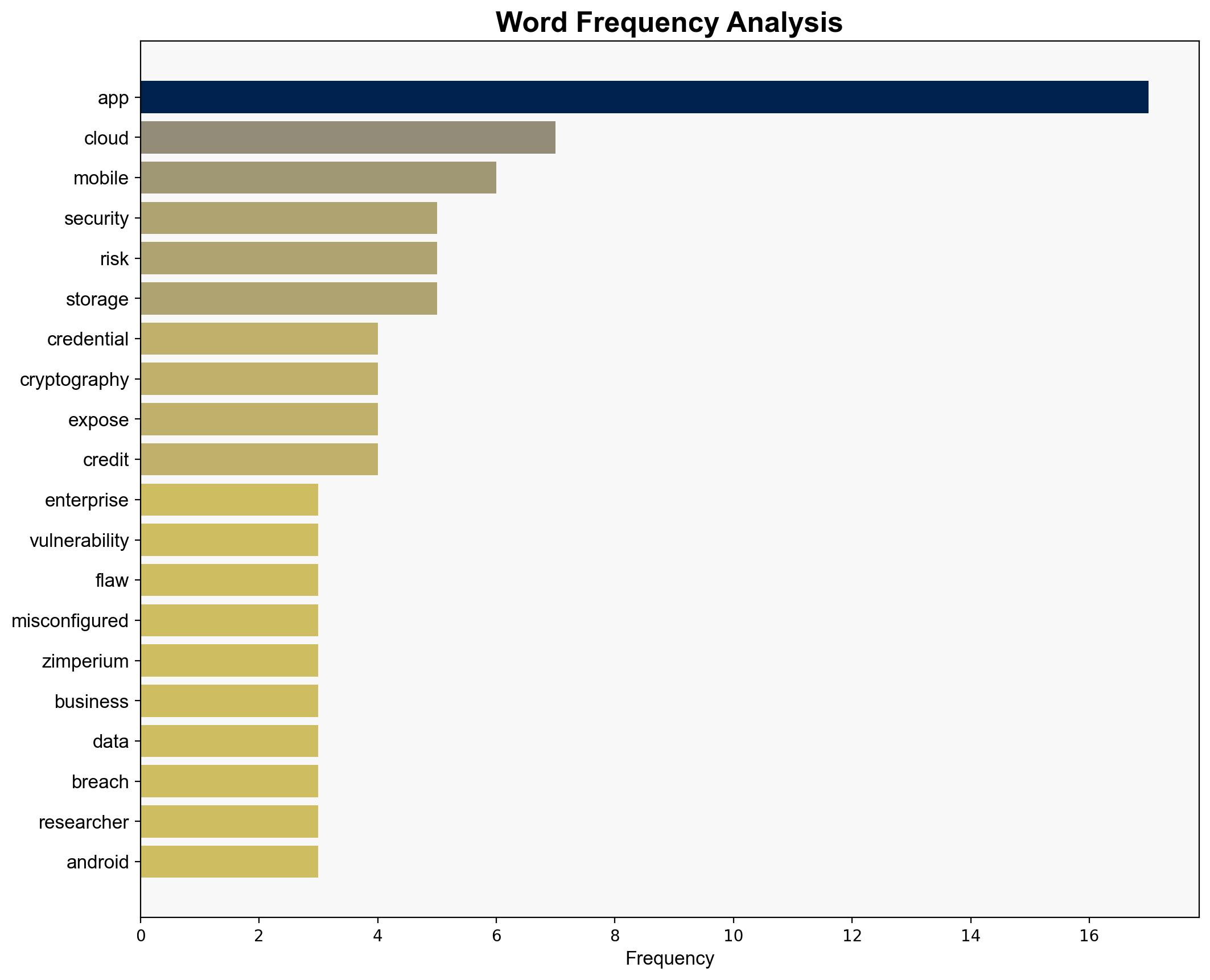
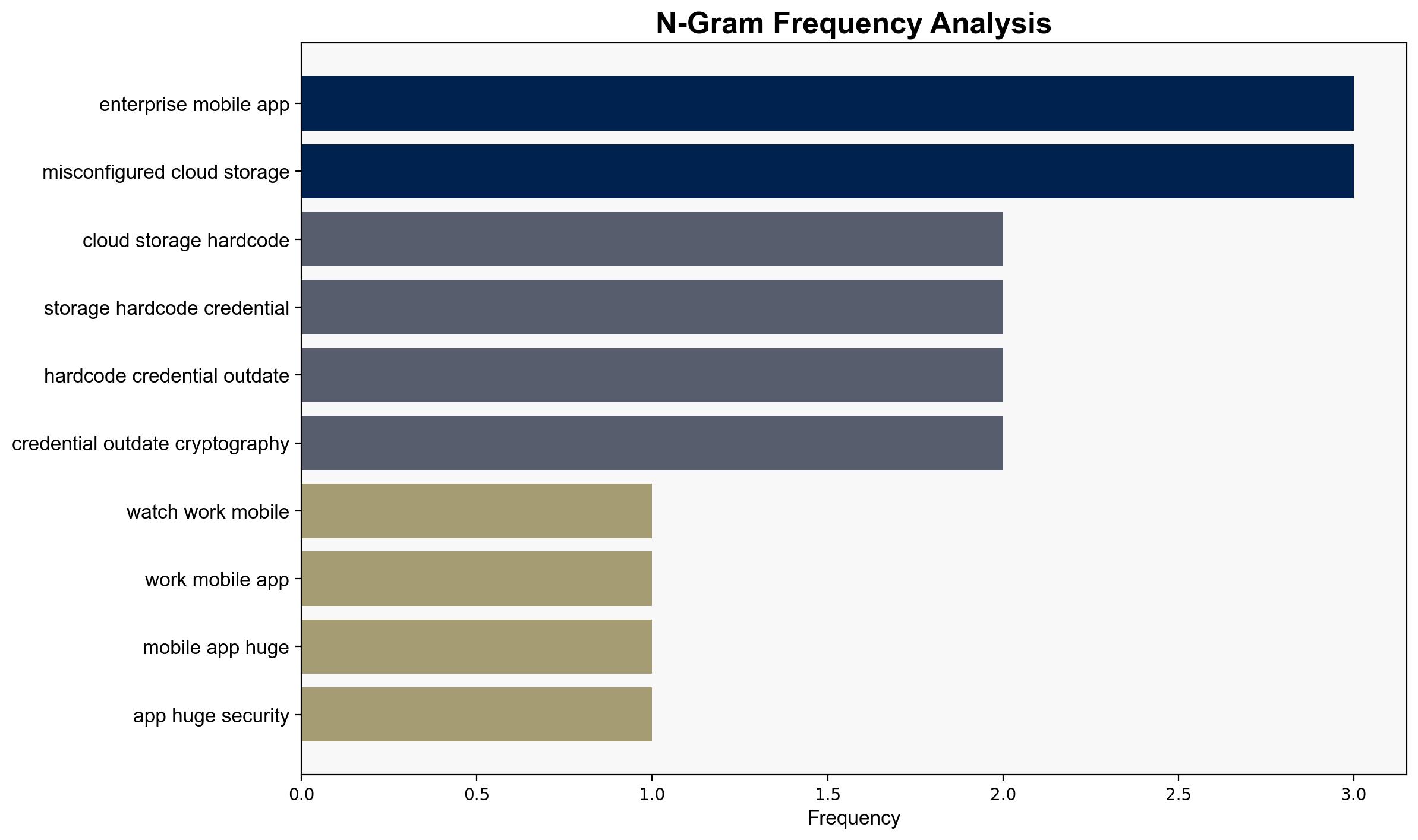
Enterprise mobile apps pose significant security risks due to vulnerabilities such as misconfigured cloud storage, hardcoded credentials, and outdated cryptography. A study by Zimperium highlights that a large percentage of these apps, particularly on iOS, are susceptible to data breaches. It is crucial for organizations to enhance their mobile app security protocols to prevent potential data leaks and associated repercussions.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The primary causes of security breaches in enterprise mobile apps include inadequate security configurations, reliance on outdated cryptographic methods, and insufficient oversight of app behavior. Motivations behind potential attacks could range from financial gain to corporate espionage.
SWOT Analysis
Strengths: Availability of advanced security tools and expertise to address vulnerabilities.
Weaknesses: High prevalence of outdated security practices and lack of visibility into app behavior.
Opportunities: Implementation of comprehensive app security audits and adoption of best practices in cryptography.
Threats: Increasing sophistication of cyber threats targeting mobile platforms and potential regulatory fines.
Indicators Development
Warning signs of emerging cyber threats include increased reports of data breaches, detection of exposed credentials, and identification of apps using weak cryptographic methods.
3. Implications and Strategic Risks
The widespread vulnerabilities in enterprise mobile apps present significant risks to data security and organizational integrity. These risks can lead to financial losses, damage to reputation, and compliance issues. The economic impact of data breaches can be substantial, affecting both the private and public sectors.
4. Recommendations and Outlook
- Conduct regular security audits of mobile apps to identify and rectify vulnerabilities.
- Implement robust encryption standards and key management practices.
- Enhance monitoring of app behavior to detect and respond to security threats promptly.
- Scenario-based projections suggest that without intervention, the frequency and severity of data breaches will increase, necessitating immediate action to bolster defenses.
5. Key Individuals and Entities
Zimperium