World Leaks Ransomware Group Introduces New Stealth Malware RustyRocket for Enhanced Data Exfiltration
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: World Leaks Ransomware Group Adds Stealthy Custom Malware RustyRocket to Attacks
1. BLUF (Bottom Line Up Front)
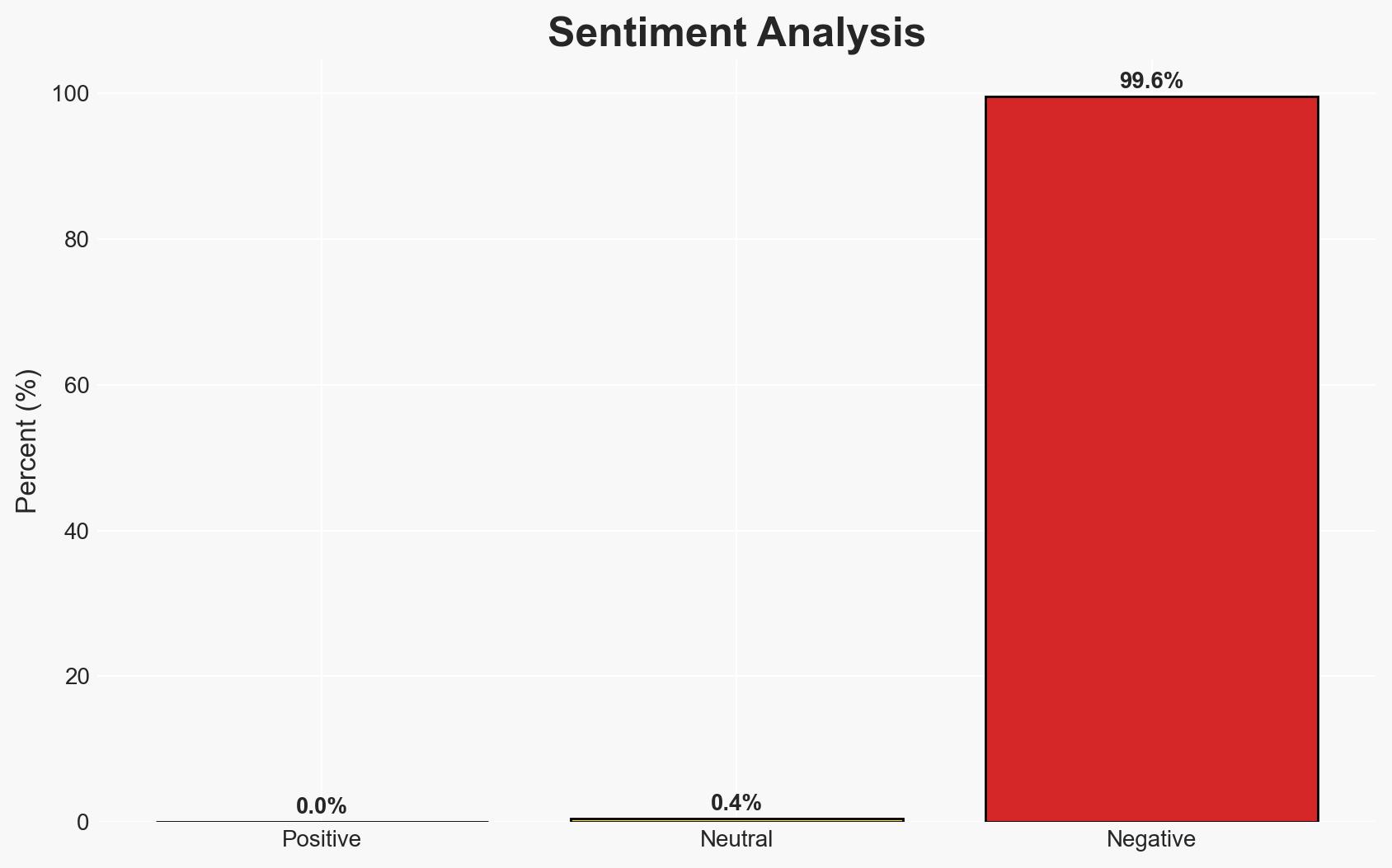
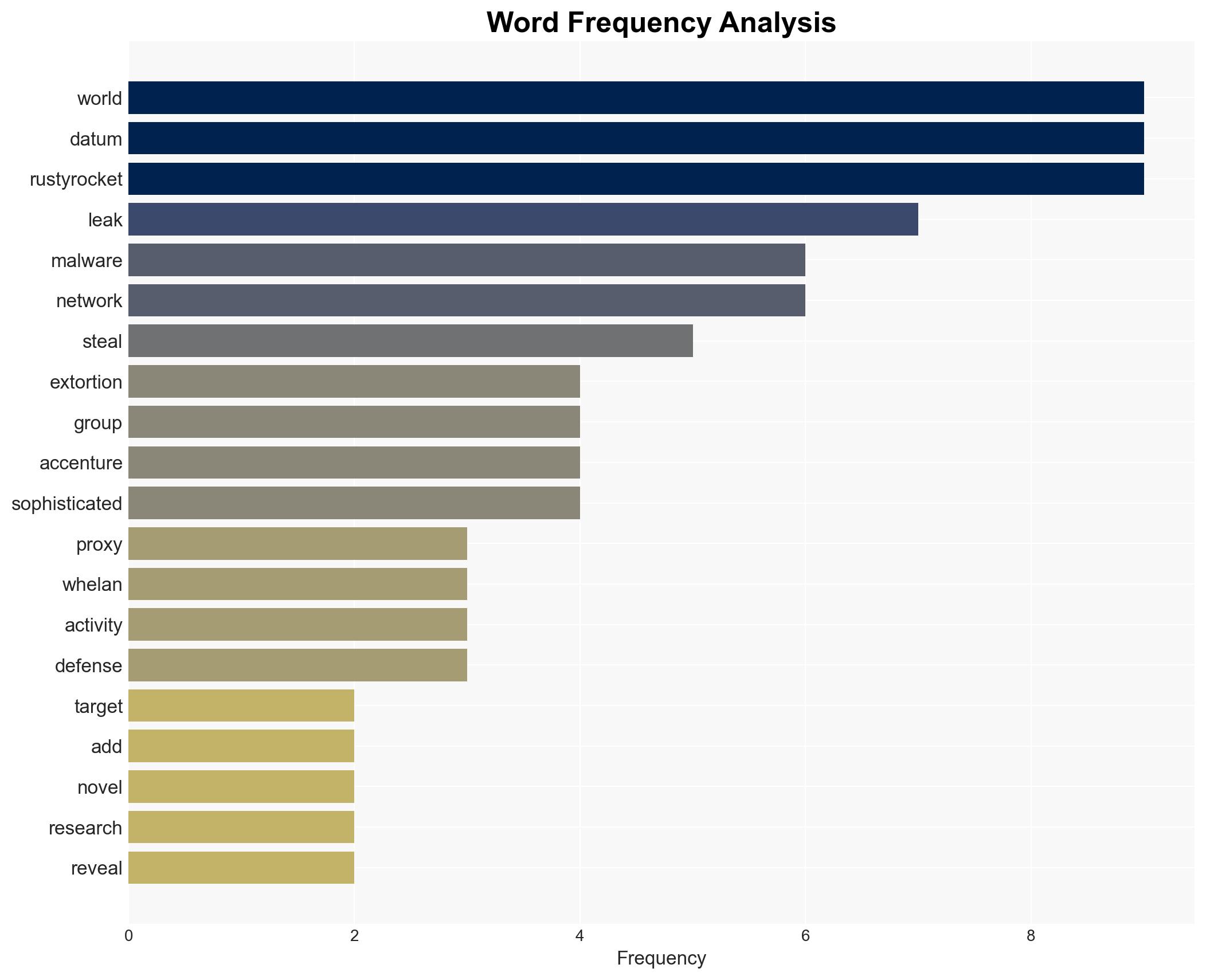
World Leaks, a cyber-criminal group, has introduced a sophisticated malware named RustyRocket, enhancing their capability to conduct stealthy data exfiltration and extortion attacks. This development poses a significant threat to organizations globally, particularly those with inadequate cyber defenses. The most likely hypothesis is that World Leaks will continue to leverage RustyRocket to target high-profile companies, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: World Leaks will primarily use RustyRocket to target large corporations for financial gain. This is supported by their history of targeting major companies like Nike and the sophisticated nature of RustyRocket, which is designed for stealthy data exfiltration. However, the specific selection criteria for targets remain unclear.
- Hypothesis B: World Leaks may diversify their targets to include smaller organizations or critical infrastructure to create broader disruption. This is less supported due to the group’s historical focus on high-profile targets and financial motives, but cannot be entirely ruled out given the malware’s capabilities.
- Assessment: Hypothesis A is currently better supported due to the group’s established pattern of targeting large corporations and the financial incentives involved. Indicators that could shift this judgment include evidence of attacks on smaller entities or infrastructure sectors.
3. Key Assumptions and Red Flags
- Assumptions: World Leaks will continue to prioritize financial extortion over other motives; RustyRocket’s capabilities are as described by Accenture; the group has the resources to maintain and deploy such sophisticated malware.
- Information Gaps: Detailed technical analysis of RustyRocket’s full capabilities; the extent of World Leaks’ operational network and affiliate structure; potential state sponsorship or external support.
- Bias & Deception Risks: Potential over-reliance on a single source (Accenture); possible exaggeration of RustyRocket’s capabilities by World Leaks to enhance their perceived threat.
4. Implications and Strategic Risks
This development could lead to increased cyber extortion incidents, affecting corporate reputations and financial stability. The stealthy nature of RustyRocket may drive organizations to invest more in advanced cybersecurity measures.
- Political / Geopolitical: Potential for increased tensions if state actors are suspected of supporting World Leaks.
- Security / Counter-Terrorism: Heightened threat environment for targeted sectors; increased demand for cybersecurity expertise.
- Cyber / Information Space: Escalation in cyber arms race; potential for copycat attacks using similar malware.
- Economic / Social: Financial losses for targeted companies; potential job losses or reputational damage leading to broader economic impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance network monitoring for signs of RustyRocket; conduct security audits and employee training on social engineering threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced threat detection and response capabilities.
- Scenario Outlook:
- Best: Successful mitigation strategies reduce World Leaks’ impact.
- Worst: Widespread adoption of RustyRocket by other groups leading to increased attacks.
- Most-Likely: Continued targeting of major corporations with incremental improvements in attack sophistication.
6. Key Individuals and Entities
- World Leaks (cyber-criminal group)
- Accenture Cybersecurity (research entity)
- T. Ryan Whelan (MD and global head of Accenture cyber intelligence)
- Nike (victim organization)
7. Thematic Tags
cybersecurity, ransomware, data exfiltration, cyber extortion, malware, threat intelligence, corporate security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us