WordPress plugin with over a million installs may have a worrying security flaw – here’s what we know
Published on: 2025-11-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: WordPress Plugin Security Flaw Analysis
1. BLUF (Bottom Line Up Front)
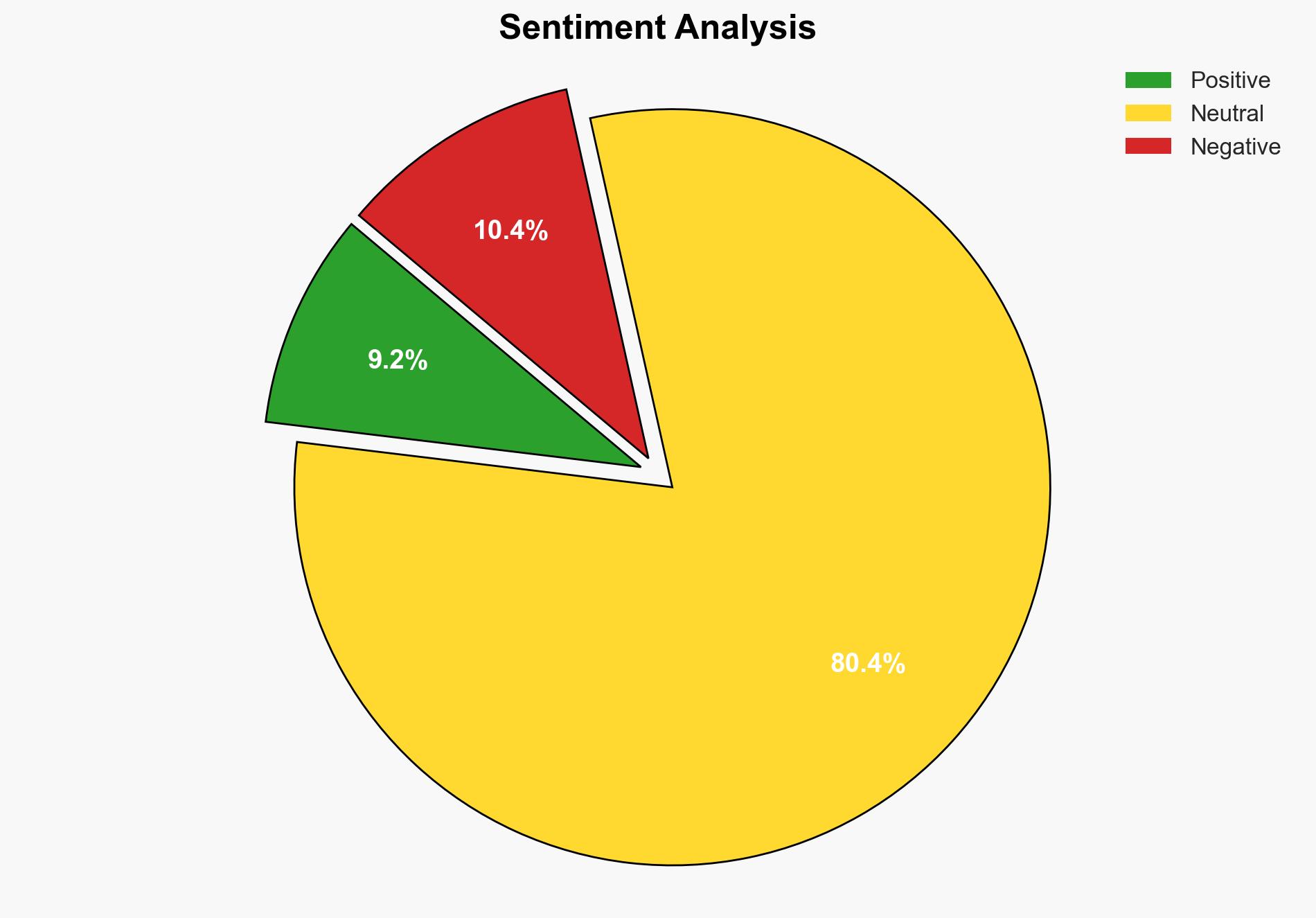
With a high confidence level, the most supported hypothesis is that the security flaw in the W3 Total Cache plugin poses a significant risk of mass exploitation if not addressed promptly. Immediate action is recommended for users to update to the latest version to mitigate potential threats.
2. Competing Hypotheses
Hypothesis 1: The security flaw in the W3 Total Cache plugin will lead to widespread exploitation due to the availability of a proof-of-concept (PoC) exploit and the high number of vulnerable installations.
Hypothesis 2: The impact of the security flaw will be minimal as most users will update their plugins before the PoC is widely used, reducing the number of vulnerable sites significantly.
Hypothesis 1 is more likely given the historical precedent of slow user response to security updates and the critical nature of the vulnerability, which allows for unauthenticated command injection.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that users will not update their plugins promptly, based on past behavior. The PoC exploit is assumed to be effective and easily accessible to threat actors.
Red Flags: The release of the PoC on November 24 is a critical date, as it may trigger increased exploitation. The reliance on user action to update plugins is a significant vulnerability.
4. Implications and Strategic Risks
The primary risk is a large-scale compromise of WordPress sites, leading to data breaches, defacement, and potential economic losses for affected businesses. Politically, this could erode trust in WordPress as a platform. Cyber risks include the potential for these compromised sites to be used in larger botnet attacks.
5. Recommendations and Outlook
- Actionable Steps: Urge all users of the W3 Total Cache plugin to update to the latest version immediately. Increase awareness through targeted communications to WordPress site administrators.
- Best Scenario: Rapid user updates lead to minimal exploitation, maintaining trust in WordPress security.
- Worst Scenario: Mass exploitation occurs, leading to significant data breaches and economic damage.
- Most-likely Scenario: Moderate exploitation occurs, with some high-profile sites affected, prompting a reactive update from remaining users.
6. Key Individuals and Entities
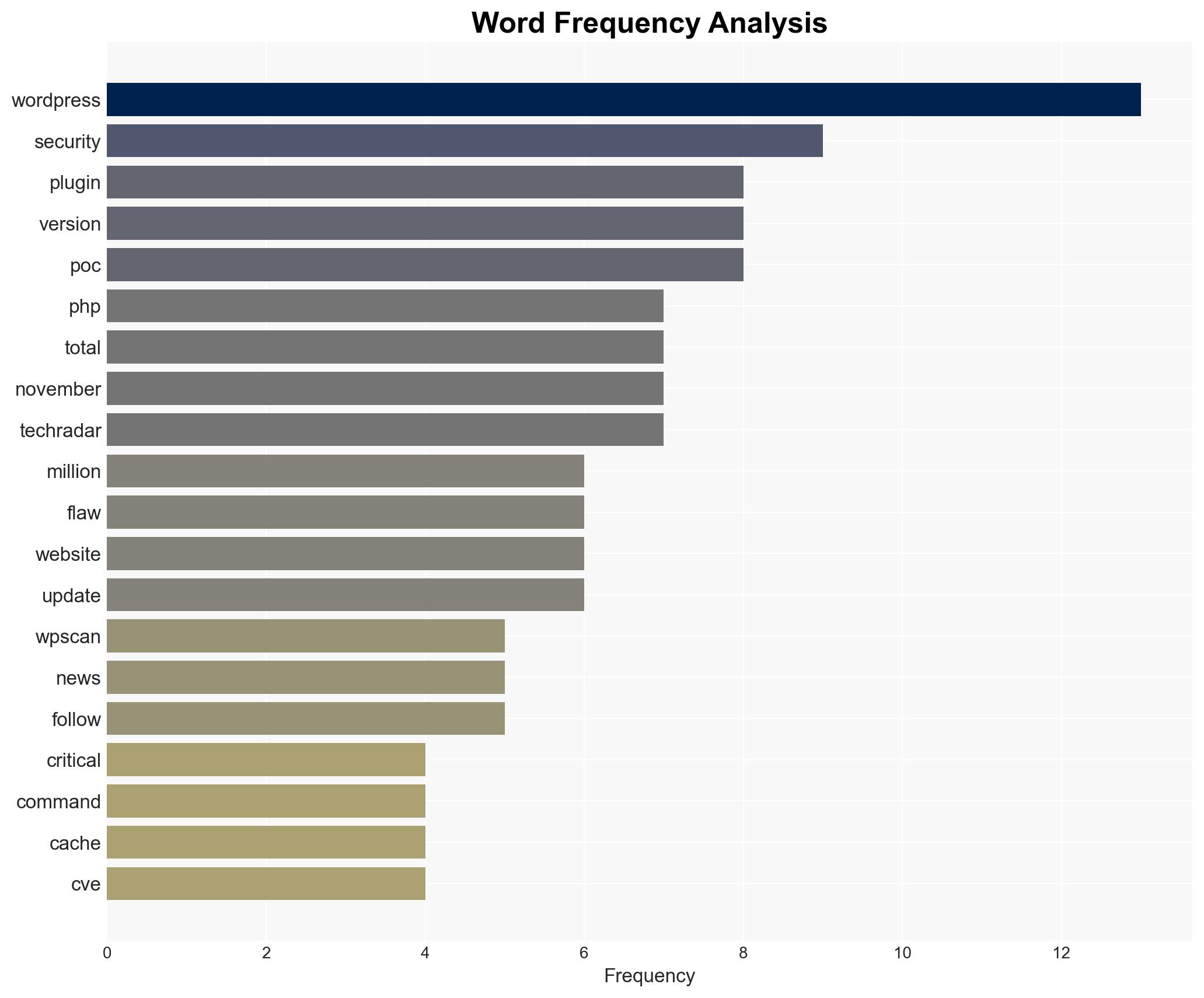
No specific individuals are identified in the source text. Key entities include WordPress, WPScan, and TechRadar.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us