Wired Suffers Data Breach, Exposing 2.4 Million Accounts Amid Wider Condé Nast Security Incident
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Welp Wired got hackedand 24 million accounts are affected
1. BLUF (Bottom Line Up Front)
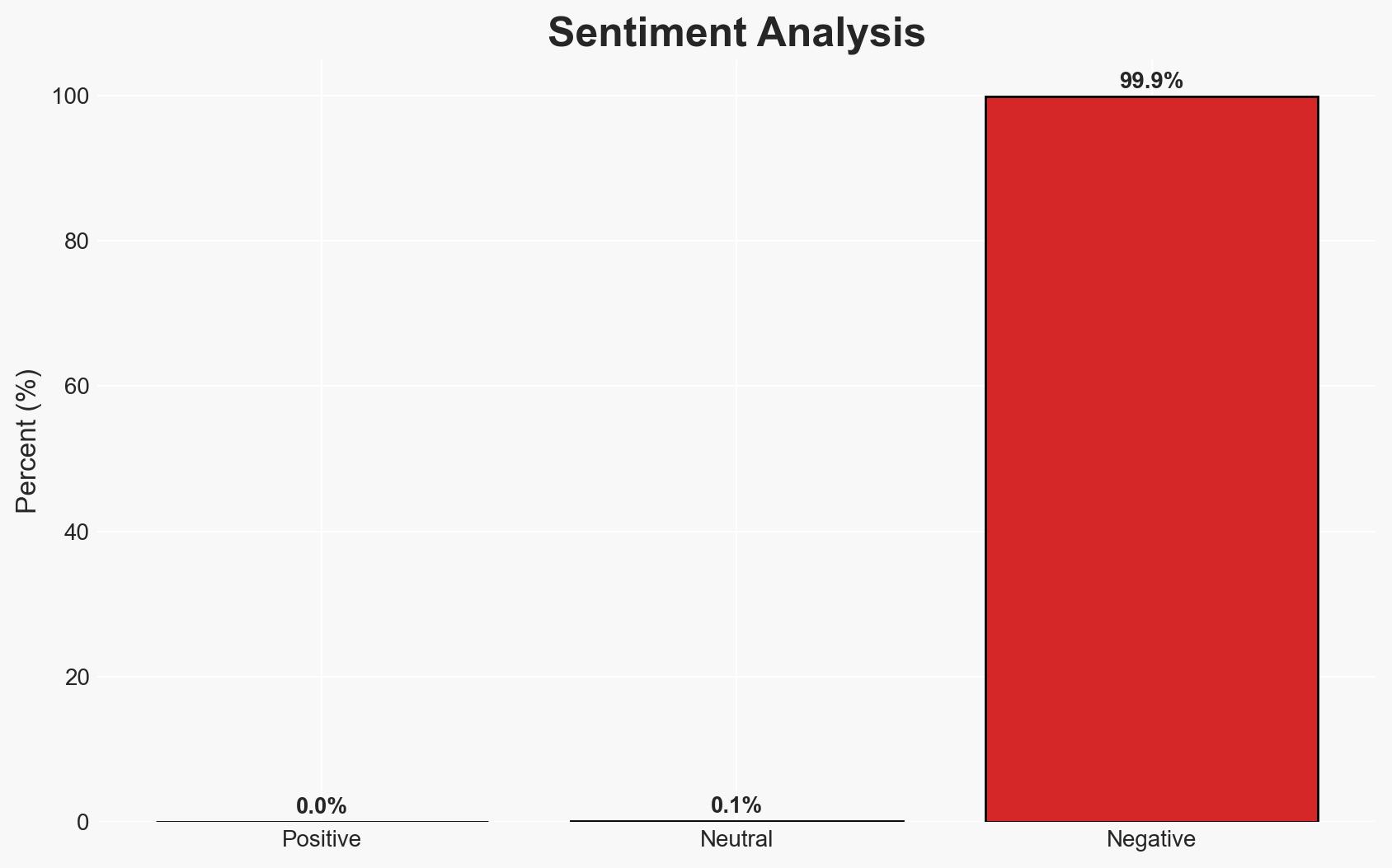
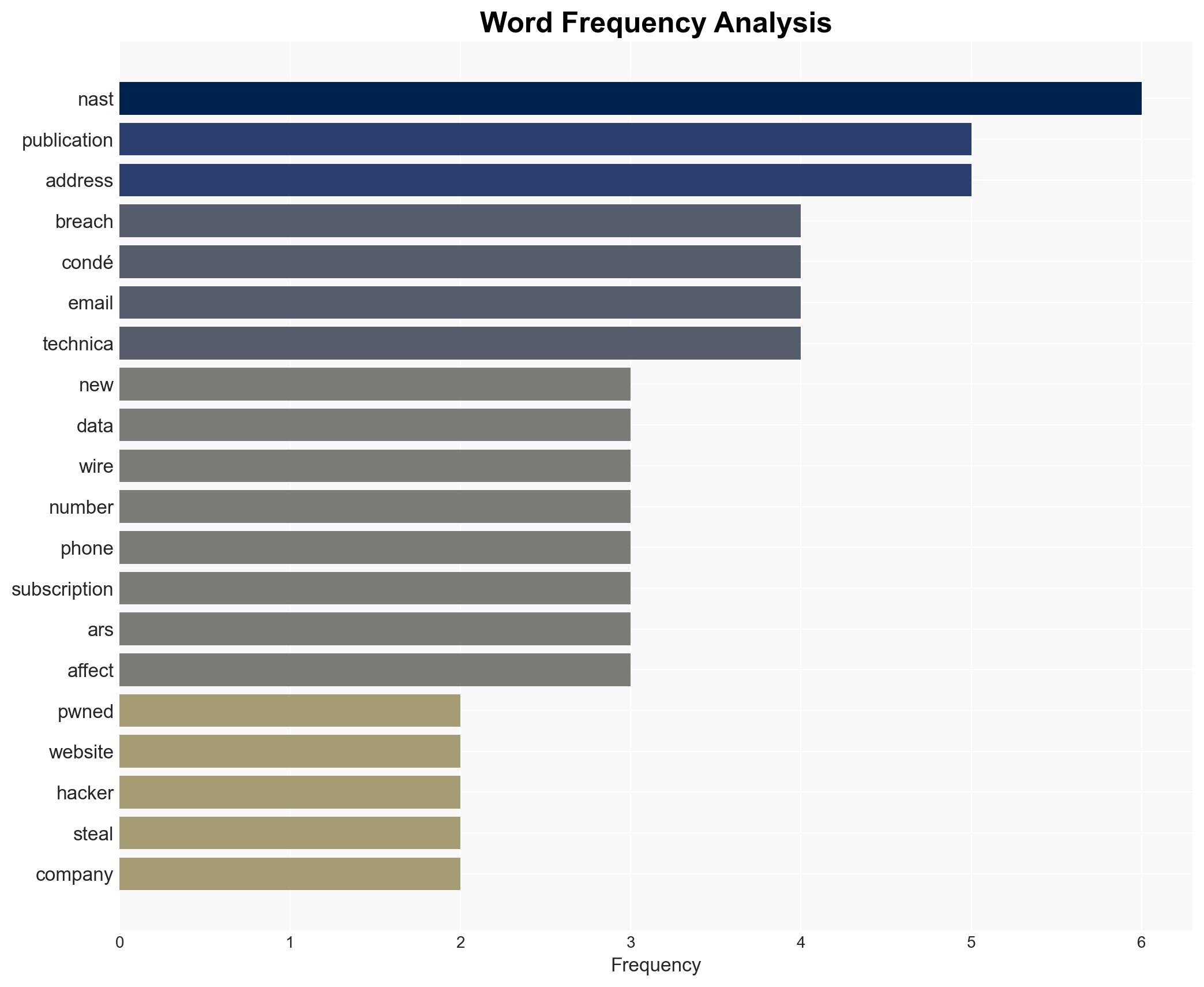
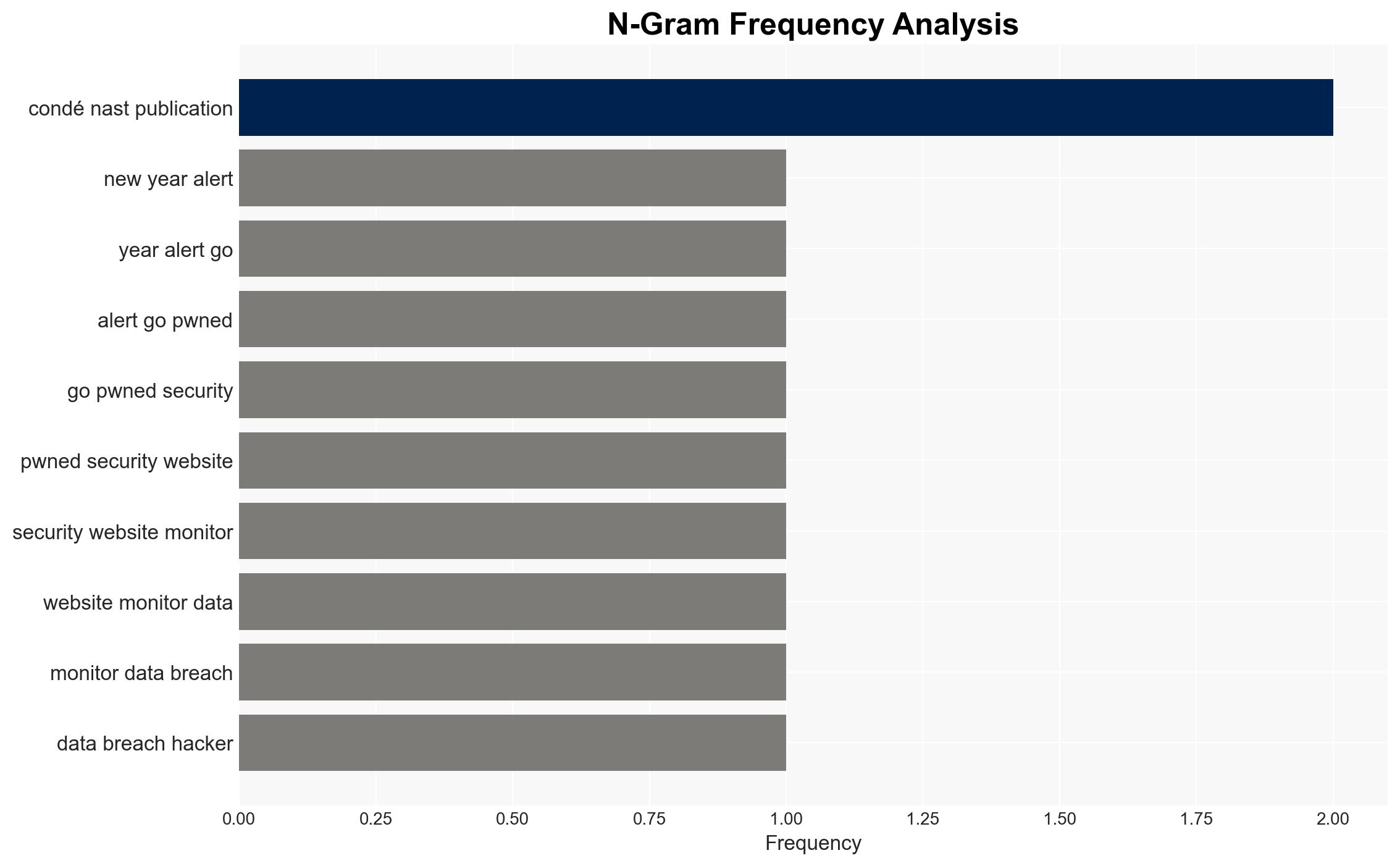
A data breach involving Wired, a Condé Nast publication, has compromised 2.4 million accounts, with additional claims of 40 million records from other Condé Nast publications. The breach may lead to increased phishing risks for affected users. The most likely hypothesis is that the breach was facilitated through vulnerabilities in Condé Nast’s systems. Overall confidence in this assessment is moderate due to limited technical details on the breach’s execution.
2. Competing Hypotheses
- Hypothesis A: The breach occurred due to a vulnerability within Condé Nast’s centralized data systems. Supporting evidence includes the hacker’s claim of accessing multiple publication records. Key uncertainties involve the specific vulnerability exploited.
- Hypothesis B: The breach was isolated to Wired and was not due to a systemic vulnerability. Ars Technica’s separate tech stack suggests potential compartmentalization. However, the hacker’s claim of accessing multiple records contradicts this.
- Assessment: Hypothesis A is currently better supported due to the hacker’s claim of accessing multiple records across Condé Nast publications. Confirmation of specific vulnerabilities or breaches in other publications could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The hacker’s claims are accurate; Condé Nast’s systems have centralized vulnerabilities; the breach data is genuine and not fabricated.
- Information Gaps: Specific technical details of the breach; confirmation of affected systems across other publications; hacker’s identity and motivations.
- Bias & Deception Risks: Potential exaggeration by the hacker to inflate perceived impact; reliance on public statements from potentially biased sources like Condé Nast.
4. Implications and Strategic Risks
This breach could lead to significant reputational damage for Condé Nast and increased scrutiny on its cybersecurity practices. The evolving threat landscape may encourage similar attacks on media companies.
- Political / Geopolitical: Limited direct implications unless state actors are involved; potential diplomatic tensions if international subscribers are affected.
- Security / Counter-Terrorism: Increased phishing and identity theft risks for affected individuals; potential exploitation by malicious actors.
- Cyber / Information Space: Highlights vulnerabilities in media cybersecurity; potential for misinformation if data is manipulated.
- Economic / Social: Trust erosion in digital subscriptions; potential financial losses for Condé Nast due to legal actions and subscriber attrition.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring for phishing campaigns; conduct a comprehensive security audit of Condé Nast’s systems; inform affected users and provide guidance on protective measures.
- Medium-Term Posture (1–12 months): Develop stronger cybersecurity partnerships; invest in advanced threat detection and response capabilities; review and update data protection policies.
- Scenario Outlook: Best: Breach contained with minimal impact; Worst: Widespread exploitation of breached data; Most-Likely: Continued phishing risks with moderate reputational damage. Triggers include discovery of further vulnerabilities or additional breaches.
6. Key Individuals and Entities
- Condé Nast
- Wired
- Ars Technica
- Have I Been Pwned
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, phishing, media industry, Condé Nast, information security, digital privacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us