What we know about Scattered Spider the hacker group targeting airlines – ABC News (AU)
Published on: 2025-07-02
Intelligence Report: What we know about Scattered Spider the hacker group targeting airlines – ABC News (AU)
1. BLUF (Bottom Line Up Front)
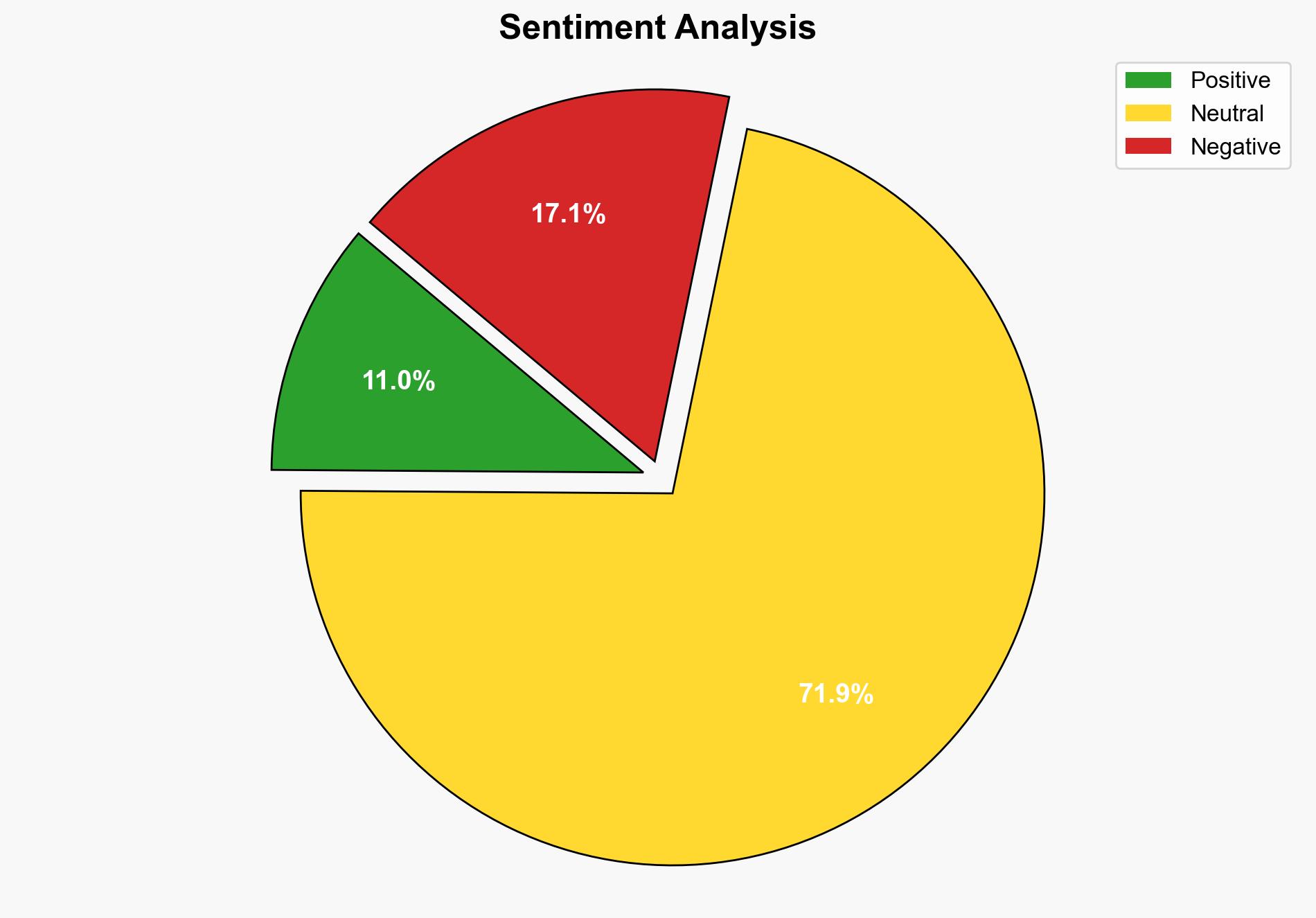
Scattered Spider, a highly aggressive hacking group, has intensified its focus on the airline sector, posing significant cybersecurity threats. Recent incidents include a major attack on Qantas, exposing millions of customer accounts. The group’s tactics, including social engineering and multi-factor authentication fatigue, highlight vulnerabilities in organizational security protocols. Immediate action is recommended to bolster defenses and mitigate potential impacts on the airline industry’s operational integrity.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Scattered Spider’s tactics, such as social engineering and MFA fatigue, are simulated to identify potential weaknesses in airline security systems and develop countermeasures.
Indicators Development
Monitoring for anomalies such as unusual login attempts and unauthorized access requests is crucial for early detection of Scattered Spider’s activities.
Bayesian Scenario Modeling
Probabilistic models predict potential attack vectors and pathways, aiding in the anticipation and prevention of future breaches.
Network Influence Mapping
Mapping the influence and connections of Scattered Spider reveals potential targets and collaborators, enhancing strategic response capabilities.
3. Implications and Strategic Risks
The persistent targeting of the airline sector by Scattered Spider underscores systemic vulnerabilities in critical infrastructure. The group’s ability to disrupt operations and access sensitive customer data poses significant economic and reputational risks. Additionally, the potential for cross-sector attacks could lead to broader implications for national security and economic stability.
4. Recommendations and Outlook
- Enhance cybersecurity training for employees to recognize and respond to social engineering tactics.
- Implement robust multi-factor authentication systems to prevent unauthorized access.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Scenario-based projections:
- Best Case: Strengthened defenses deter future attacks, safeguarding customer data and maintaining operational integrity.
- Worst Case: Continued breaches lead to significant financial losses and erosion of public trust.
- Most Likely: Incremental improvements in security reduce attack frequency but require ongoing vigilance.
5. Key Individuals and Entities
David Tuffley, Daswin De Silva
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus