WhatsApp Used to Distribute Astaroth Banking Trojan in Brazil Through Automated Messaging to Contacts
Published on: 2026-01-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
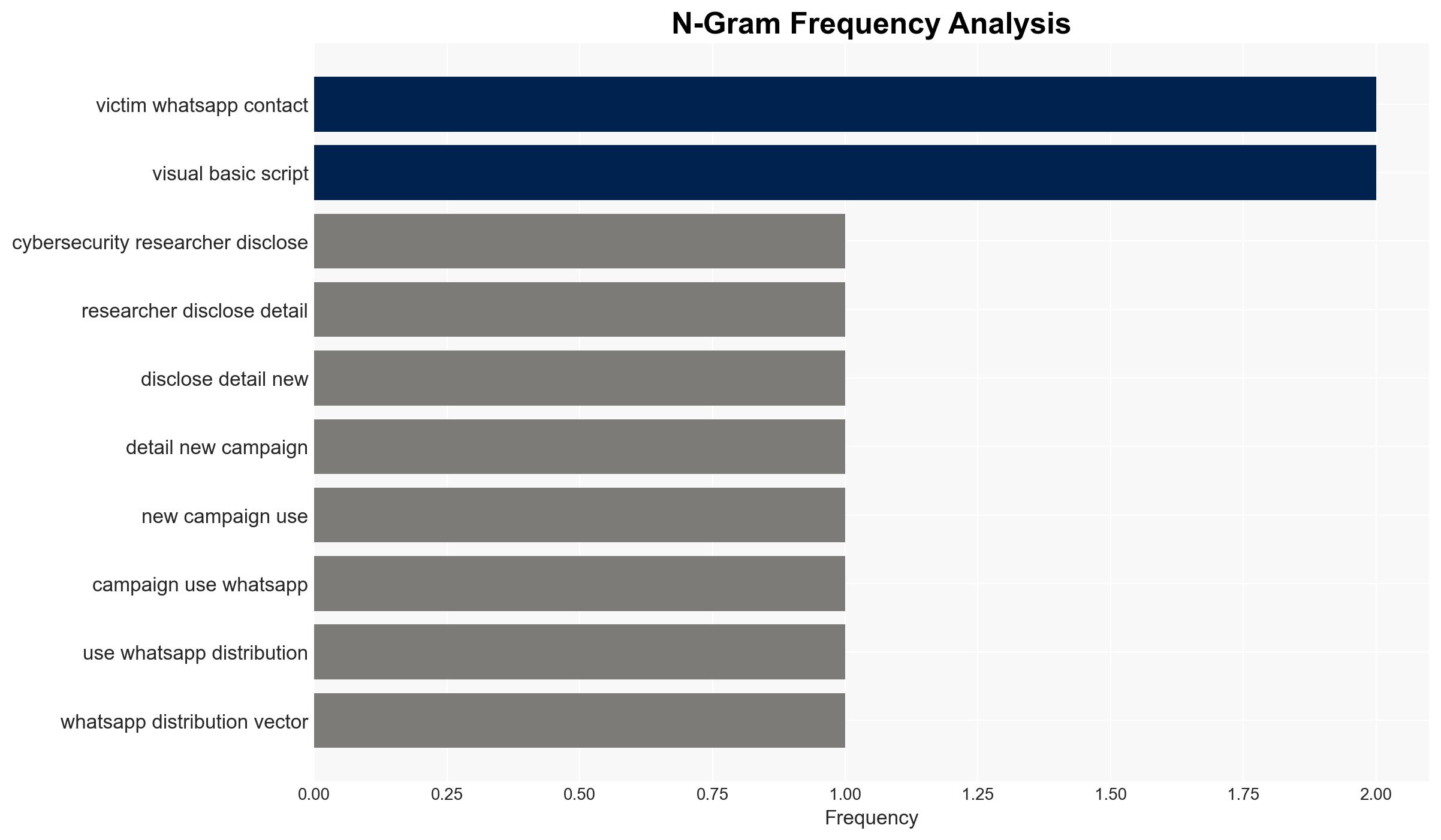
Intelligence Report: WhatsApp Worm Spreads Astaroth Banking Trojan Across Brazil via Contact Auto-Messaging
1. BLUF (Bottom Line Up Front)
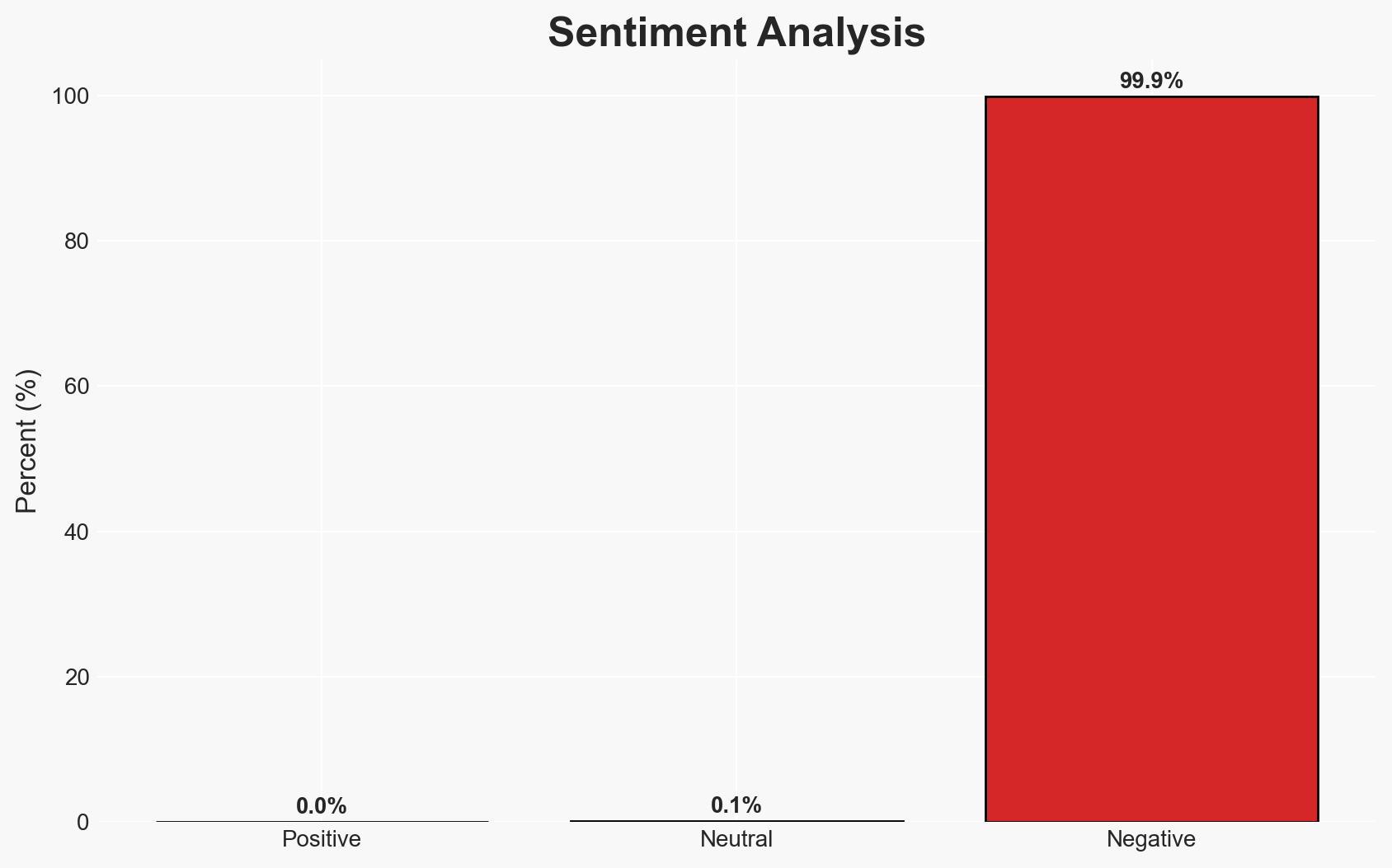
The Astaroth banking trojan is being disseminated in Brazil through a WhatsApp-based worm, leveraging the platform’s widespread use to propagate malware. This campaign, primarily affecting Brazilian users, poses significant cybersecurity risks. The most likely hypothesis is that threat actors are exploiting WhatsApp’s popularity to enhance malware distribution efficiency. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Threat actors are using WhatsApp as a deliberate strategy to exploit its widespread use in Brazil, enhancing the reach and impact of the Astaroth trojan. This is supported by the observed use of WhatsApp in multiple campaigns and the high infection rate in Brazil. However, the exact motivations and end goals of the actors remain unclear.
- Hypothesis B: The use of WhatsApp is opportunistic rather than strategic, with actors exploiting any available platform to spread malware. This is contradicted by the consistent use of WhatsApp in recent campaigns, suggesting a more targeted approach.
- Assessment: Hypothesis A is currently better supported due to the consistent pattern of WhatsApp exploitation in Brazil-focused campaigns. Indicators that could shift this judgment include evidence of similar tactics in regions where WhatsApp is less prevalent.
3. Key Assumptions and Red Flags
- Assumptions: The threat actors have a detailed understanding of WhatsApp’s API and user behavior in Brazil; the malware’s propagation relies on the high trust level among WhatsApp contacts; Brazilian cybersecurity defenses are currently insufficient to counter this tactic.
- Information Gaps: Specific identities and affiliations of the threat actors; detailed technical analysis of the malware’s components; comprehensive data on infection rates outside Brazil.
- Bias & Deception Risks: Potential over-reliance on reports from cybersecurity firms with vested interests; risk of underestimating the adaptability of threat actors to countermeasures.
4. Implications and Strategic Risks
This development could lead to increased sophistication in malware distribution tactics, influencing broader cyber threat landscapes.
- Political / Geopolitical: Potential strain on Brazil’s international cybersecurity collaborations if the threat is perceived as a national security issue.
- Security / Counter-Terrorism: Increased vulnerability of financial institutions and personal data, potentially leading to broader economic destabilization.
- Cyber / Information Space: Escalation in the use of social media platforms for malware propagation, challenging existing cybersecurity frameworks.
- Economic / Social: Potential erosion of trust in digital communication platforms, impacting social cohesion and economic transactions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of WhatsApp traffic for anomalous patterns; collaborate with WhatsApp for rapid response capabilities; initiate public awareness campaigns on phishing risks.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced threat detection technologies; strengthen legal frameworks for cybercrime prosecution.
- Scenario Outlook:
- Best: Effective countermeasures reduce malware spread significantly.
- Worst: Malware evolves, bypassing current defenses and causing widespread financial damage.
- Most-Likely: Continued low-level infections with periodic spikes as new tactics are tested.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
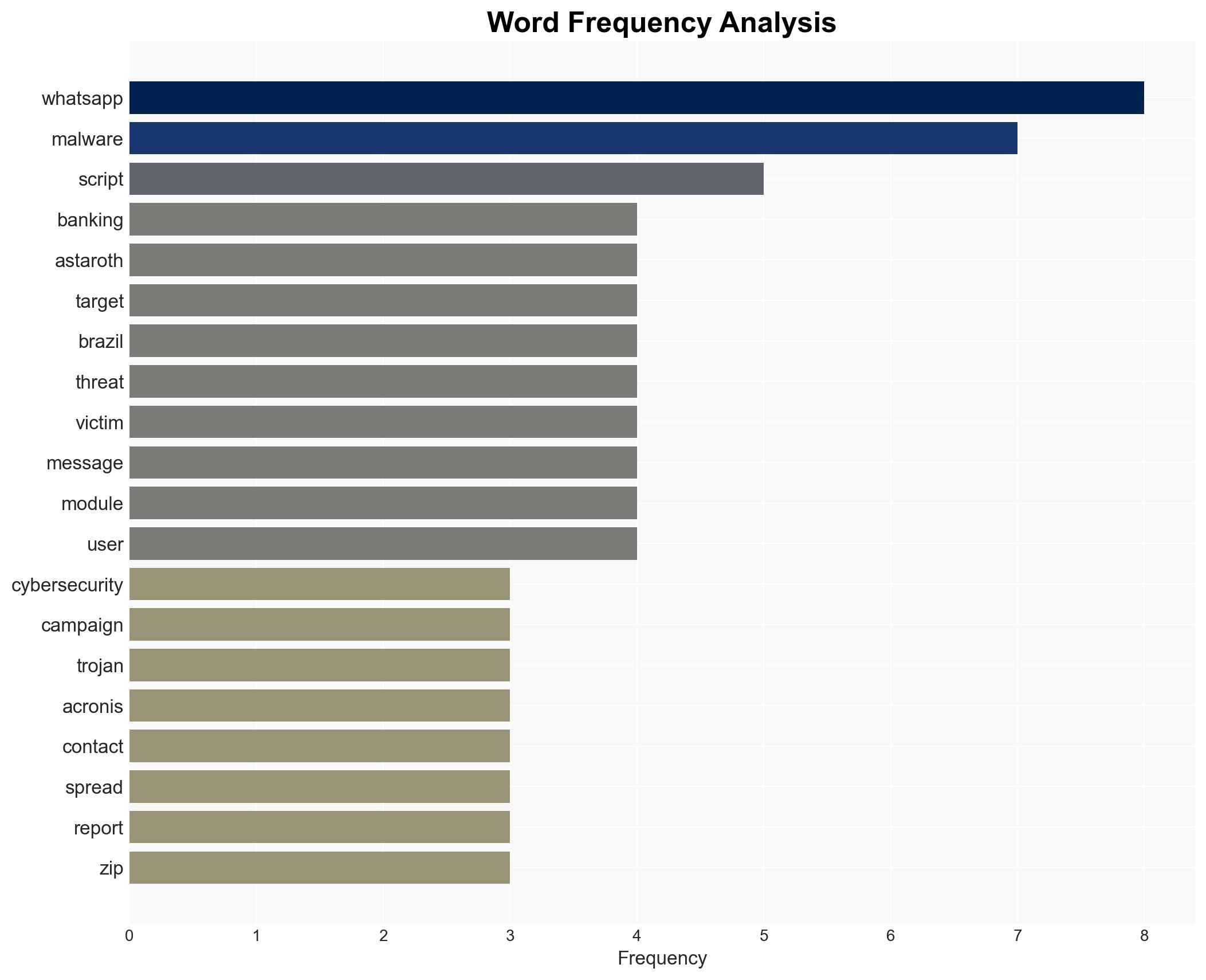
cybersecurity, malware, Brazil, WhatsApp, banking trojan, cyber threat, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us