When IT fails OT pays the price – Help Net Security
Published on: 2025-11-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
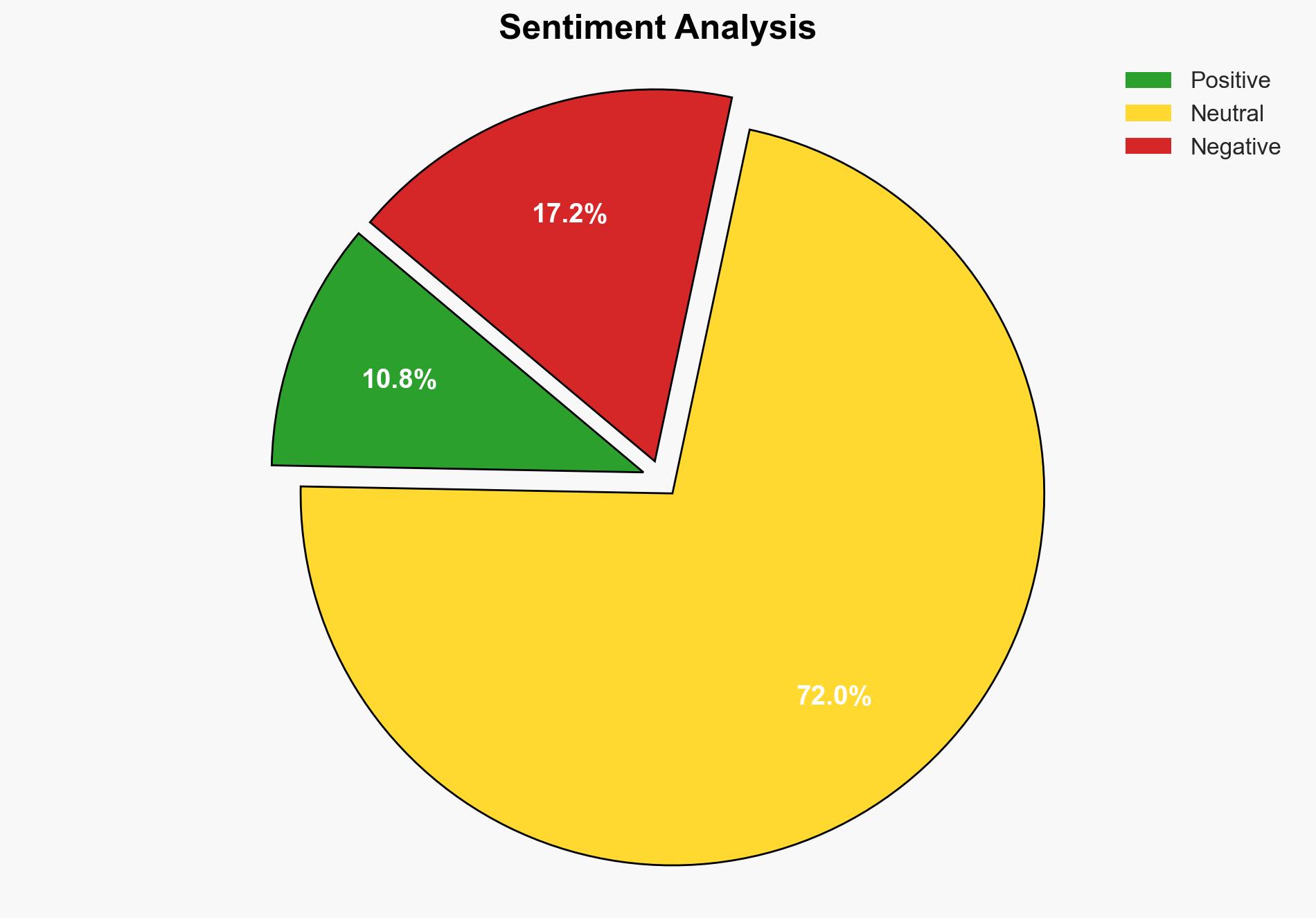
With a moderate confidence level, the most supported hypothesis is that cybercriminal and state-sponsored groups are increasingly targeting Operational Technology (OT) systems due to their critical role in industrial processes and the potential for significant disruption. Recommended actions include enhancing OT security measures, improving cross-sector collaboration, and investing in advanced threat detection capabilities.
2. Competing Hypotheses
Hypothesis 1: Cybercriminal and state-sponsored groups are targeting OT systems primarily for financial gain through extortion and ransomware, exploiting weak segmentation and integration with IT systems.
Hypothesis 2: These groups are targeting OT systems as part of broader geopolitical strategies, aiming to disrupt critical infrastructure and exert political pressure.
Hypothesis 1 is more likely due to the observed pattern of ransomware attacks and financial motives. However, the geopolitical context and involvement of state-sponsored actors lend some credibility to Hypothesis 2.
3. Key Assumptions and Red Flags
Assumptions include the continued vulnerability of OT systems due to integration with IT networks and insufficient security measures. A red flag is the potential underestimation of state-sponsored actors’ strategic objectives beyond financial motives. Deception indicators include the use of legitimate traffic blending techniques, which may obscure true intentions.
4. Implications and Strategic Risks
The targeting of OT systems poses significant risks, including operational disruptions in critical sectors like energy, transportation, and manufacturing. Escalation scenarios could involve increased geopolitical tensions, economic instability due to prolonged disruptions, and potential retaliatory cyber operations. The convergence of IT and OT vulnerabilities amplifies these risks.
5. Recommendations and Outlook
- Enhance OT security by implementing robust segmentation and access controls.
- Foster cross-sector collaboration to share threat intelligence and best practices.
- Invest in advanced threat detection and response capabilities tailored to OT environments.
- Best-case scenario: Improved defenses reduce successful attacks, minimizing disruption.
- Worst-case scenario: A coordinated attack leads to widespread infrastructure failures and geopolitical conflict.
- Most-likely scenario: Continued sporadic attacks with varying degrees of success, prompting incremental security improvements.
6. Key Individuals and Entities
Entities involved include Sandworm, TEMP.Veles, and Qilin Group, known for their roles in cyber operations targeting OT systems.
7. Thematic Tags
Cybersecurity, Operational Technology, Ransomware, Geopolitical Conflict
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us