ZDI Drops 13 Unpatched Ivanti Endpoint Manager Vulnerabilities – Securityweek.com
Published on: 2025-10-10
Intelligence Report: ZDI Drops 13 Unpatched Ivanti Endpoint Manager Vulnerabilities – Securityweek.com
1. BLUF (Bottom Line Up Front)
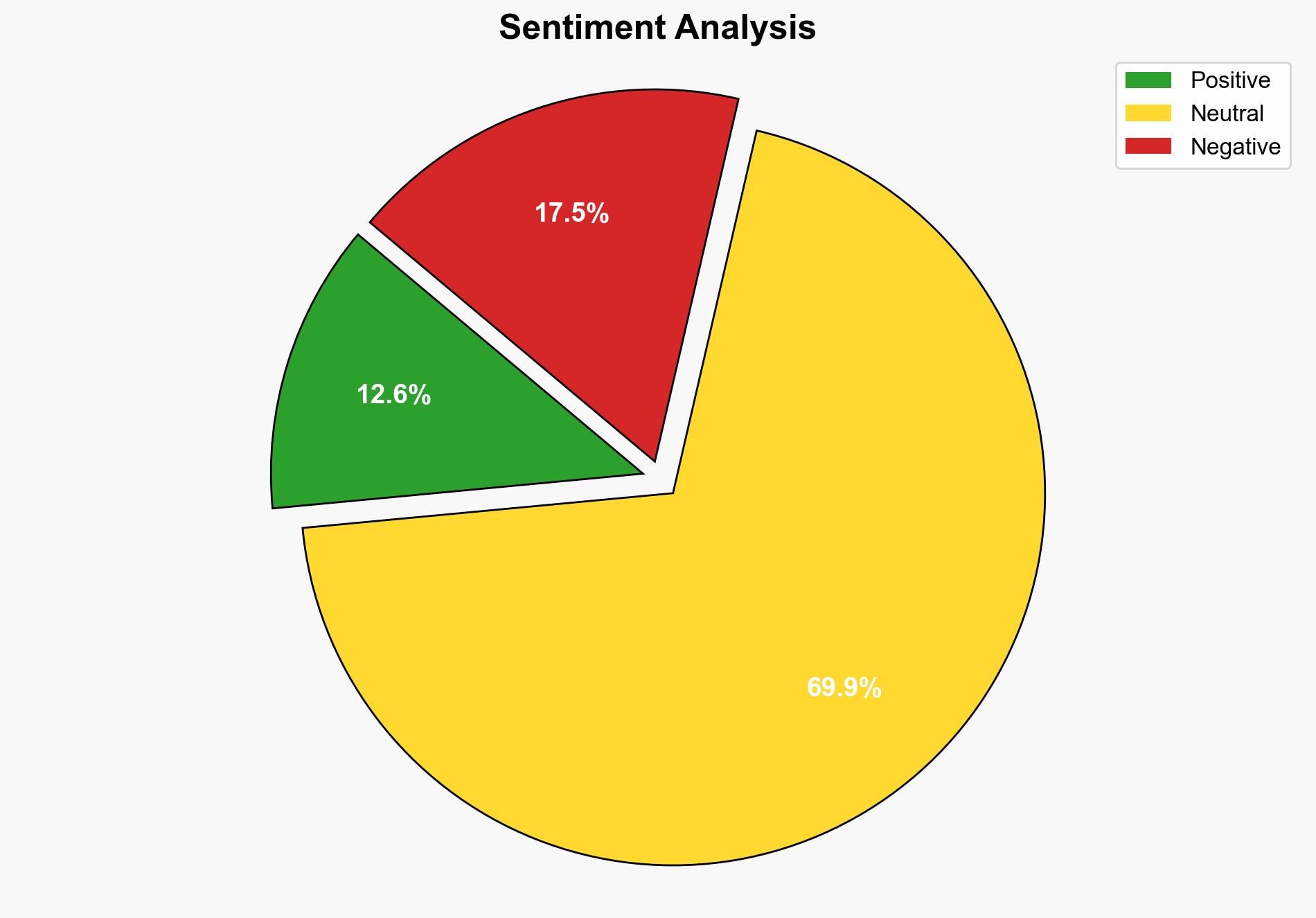
The most supported hypothesis is that Ivanti’s vulnerabilities pose a significant risk due to their potential exploitation by sophisticated threat actors, despite the company’s claims of difficulty in exploitation. The confidence level in this assessment is moderate, given the lack of direct evidence of exploitation in the wild but the high severity of the vulnerabilities. It is recommended to prioritize patching and enhance monitoring of systems using Ivanti products.
2. Competing Hypotheses
1. **Hypothesis A**: The vulnerabilities in Ivanti Endpoint Manager are highly exploitable and pose an immediate threat to organizations, particularly in critical sectors, due to their high CVSS scores and the nature of the flaws.
2. **Hypothesis B**: The vulnerabilities, while technically severe, are difficult to exploit in practice, as suggested by Ivanti, and therefore do not pose an immediate threat.
Using ACH 2.0, Hypothesis A is better supported due to the high severity ratings and the history of similar vulnerabilities being exploited by advanced threat actors. Hypothesis B is weakened by Ivanti’s delayed response and the lack of immediate patching, which suggests potential underestimation of the threat.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes that threat actors have the capability and intent to exploit these vulnerabilities. Hypothesis B assumes that Ivanti’s assessment of exploitation difficulty is accurate.
– **Red Flags**: Ivanti’s delayed response and request for patching extensions may indicate resource constraints or underestimation of the threat. The absence of reported exploitation does not guarantee safety, as sophisticated actors may exploit vulnerabilities without immediate detection.
4. Implications and Strategic Risks
The vulnerabilities could lead to significant data breaches or disruptions, especially in sectors critical to national security. If exploited, they could facilitate espionage or cyber-attacks by state-sponsored actors, notably those with a history of targeting similar vulnerabilities. The economic impact could be substantial, affecting both Ivanti and its clients, potentially leading to loss of trust and financial penalties.
5. Recommendations and Outlook
- **Immediate Actions**: Urgently apply available patches and implement temporary mitigations as recommended by ZDI and cybersecurity experts.
- **Monitoring**: Increase monitoring for signs of exploitation and unusual activity related to Ivanti products.
- **Scenario Projections**:
– **Best Case**: Rapid patching and no exploitation occur, maintaining system integrity.
– **Worst Case**: Widespread exploitation leads to significant breaches and operational disruptions.
– **Most Likely**: Some exploitation occurs, but is contained through effective monitoring and response.
6. Key Individuals and Entities
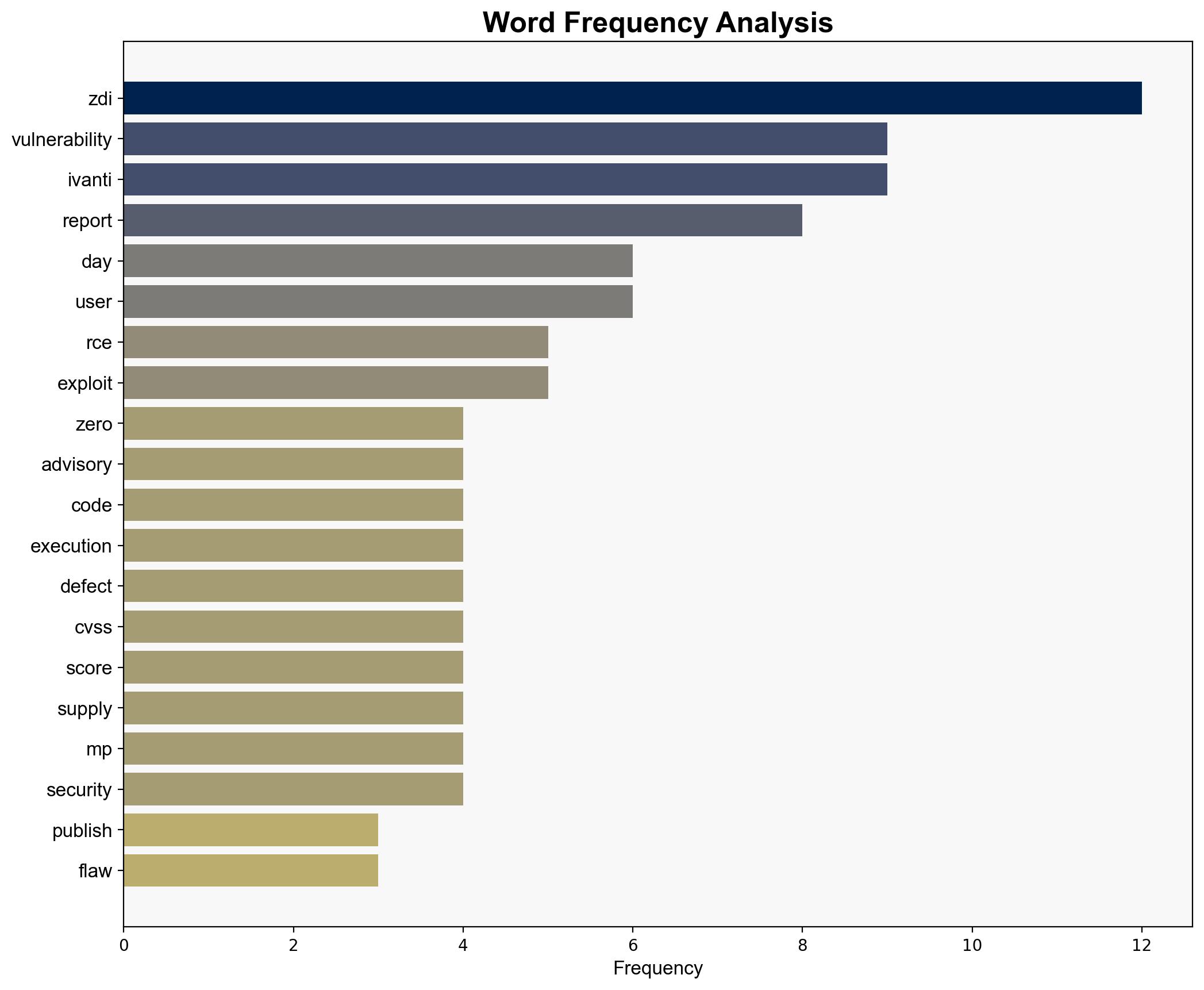
– Ivanti
– Trend Micro’s Zero Day Initiative (ZDI)
– Potential state-sponsored actors (e.g., Chinese espionage groups)
7. Thematic Tags
national security threats, cybersecurity, vulnerability management, critical infrastructure protection