You too can run malware from NPM I mean without consequences – Github.com
Published on: 2025-09-09
Intelligence Report: You too can run malware from NPM I mean without consequences – Github.com
1. BLUF (Bottom Line Up Front)
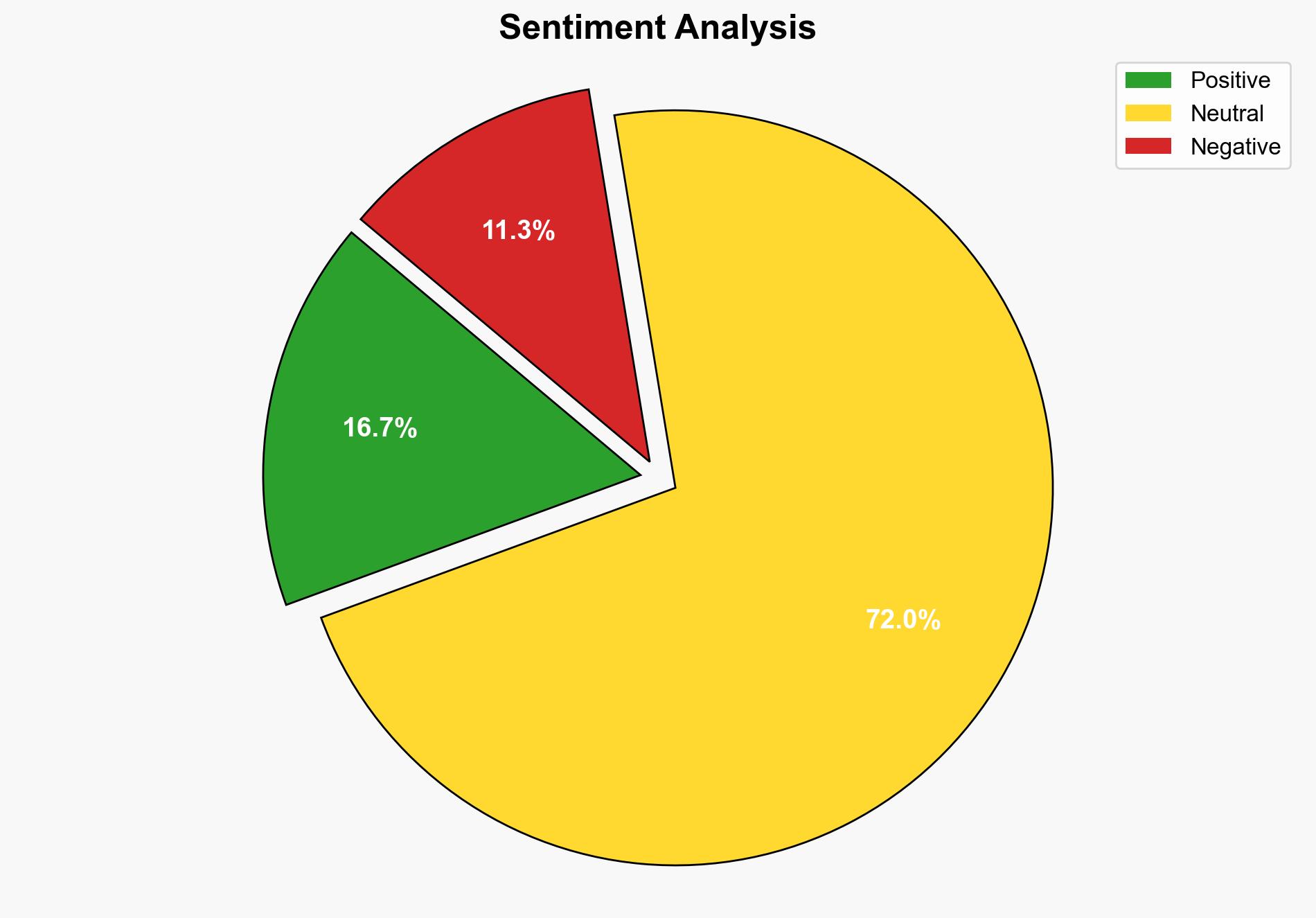
The analysis suggests a moderate confidence level that the primary motivation behind the malware in the NPM package is either a low-impact financial gain or a proof-of-concept demonstration. The most supported hypothesis is that this is a demonstration of vulnerability in the software supply chain rather than a sophisticated financial attack. Recommended action includes enhancing monitoring of software dependencies and educating developers on secure coding practices.
2. Competing Hypotheses
1. **Hypothesis 1**: The malware is a proof-of-concept to demonstrate vulnerabilities in the software supply chain, aiming to raise awareness rather than cause significant harm.
2. **Hypothesis 2**: The malware is designed for financial gain through redirecting cryptocurrency transactions, albeit with low sophistication and impact.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the low impact and apparent mocking tone of the malware author, suggesting an intent to highlight security flaws rather than execute a high-stakes financial attack.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the malware’s low impact is intentional and not due to technical limitations. The analysis assumes that the author’s intent can be inferred from the tone and impact of the malware.
– **Red Flags**: The lack of detailed information on the malware’s distribution and the author’s identity raises questions. The mocking tone could be a deception tactic to downplay the threat.
4. Implications and Strategic Risks
The incident underscores the vulnerability of software supply chains, which could be exploited for more severe attacks in the future. There is a risk of cascading threats if similar vulnerabilities are not addressed, potentially affecting economic and cybersecurity domains. The psychological impact on developers and organizations could lead to increased caution or paranoia regarding open-source dependencies.
5. Recommendations and Outlook
- Implement stricter monitoring and validation of third-party packages in software projects.
- Educate developers on identifying and mitigating supply chain vulnerabilities.
- Scenario Projections:
- **Best Case**: Increased awareness leads to improved security practices and reduced vulnerabilities.
- **Worst Case**: A more sophisticated actor exploits similar vulnerabilities for significant financial or data theft.
- **Most Likely**: Continued low-impact incidents that gradually improve awareness and security measures.
6. Key Individuals and Entities
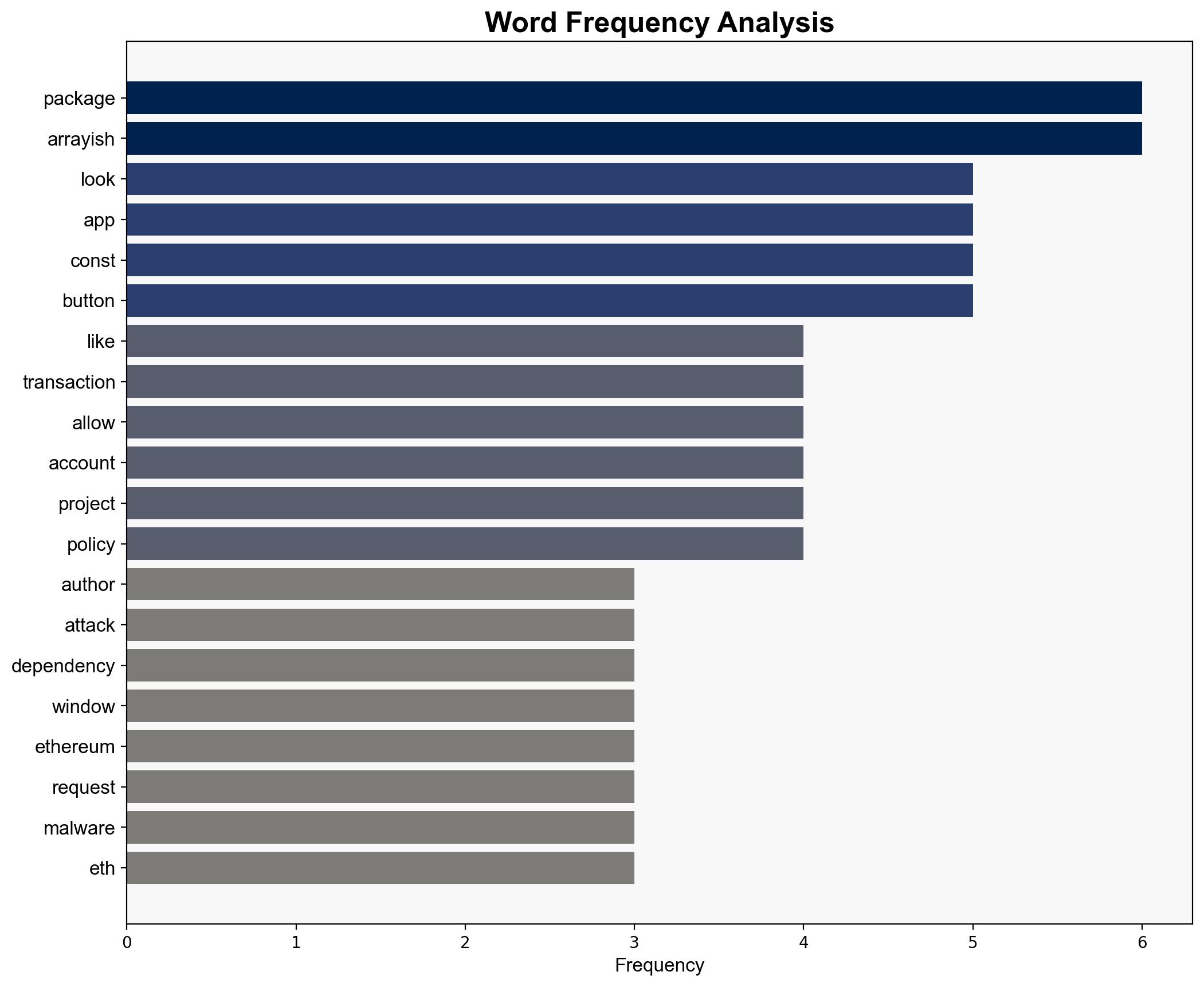
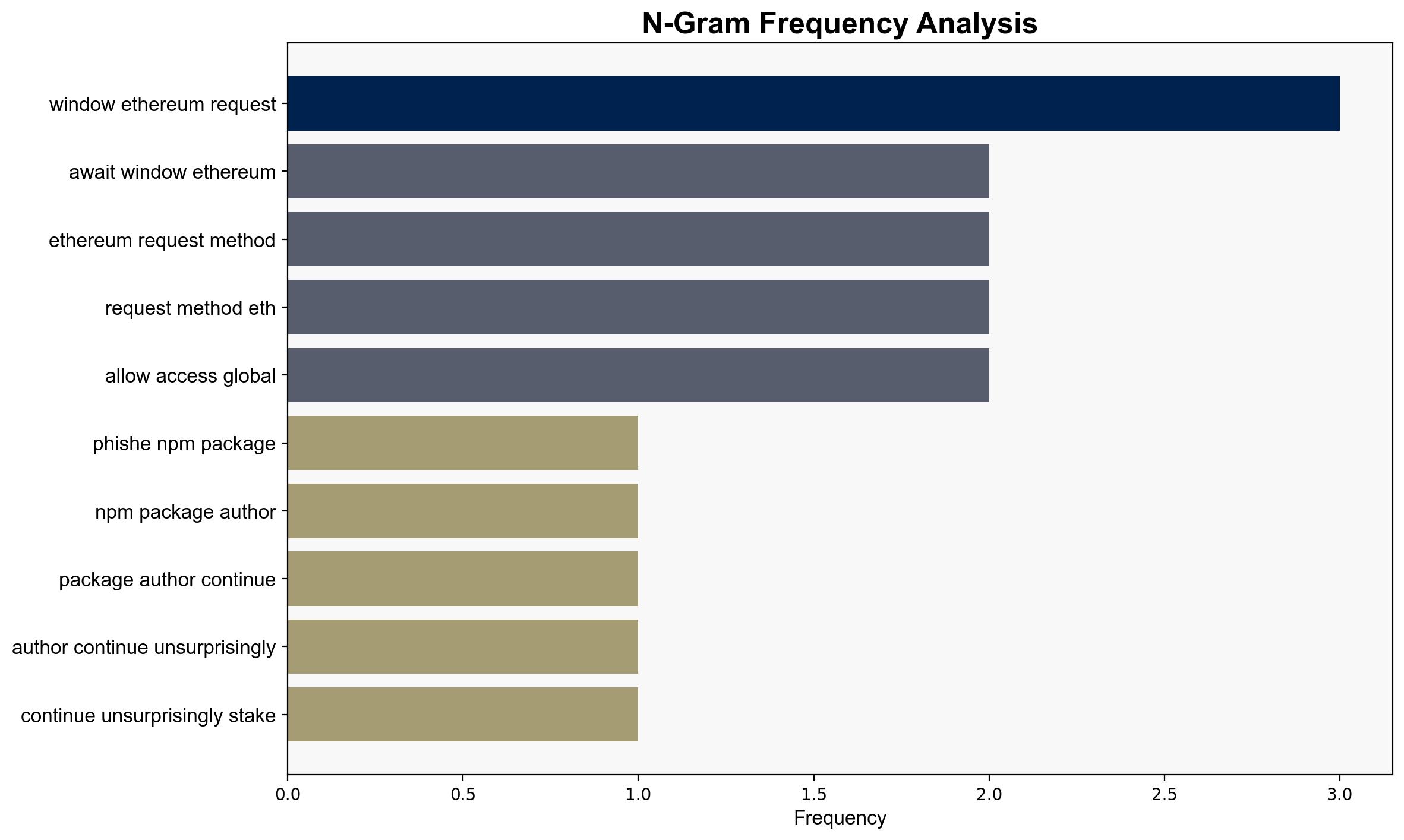
No specific individuals are identified in the source material. The entity involved is the NPM package ecosystem, particularly the “arrayish” package.
7. Thematic Tags
national security threats, cybersecurity, software supply chain, vulnerability awareness