Web services giant Aruba spoofed in major phishing scam – here’s what to look out for to stay safe – TechRadar
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Web services giant Aruba spoofed in major phishing scam – here’s what to look out for to stay safe – TechRadar
1. BLUF (Bottom Line Up Front)
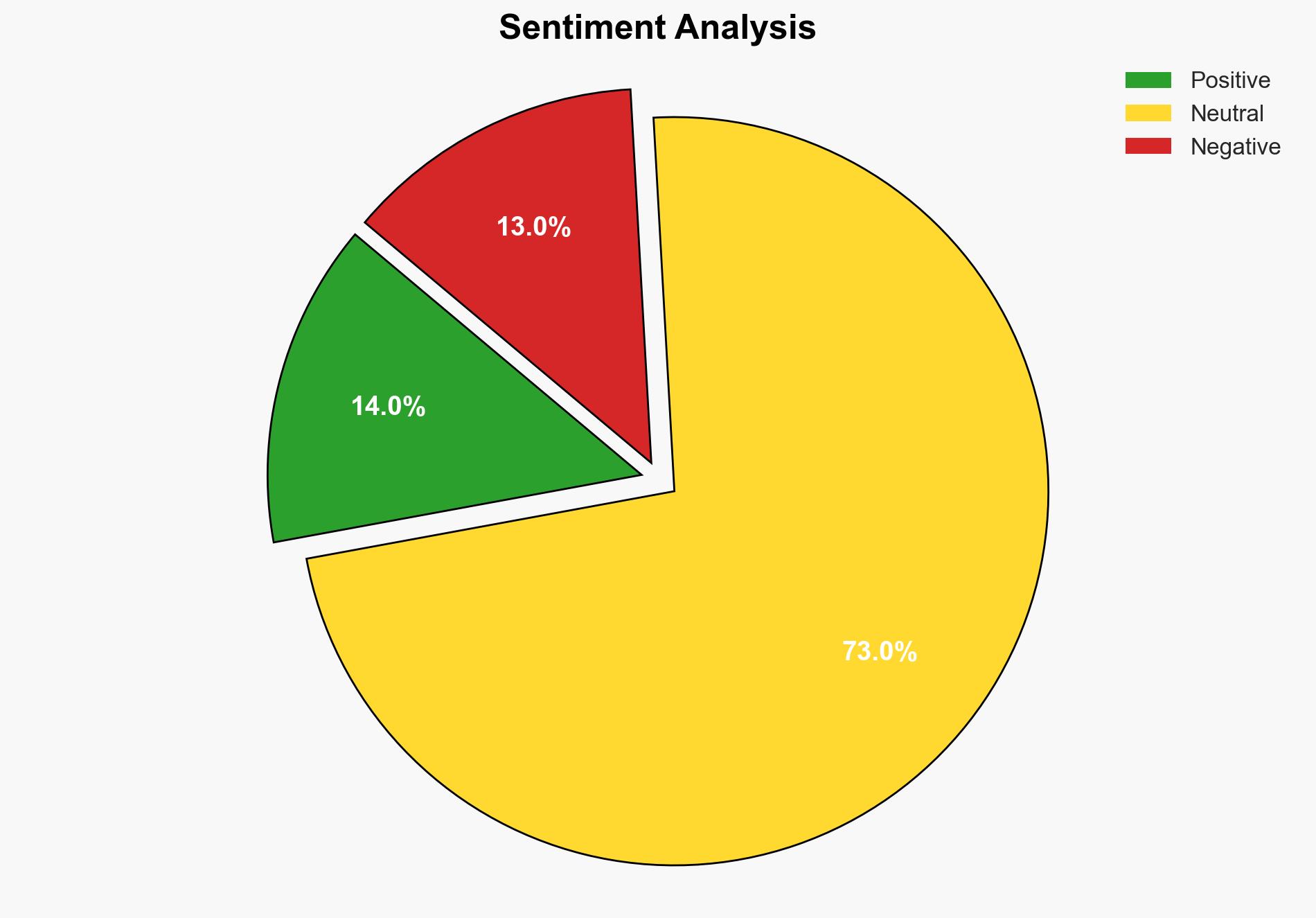
The phishing scam targeting Aruba users represents a significant cybersecurity threat due to its sophisticated automation and large-scale credential theft capabilities. The most supported hypothesis is that this operation is conducted by a highly skilled cybercriminal group aiming for financial gain through credential theft and resale. Confidence level: Moderate. Recommended action includes enhancing cybersecurity measures, user education, and collaboration with cybersecurity firms to mitigate risks.
2. Competing Hypotheses
Hypothesis 1: The phishing operation is orchestrated by a highly skilled cybercriminal group aiming to steal and monetize user credentials on a large scale.
Hypothesis 2: The phishing operation is a state-sponsored initiative aimed at compromising critical infrastructure and gaining access to sensitive information for espionage purposes.
Hypothesis 1 is more likely due to the use of financial gain tactics, such as selling credentials on the dark web, and the absence of geopolitical indicators typically associated with state-sponsored attacks.
3. Key Assumptions and Red Flags
Assumptions: The phishing kit’s sophistication implies a high level of technical expertise. The choice of Aruba as a target suggests a focus on high-value targets.
Red Flags: The use of CAPTCHA and Telegram bots indicates efforts to evade detection and automate credential theft, which are hallmarks of organized cybercrime.
Deception Indicators: The phishing emails mimic official communications, increasing the likelihood of user deception.
4. Implications and Strategic Risks
The phishing scam poses significant risks, including potential breaches of sensitive business data, financial losses, and reputational damage to Aruba and its users. Escalation scenarios include increased cyberattacks on other critical infrastructure entities and potential economic impacts due to compromised business operations.
5. Recommendations and Outlook
- Actionable Steps: Implement advanced threat detection systems, conduct user awareness training, and collaborate with cybersecurity firms to monitor and respond to phishing threats.
- Best Scenario: Enhanced security measures prevent further credential theft, and the perpetrators are identified and apprehended.
- Worst Scenario: The phishing operation expands, leading to widespread data breaches and significant economic impacts.
- Most-likely Scenario: Continued phishing attempts with varying degrees of success, necessitating ongoing vigilance and adaptation of security strategies.
6. Key Individuals and Entities
Group-IB (Cybersecurity firm that identified the phishing scam)
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·