WhatsApp easily exposed 35 billion people’s phone numbers – GSMArena.com
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
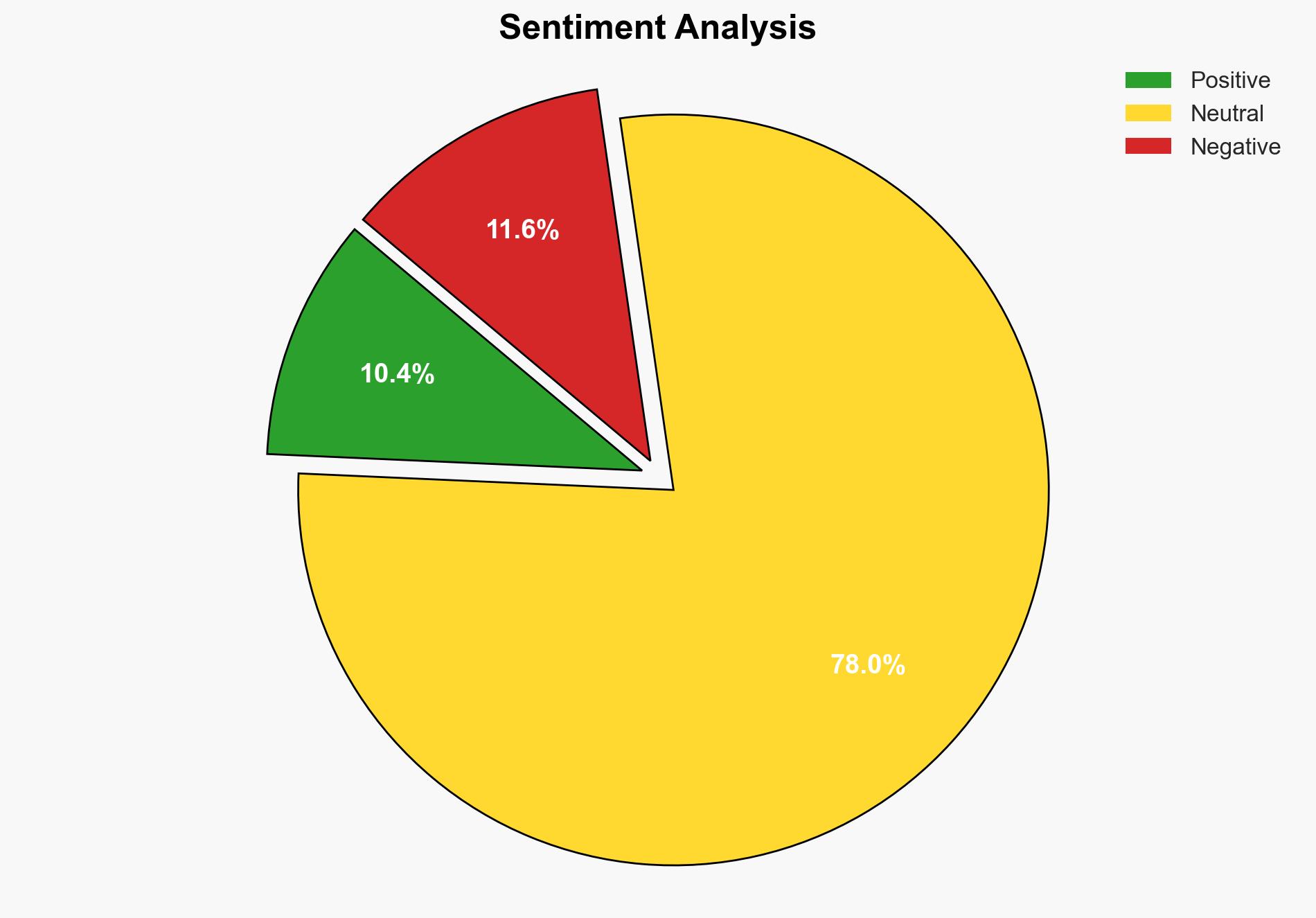
1. BLUF (Bottom Line Up Front)
There is a moderate confidence level that the exposure of WhatsApp users’ phone numbers was due to a systemic vulnerability in the platform’s contact discovery feature, rather than a targeted attack by malicious actors. The most supported hypothesis is that the vulnerability was inadvertently exploited by researchers, but could have been used by malicious entities if not addressed. Recommended actions include enhancing security protocols, conducting a thorough audit of the platform’s privacy settings, and implementing user education on privacy controls.
2. Competing Hypotheses
Hypothesis 1: The exposure of phone numbers was due to a vulnerability in WhatsApp’s contact discovery feature, which was unintentionally exploited by researchers. This hypothesis is supported by the fact that the Austrian researcher was able to extract phone numbers without sophisticated hacking techniques, indicating a systemic flaw.
Hypothesis 2: The exposure was the result of a deliberate attack by a malicious actor exploiting a known vulnerability. This hypothesis is less supported due to the lack of evidence of malicious exploitation and the fact that the issue was reported by a researcher rather than discovered through a breach.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the researcher acted in good faith and that Meta’s response to the issue was timely and effective. There is also an assumption that no other actors exploited the vulnerability before it was addressed.
Red Flags: The delay between the notification of the issue in April and the implementation of a rate limit in October could indicate a potential underestimation of the risk by Meta. Additionally, the assurance of no malicious exploitation lacks transparency and independent verification.
4. Implications and Strategic Risks
The exposure of phone numbers poses significant privacy risks, potentially leading to phishing attacks, identity theft, and other cyber threats. If exploited by malicious actors, this could escalate into broader informational and reputational damage for Meta. Politically, it could lead to increased regulatory scrutiny and pressure for stricter data protection laws.
5. Recommendations and Outlook
- Conduct a comprehensive security audit of WhatsApp’s contact discovery and privacy settings.
- Implement enhanced user education on privacy settings and potential risks.
- Engage with regulatory bodies to demonstrate proactive measures in data protection.
- Best-case scenario: The issue is fully resolved with no further exploitation, and Meta enhances its reputation for data security.
- Worst-case scenario: Undetected exploitation leads to significant user data breaches, resulting in legal and financial repercussions for Meta.
- Most-likely scenario: The vulnerability is patched, but Meta faces ongoing scrutiny and must strengthen its cybersecurity measures.
6. Key Individuals and Entities
Meta Platforms, Inc. – Parent company of WhatsApp, responsible for addressing the vulnerability.
Austrian Researcher – Individual who discovered and reported the vulnerability.
7. Thematic Tags
Cybersecurity, Data Privacy, Vulnerability Management, Regulatory Compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us